Linux backdoor malware infects WordPress-based websites
Real-time threat news | All the news | Virus alerts
December 30, 2022
For many years cybercriminals have been attacking WordPress-driven websites. Information security experts register cases when various vulnerabilities of the WordPress platform are used in order to hack sites and inject malicious scripts into them. An analysis of an uncovered trojan application, performed by Doctor Webs’ specialists, revealed that it could be the malicious tool that cybercriminals have been using for more than three years to carry out such attacks and monetize the resale of traffic, or arbitrage.
Dubbed Linux.BackDoor.WordPressExploit.1 in accordance with Dr.Web anti-virus classification, this malware targets 32-bit versions of Linux, but it can also run on 64-bit versions. Linux.BackDoor.WordPressExploit.1 is a backdoor that is remotely controlled by malicious actors. Upon their command, it is able to perform the following actions:
- Attack a specified webpage (website);
- Switch to standby mode;
- Shut itself down;
- Pause logging its actions.
The main functionality of the trojan is to hack websites based on a WordPress CMS (Content Management System) and inject a malicious script into their webpages. To do so, it uses known vulnerabilities in WordPress plugins and website themes. Before attacking, the trojan contacts its C&C server and receives the address of the site it is to infect. Next, Linux.BackDoor.WordPressExploit.1 successively tries exploiting vulnerabilities in the following outdated plugins and themes that can be installed on a website:
- WP Live Chat Support Plugin
- WordPress – Yuzo Related Posts
- Yellow Pencil Visual Theme Customizer Plugin
- Easysmtp
- WP GDPR Compliance Plugin
- Newspaper Theme on WordPress Access Control (vulnerability CVE-2016-10972)
- Thim Core
- Google Code Inserter
- Total Donations Plugin
- Post Custom Templates Lite
- WP Quick Booking Manager
- Faceboor Live Chat by Zotabox
- Blog Designer WordPress Plugin
- WordPress Ultimate FAQ (vulnerabilities CVE-2019-17232 and CVE-2019-17233)
- WP-Matomo Integration (WP-Piwik)
- WordPress ND Shortcodes For Visual Composer
- WP Live Chat
- Coming Soon Page and Maintenance Mode
- Hybrid
If one or more vulnerabilities are successfully exploited, the targeted page is injected with a malicious JavaScript that is downloaded from a remote server. With that, the injection is done in such a way that when the infected page is loaded, this JavaScript will be initiated first—regardless of the original contents of the page. At this point, whenever users click anywhere on the infected page, they will be transferred to the website the attackers need users to go to.
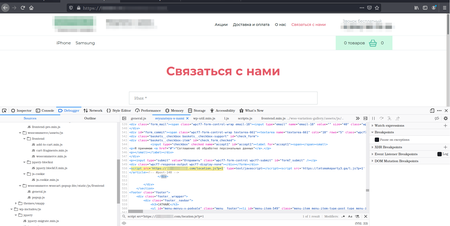
An example of one of the infected pages is shown in the screenshot below:
The trojan application collects statistics on its work. It tracks the overall number of websites attacked, every case of a vulnerability being exploited successfully, and additionally—the number of times it has successfully exploited the WordPress Ultimate FAQ plugin and the Facebook messenger from Zotabox. In addition, it informs the remote server about all detected unpatched vulnerabilities.
Along with the current modification of this trojan application, our specialists also discovered its updated version Linux.BackDoor.WordPressExploit.2. It differs from the original one by the C&C server address, the address of the domain from which the malicious JavaScript is downloaded, and also by an additional list of exploited vulnerabilities for the following plugins:
- Brizy WordPress Plugin
- FV Flowplayer Video Player
- WooCommerce
- WordPress Coming Soon Page
- WordPress theme OneTone
- Simple Fields WordPress Plugin
- WordPress Delucks SEO plugin
- Poll, Survey, Form & Quiz Maker by OpinionStage
- Social Metrics Tracker
- WPeMatico RSS Feed Fetcher
- Rich Reviews plugin
With that, both trojan variants have been found to contain unimplemented functionality for hacking the administrator accounts of targeted websites through a brute-force attack—by applying known logins and passwords, using special vocabularies. It is possible that this functionality was present in earlier modifications, or, conversely, that attackers plan to use it for future versions of this malware. If such an option is implemented in newer versions of the backdoor, cybercriminals will even be able to successfully attack some of those websites that use current plugin versions with patched vulnerabilities.
Doctor Web recommends that owners of WordPress-based websites keep all the components of the platform up-to-date, including third-party add-ons and themes, and also use strong and unique logins and passwords for their accounts.
More details on Linux.BackDoor.WordPressExploit.1
More details on Linux.BackDoor.WordPressExploit.2