Fruity trojan downloader performs multi-stage infection of Windows computers
Real-time threat news | Hot news | All the news | Virus alerts
July 27, 2023
For about a year, Doctor Web has been registering support requests from users complaining about Windows-based computers getting infected with the Remcos RAT (Trojan.Inject4.57973) spyware trojan. While investigating these incidents, our specialists uncovered an attack in which Trojan.Fruity.1, a multi-component trojan downloader, played a major role. To distribute it, threat actors create malicious websites and specifically crafted software installers. Among the software in question are various instruments for fine-tuning CPUs, graphic cards, and BIOS; PC hardware-monitoring tools; and some other apps. Such installers are used as a decoy and contain not only the software potential victims are interested in, but also the trojan itself with all its components.
When a visitor tries to download an app from a fake site, they are redirected to the MEGA file hosting service webpage, which offers them a zip file, containing a trojan installer package, for download.
When an unsuspecting victim extracts the executable file from the archive and launches it, the standard installation process begins. However, along with the desired harmless program, which distracts the user, Trojan.Fruity.1 also infiltrates the computer. With the rest of its components, it is copied into the same directory as the decoy app.
Threat actors turned legitimate programs into one the trojan’s “modules”. In the example in question, Trojan.Fruity.1 was implanted into one of the Python programming-language libraries and launched by the python.exe interpreter with a valid digital certificate. In addition, there were also cases when attackers used files from VLC mediaplayer and VMWare virtualization software.
Below is the list of files related to the trojan:
- python39.dll—a copy of an initially harmless library from the Python package in which attackers implanted the malicious code;
- python.exe—the original Python language interpreter which is used to launch the modified library;
- idea.cfg—a configuration containing the data on the payload location;
- idea.mp3—encrypted trojan modules;
- fruit.png—an encrypted payload.
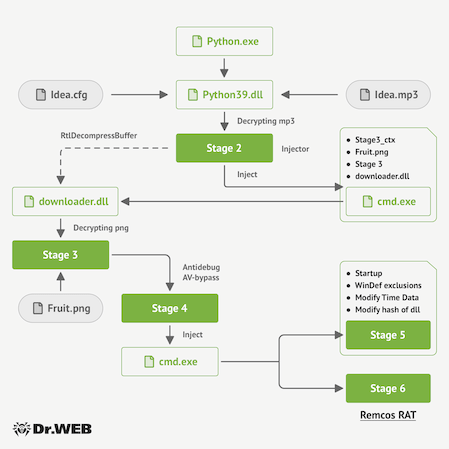
Once all the components are extracted from the installer, a multi-stage infection process of the target system begins. The next image depicts the general schematic of the Trojan.Fruity.1 operating algorithm.
1st stage of infection
Upon the python39.dll library’s launch, Trojan.Fruity.1 decrypts the contents of the file idea.mp3 and extracts the .dll library and shellcode (code №1) from it, making them ready for the second stage. It also reads the contents of the file idea.cfg. This file contains a string with information on the location of the payload that the trojan needs to run. This payload can be downloaded from the Internet or be a local file on a target computer. In this particular case, the fruit.png file that was extracted by the trojan installer earlier is used.
2nd stage of infection
The decoded shellcode (code №1) launches a cmd.exe command-line interpreter in a suspended state. Next, information about the payload (fruit.png file), the shellcode for the third stage (code №2), and the context for its operation are written into its memory section. After that, the .dll file decoded in the previous stage is patched with the data pointing to the address of the context in the process. This .dll file is then injected into the cmd.exe process, after which control passes to the library.
3rd stage of infection
The injected library verifies the string with the data on the location of the encoded payload received earlier. If this string starts with the http abbreviation, the library tries downloading the target file from the Internet. Otherwise, it uses the local file. In this case, the library receives information about the path to the local file fruit.png. This image is moved into the temporary directory, after which code №2 is launched to decrypt it. This image file uses the steganography method to hide two executables (.dll libraries) and the shellcode for the next-stage initialization (code №3) inside it.
4th stage of infection
Upon performing all the previous steps, Trojan.Fruity.1 launches code №3. With its help, it tries to bypass anti-virus detection and prevent the trojan’s debugging process when undergoing analysis by information security specialists.
The trojan tries to perform an inject into the msbuild.exe process of the MSBuild program. If it fails, it tries doing it again with the cmd.exe and notepad.exe (which belong to the Windows command-line interpreter and a Notepad app respectively). Using the Process Hollowing method, one of the .dll libraries decoded earlier from the fruit.png image is injected. The shellcode (code №4) to initialize the fifth stage is also injected.
Next, a .dll file with a random name is created in the temporary directory. The contents of another file decoded from the image are then written into this .dll file. This library is then also injected into the target process. However, the Process Doppelgänging method is used instead, which allows the original process in the memory to be replaced with the malicious one. In this case, this library is the Remcos RAT spyware tojan.
5th stage of infection
Using the shellcode (code №4) and the .dll library injected into the target library, Trojan.Fruity.1 adds the python.exe app into the Autostart list of the Windows OS. It also creates a task for launching the app in the system scheduler. Moreover, Trojan.Fruity.1 adds this app to the list of exclusions of the built-in Windows anti-virus. Next, the shellcode writes random data to the end of the python39.dll file in such a way that its hash sum is changed and thus the file differs from the original one extracted from the trojan installer. In addition, it modifies the library’s metadata, changing its creation date and time.
Despite the fact that Trojan.Fruity.1 is currently distributing the Remcos RAT spyware app, threat actors can use this downloader trojan to infect computers with other malware. At the same time, this malware can either be downloaded from the Internet or distributed together with Trojan.Fruity.1 as part of trojan software installers. As a result, cybercriminals have more opportunities to execute various attack scenarios.
Our specialists remind users that they should download software only from trustworthy sources like developers’ official websites and specialized software catalogs. Dr.Web anti-virus products successfully detect and delete Trojan.Fruity.1 and its malicious components, so they pose no threat to our users.
More details on Trojan.Fruity.1