Hidden crypto miner in pirated software makes cybercriminals rich at the expense of their victims
Real-time threat news | Hot news | All the news
January 15, 2024
In December 2023, virus analysts at Doctor Web noticed an increase in the detection rates of Trojan.BtcMine.3767 and its companion malware Trojan.BtcMine.2742, which, as it turned out, were ending up on users' computers with pirated software.
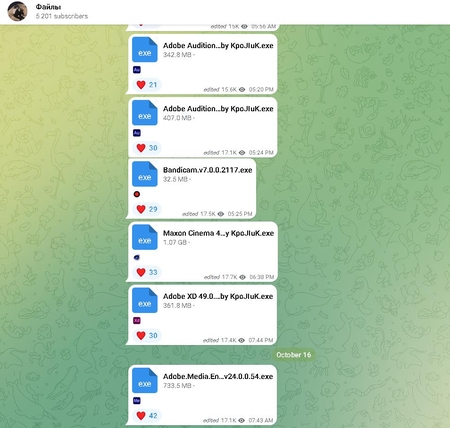
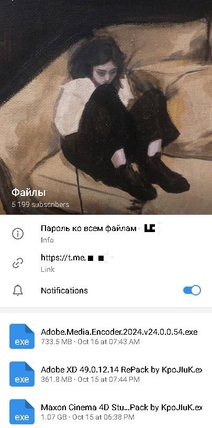
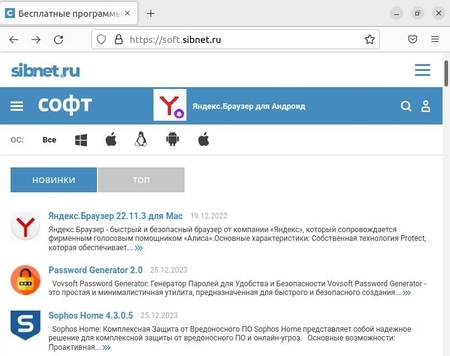
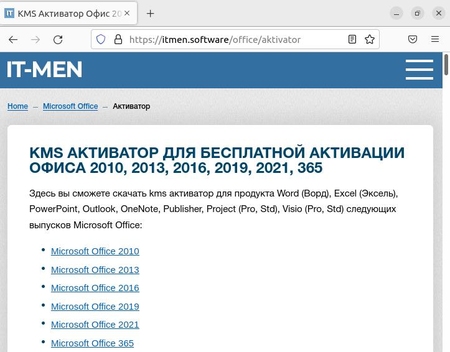
Trojan.BtcMine.3767 is a trojan program for Windows written in C++. It is a crypto-miner loader based on the SilentCryptoMiner project. The platforms used to distribute the infected software packages are the t[.]me/files_f Telegram channel (over 5,000 subscribers) and the itmen[.]software and soft[.]sibnet[.]ru websites. Interestingly, in the latter case the hackers went the extra mile and prepared custom builds using the NSIS installer. After unpacking the installation packages, our analysts discovered the paths used by the attackers to store the trojan's source files:
C:\bot_sibnet\Resources\softportal\exe\
C:\bot_sibnet\Resources\protect_build\miner\
According to the Dr.Web malware analysis lab, in one of the distribution campaigns the trojan has infected over 40 000 computers in a little less than two months. Considering the number of views in Telegram and website traffic, the scale of the problem may be much larger.
When launched, the loader copies itself to the %ProgramFiles%\google\chrome\ directory under the name updater.exe and creates a scheduler task so that it can run on startup. To make it look harmless, the task is named GoogleUpdateTaskMachineQC. In addition, the loader adds its file to the Windows Defender exceptions and prevents the computer from shutting down and hibernating. The initial settings are embedded in the trojan and then updated from a remote host. Once initialized, the loader injects Trojan.BtcMine.2742, the payload responsible for hidden cryptocurrency mining, into the explorer.exe process.
In addition, this loader allows the r77 fileless rootkit to be installed on a compromised computer, Windows updates to be disabled, website access to be blocked, trojan source files to be auto-deleted and -restored, the cryptomining process to be suspended, and the RAM and VRAM occupied by the miner to be unloaded when the computer user runs process-monitoring programs.
Dr.Web anti-virus successfully detects and neutralizes Trojan.BtcMine.3767 and Trojan.BtcMine.2742, so they do not pose a threat to our users.
Indicators of compromise