Doctor Web’s January 2024 review of virus activity on mobile devices
March 29, 2024
The number of attacks carried out by various banking trojan families increased by 17.04%, Android.Spy spyware trojan attacks increased by 11.16%, and Android.Locker ransomware attacks increased by an insignificant 0.92%.
At the same time, our specialists uncovered more threats on Google Play, including a new family of unwanted adware modules dubbed Adware.StrawAd and new trojans from the Android.FakeApp family. Malicious actors use the latter to execute various fraudulent schemes.
PRINCIPAL TRENDS IN JANUARY
- Adware trojans from the Android.HiddenAds family maintained their lead in terms of the number of times they were detected on protected devices
- Many Android malware families became more active
- More threats were discovered on Google Play
According to statistics collected by Dr.Web for Android
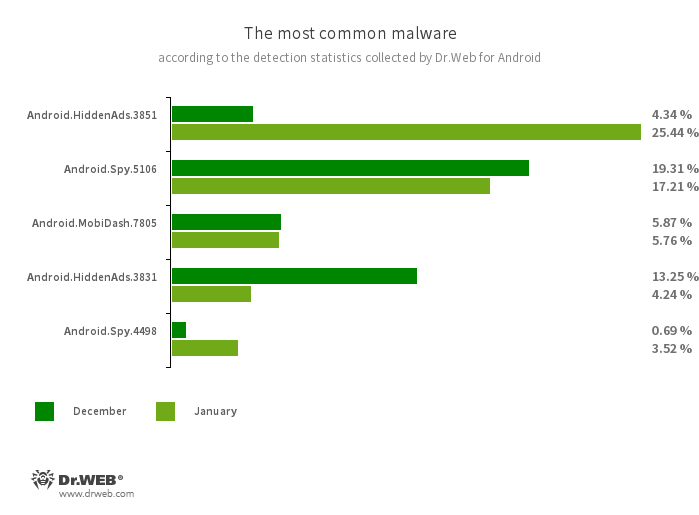
- Android.HiddenAds.3851
- Android.HiddenAds.3831
- Trojan apps designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Spy.5106
- Android.Spy.4498
- The detection name for a trojan that presents itself as modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes containing remotely configurable content.
- Android.MobiDash.7805
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
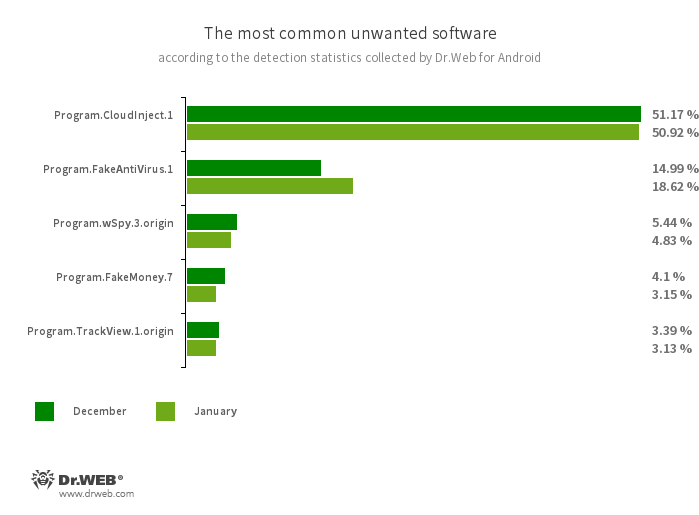
- Program.CloudInject.1
- The detection name for Android programs that have been modified using the CloudInject cloud service and the eponymous Android utility (the latter was added to the Dr.Web virus database as Tool.CloudInject). Such programs are modified on a remote server; meanwhile, the modders (users) who are interested in such modifications cannot control exactly what will be added to the apps. Moreover, these programs receive a number of dangerous system permissions. Once modification is complete, users can remotely manage these apps. They can block them, display custom dialogs, and track when other software is being installed or removed from a device, etc.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.wSpy.3.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to the phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. It also has keylogger functionality.
- Program.FakeMoney.7
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.TrackView.1.origin
- The detection name for a program that allows users to be monitored via their Android devices. Malicious actors can utilize it to track a target device’s location, use the camera to record video and take photos, eavesdrop via the microphone, record audio, etc.
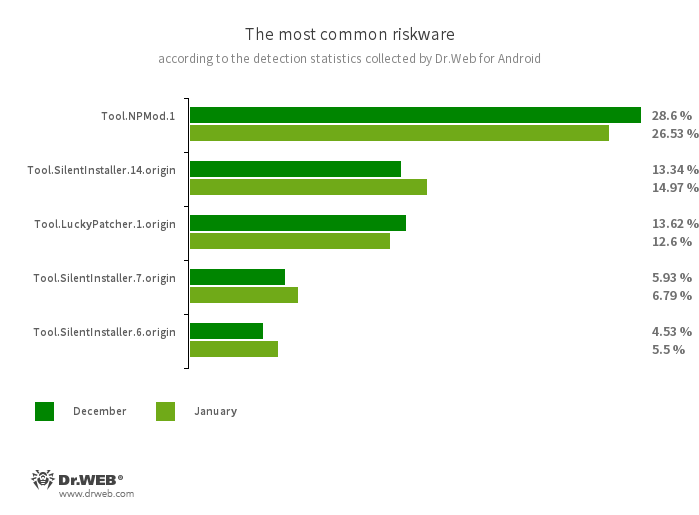
- Tool.NPMod.1
- The detection name for Android programs that have been modified using the NP Manager utility. A special module is embedded in such apps, and it allows them to bypass digital signature verification once they have been modified.
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.6.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment in the context of the apps in which they are integrated. The APK files, launched with the help of these platforms, can operate as if they are part of such programs and can also obtain the same permissions.
- Tool.LuckyPatcher.1.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root-access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads specially prepared scripts from the Internet, which can be crafted and added to the common database by any third party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
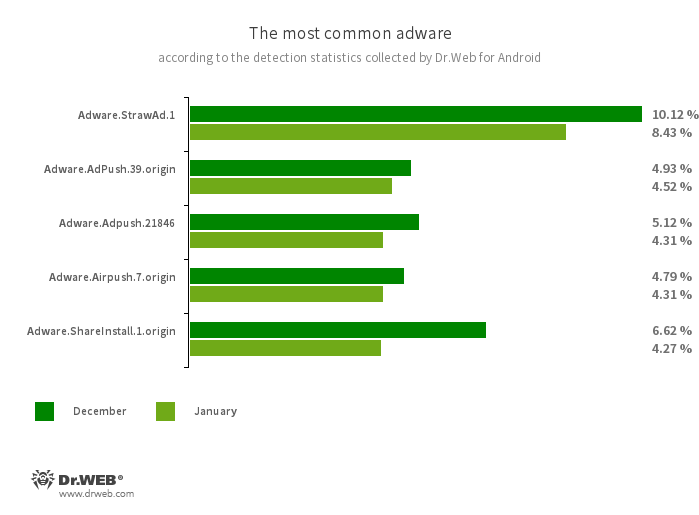
- Adware.StrawAd.1
- The detection name for Android programs containing the built-in Adware.StrawAd.1.origin unwanted adware module. This module displays ads from various advertising service providers when Android device screens are unlocked.
- Adware.AdPush.39.origin
- Adware.Adpush.21846
- Adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, these modules collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.Airpush.7.origin
- A member of a family of adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.ShareInstall.1.origin
- An adware module that can be built into Android applications. It displays notifications containing ads on the Android OS lock screen.
Threats on Google Play
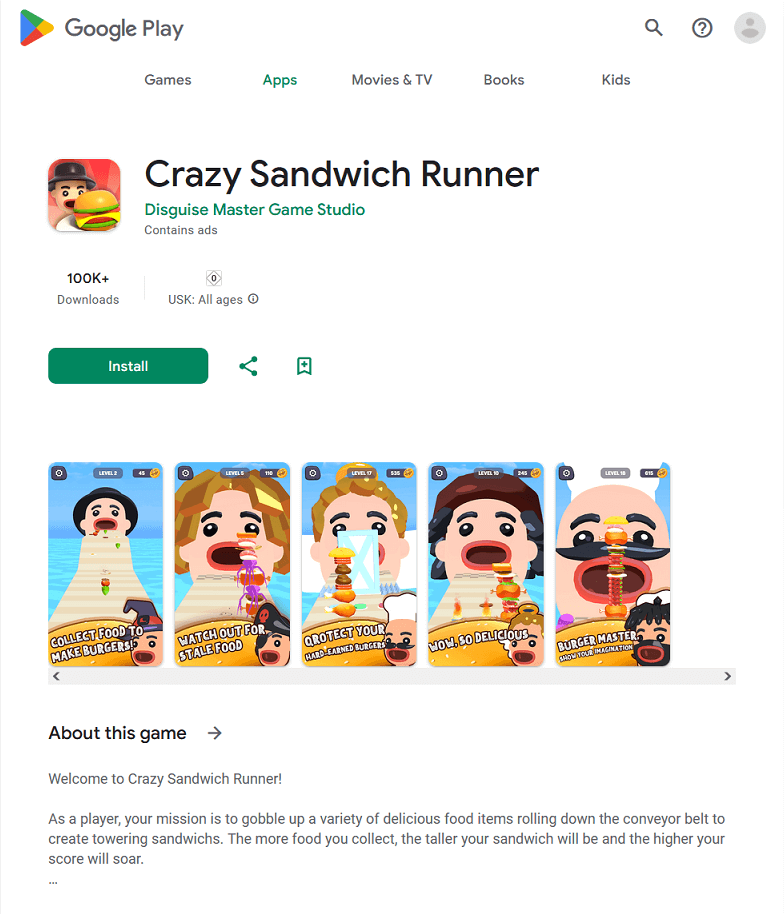
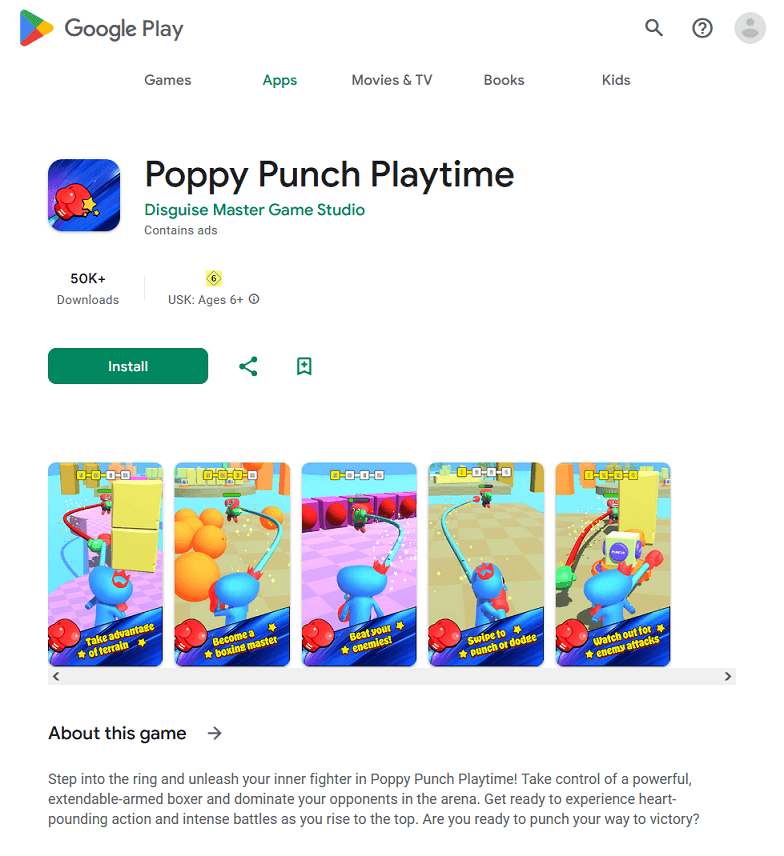
At the beginning of January 2024, Doctor Web’s virus laboratory tracked down a number of games on Google Play containing the built-in Adware.StrawAd.1.origin unwanted adware platform:
- Crazy Sandwich Runner
- Purple Shaker Master
- Poppy Punch Playtime, Meme Cat Killer
- Toiletmon Camera Playtime
- Finger Heart Matching
- Toilet Monster Defense
- Toilet Camera Battle
- Toimon Battle Playground
This platform is a specialized encrypted software module that is stored in the resource directory of the host applications. When an Android device’s screen is unlocked, it can display ads coming from a variety of advertising service providers. Dr.Web anti-virus detects apps containing Adware.StrawAd.1.origin as members of the Adware.StrawAd family.
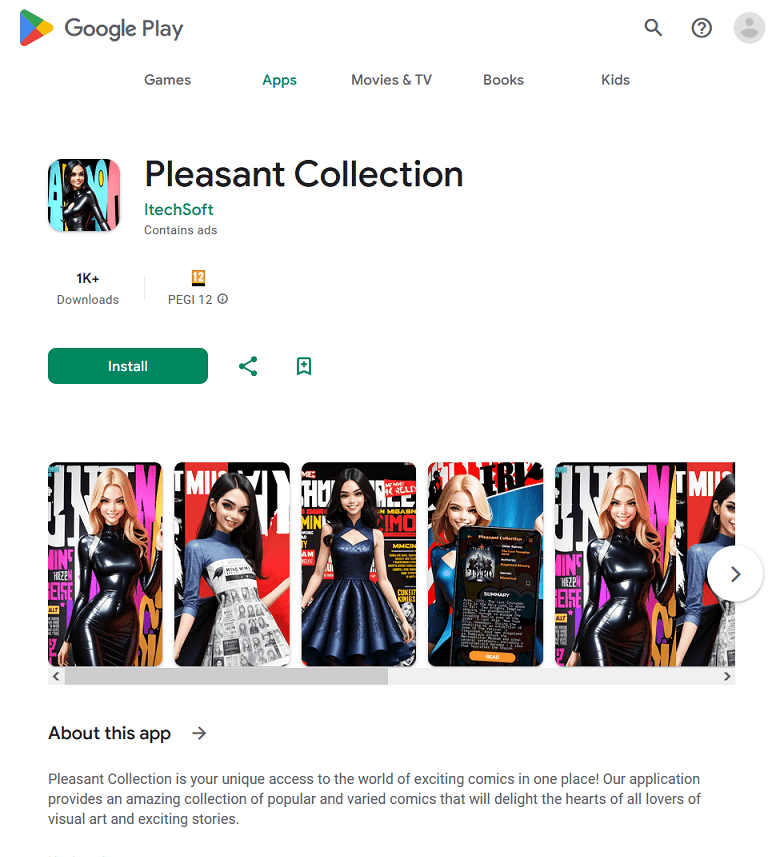
During January, our specialists also discovered a number of malicious fake programs from the Android.FakeApp family. For example, the Android.FakeApp.1579 trojan was concealed in the Pleasant Collection app, which masqueraded as a program that lets users read comics.
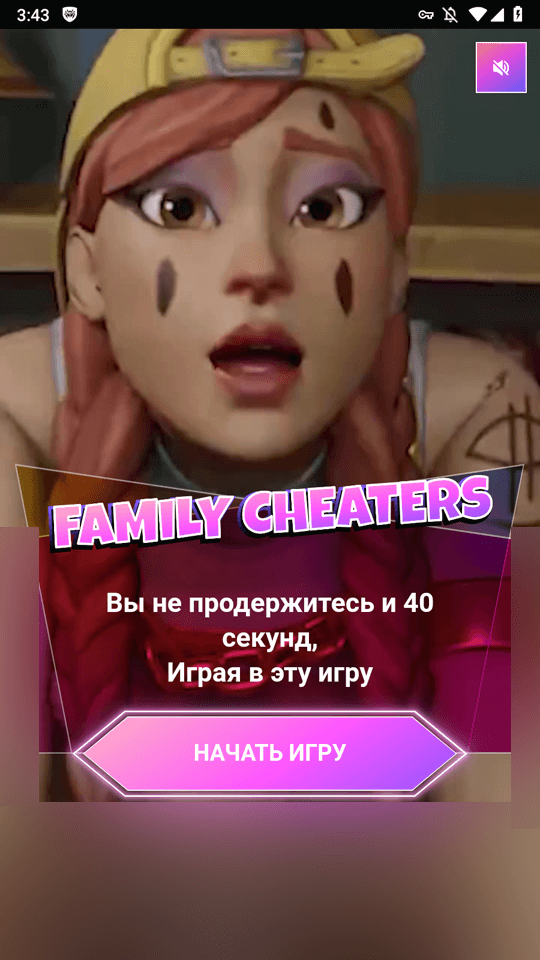
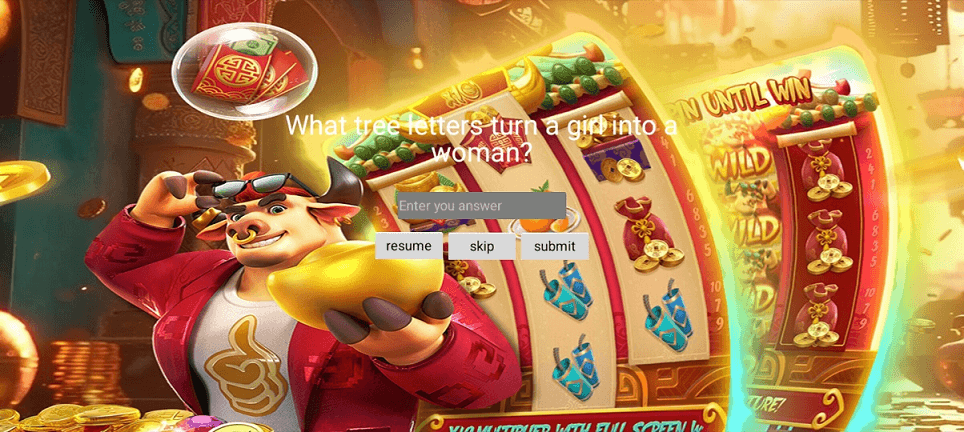
However, its only task was to load fraudulent websites, which could include sites through which users could allegedly access certain games, including adult ones. Below is an example of one such site.
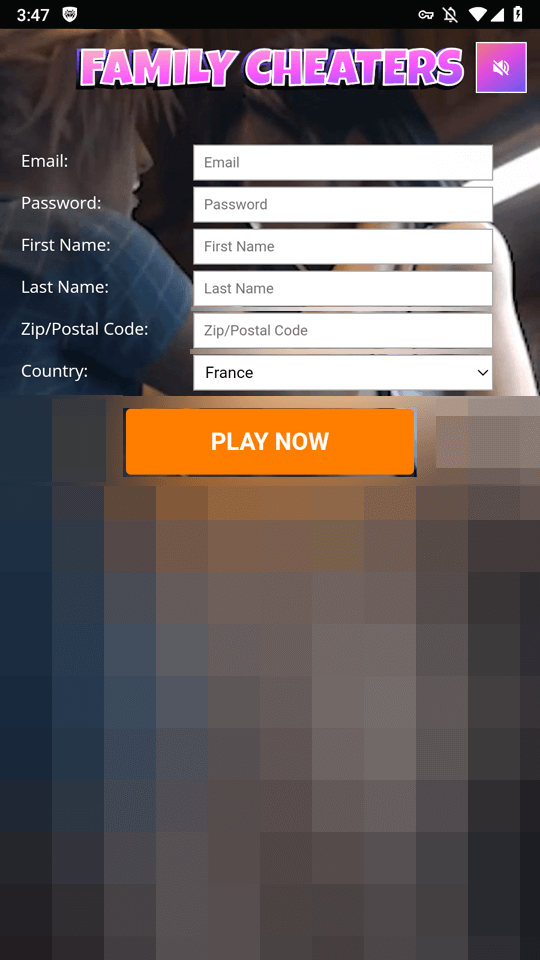
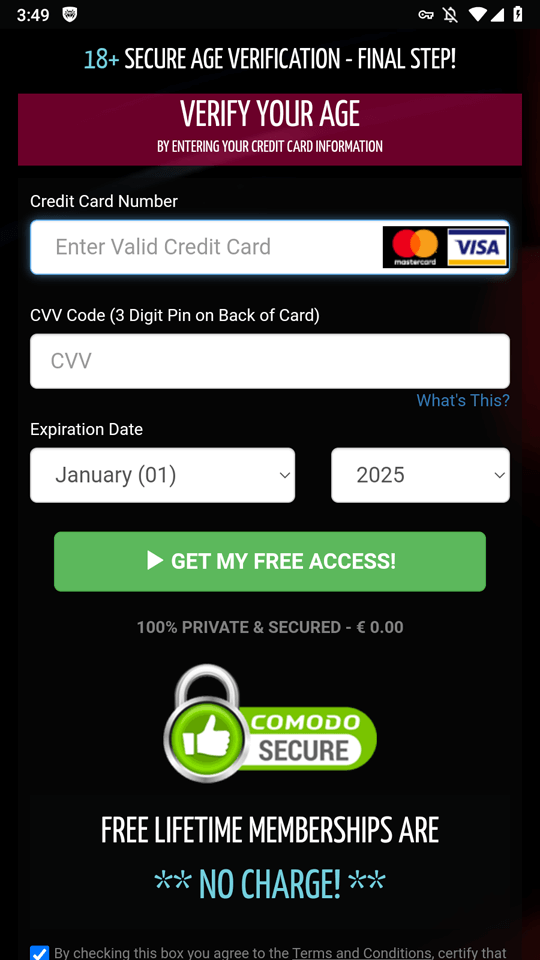
In this case, before “starting” the game, the potential victim is asked to answer several questions and then provide their personal data, followed by their bank card data―supposedly to verify the user’s age.
Some of the malicious Android.FakeApp programs discovered were again disguised as games. They were added to the Dr.Web virus database as Android.FakeApp.1573, Android.FakeApp.1574, Android.FakeApp.1575, Android.FakeApp.1577, and Android.FakeApp.32.origin.
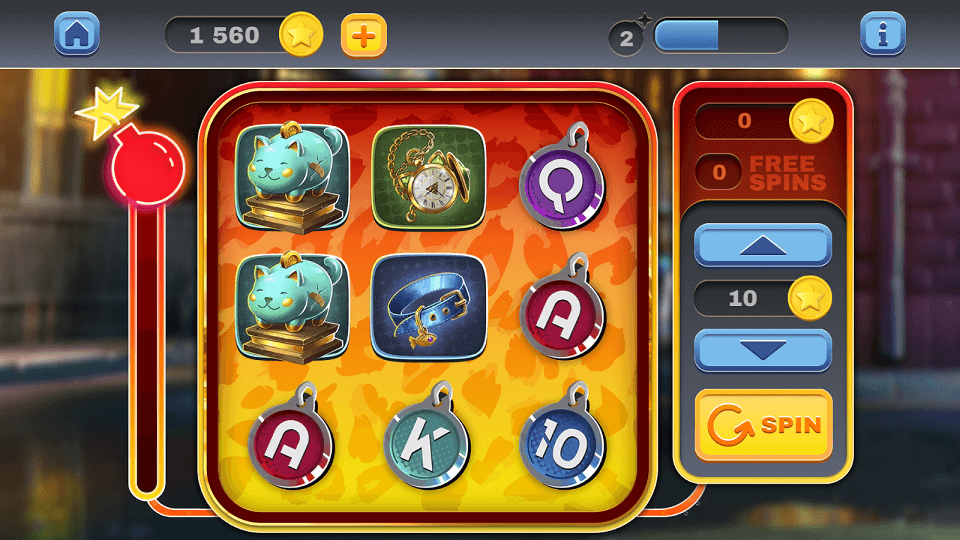
Under certain conditions, such fakes could load online casino and bookmaker websites. Examples of how they operate as games:
An example of one of the websites they loaded:
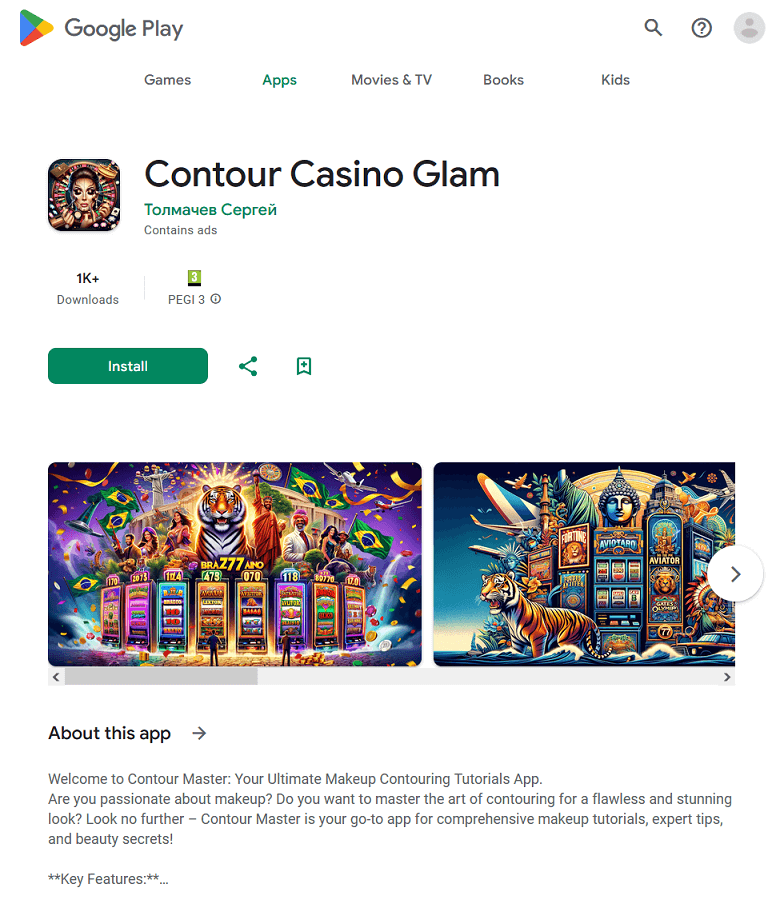
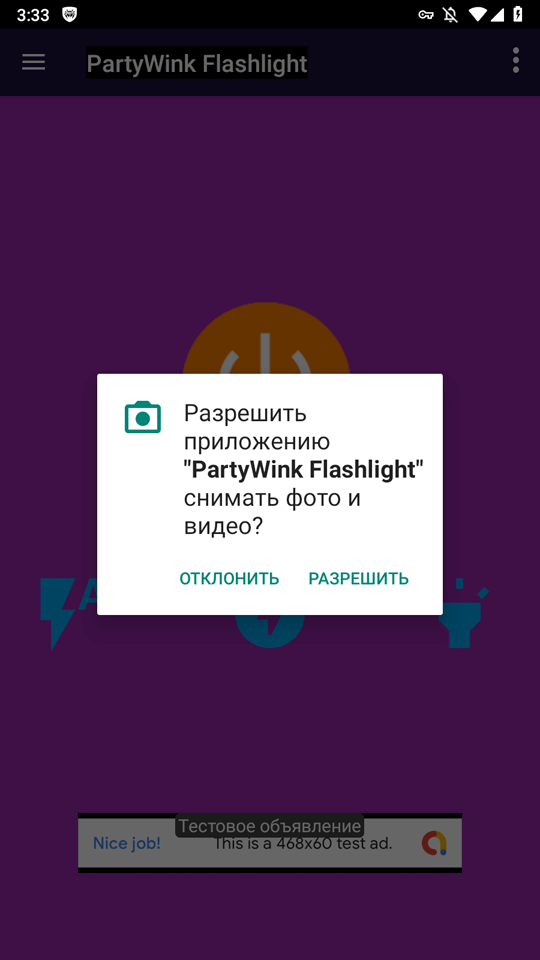
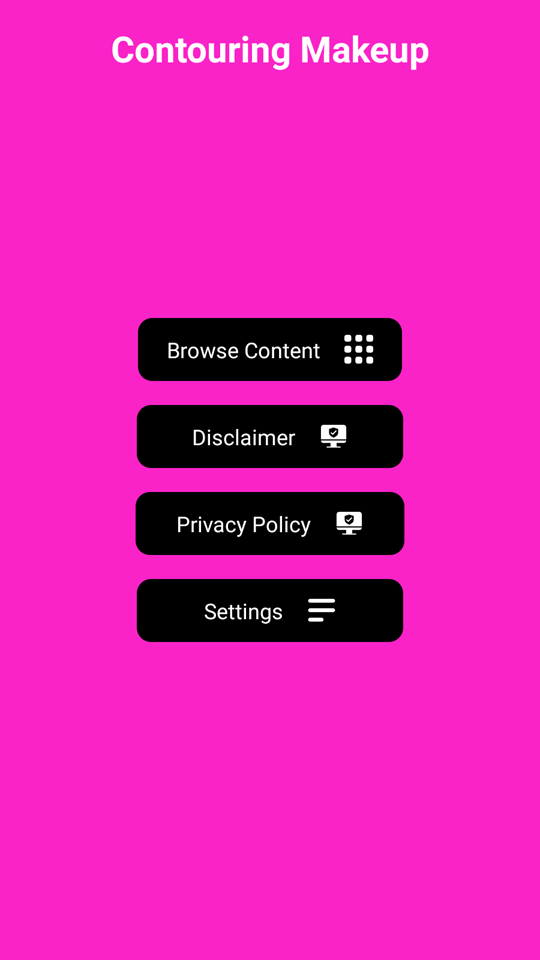
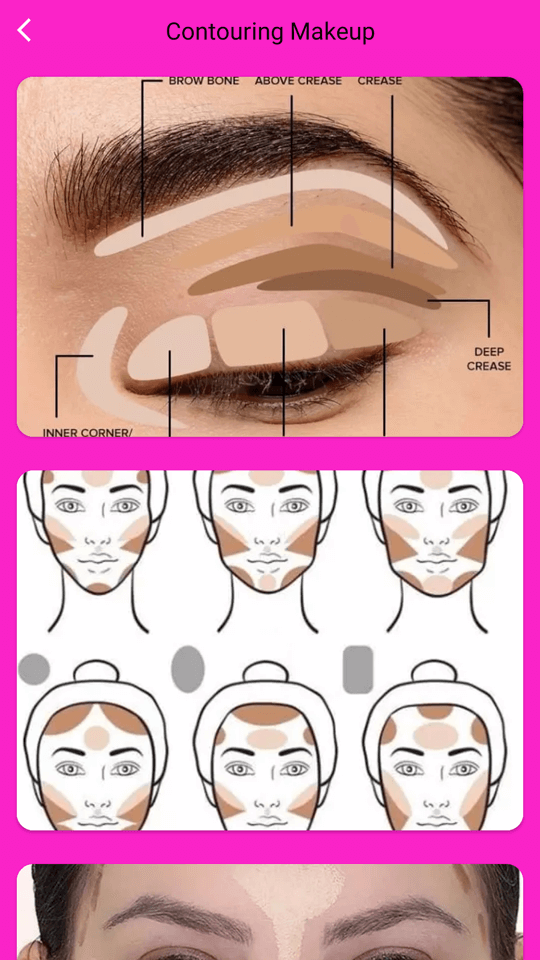
Loading online casino and bookmaker websites was also the task assigned to few other trojans. For instance, Android.FakeApp.1576 malware was concealed in the Contour Casino Glam makeup teaching app and in Fortune Meme Studio―a meme-creation tool. And the Android.FakeApp.1578 trojan was in the Lucky Flash Casino Light flashlight program.
Once installed, they operated as harmless apps, but after a while they could start loading target websites.
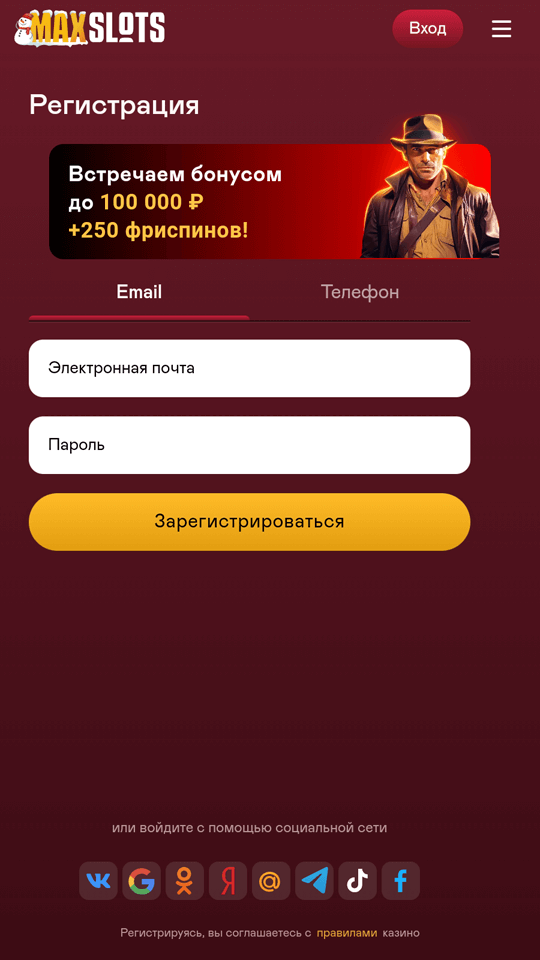
In addition, malicious actors distributed different variants of the Android.FakeApp.1564 and Android.FakeApp.1580 trojans, disguising them as financial apps, reference books and teaching aids, programs for participating in surveys, and other software.
These fake apps loaded bogus financial websites where potential victims were offered various services allegedly on behalf of well-known companies. For example, users “could” become investors or improve their financial literacy. To “access” one or another service, users had to take a survey and register an account by providing their personal data.
Examples of websites loaded:
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products