Post-holiday lull: virus threats in January 2011
Virus reviews | All the news | Virus alerts
February 8, 2011
Trojan encoders
The beginning of the year saw the emergence of new versions of Trojans that encrypted documents in infected systems and then offered users a special tool with which to decrypt them – for a price.
In particular, modifications of Trojan.Encoder.94 and Trojan.Encoder.96 were added to the Dr.Web virus database in January.
Please remember that unskilled users' actions with encrypted files may cause irreparable harm to the data. Restoring systems, deleting temporary system files, and clearing the browser cache, etc., are not recommended; such actions can make it impossible to recover your data.
Also, do not pick out the first available tool for decryption; in such cases, the risk of corrupting files permanently is high. Instead, request assistance from the Doctor Web virus laboratory: select "cure request" as a request category, and attach a few pairs of encrypted and unencrypted documents to your request.
Windows blockers
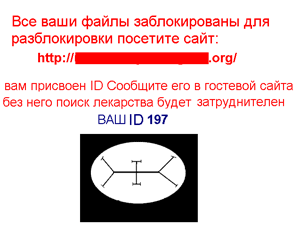
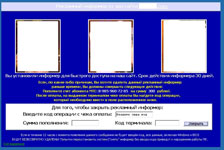
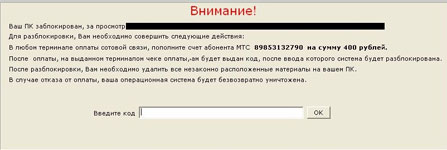
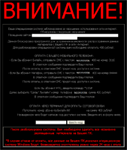
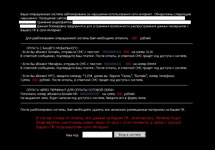
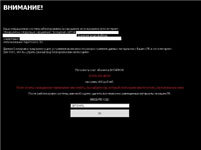
In January, Windows blockers continued spreading to users systems, and these malicious programs have become more diverse. Programs discovered earlier were found along with new types of blockers.
In contrast with the demands displayed by earlier versions of the malware, the new blockers increased the ransom amount demanded to unlock systems.
In late January, Windows blockers were also spread through the LiveJournal site. By clicking on a link in a comment left by intruders, users were taken to a photo hosting site from which they were directed to an adult content website. There victims were invited to download an EXE-file that concealed Trojan.Winlock.
The gallery below shows screenshots of the most common Windows blockers in January.
General statistics of Internet fraud in January
In cases of Internet fraud, over the past month the average number of users requesting assistance from Doctor Web’s free technical support team reached 178, 8% more than in December 2010.
The number of support requests related to malicious programs that required the transfer of money to a mobile phone account increased to 80% (in November 2010, the number of such complaints was 60%, and in December - 70% of the total).
The number of appeals for assistance concerning Trojans that required users to recharge criminals’ mobile phone accounts using appropriate SMS-services rendered by mobile operators, rather than payment terminals, increased from 23% in December to 43% in January.
The number of support requests related to malware demanding that paid text messages be sent continued to fall, and in January 2011, it amounted to only 15% of all appeals.
Banking botnets
Intruders kept spreading botnet client software among Russian users of e-banking systems and electronic cash systems. Typically, each client modification was directed simultaneously at multiple targets, apparently in the hope that one of them might end up on an infected compute.
Doctor Web virus analysts registered the activity of several of these botnets, in particular WinSpy and IBank. Following criminals’ commands, infected computers regularly update their components that make up the "payload" of the botnet. Upgrading is necessary since fraudsters are forced to deal with the anti-virus products installed on users' computers and because the specific objectives of criminals also tend to change through time.
Fake anti-viruses targeting Western Europeans were among January’s other significant threats. System Tool 2011 and Antivirus Scan topped the list of fakes. English-speaking Facebook users also came under attack. Trojan.MulDrop1.62295 was spread as a gift from user to user through spam messages sent over the social network.
Viruses detected in January in mail traffic
| 01.01.2011 00:00 - 01.02.2011 00:00 | ||
| 1 | Trojan.DownLoad1.58681 | 592254 (9.31%) |
| 2 | Trojan.Packed.20878 | 426750 (6.71%) |
| 3 | Trojan.Oficla.zip | 313652 (4.93%) |
| 4 | Trojan.MulDrop.64589 | 311774 (4.90%) |
| 5 | Trojan.DownLoad.41551 | 271184 (4.26%) |
| 6 | Trojan.Packed.20312 | 261419 (4.11%) |
| 7 | Trojan.Oficla.38 | 148062 (2.33%) |
| 8 | Win32.HLLM.Beagle | 117539 (1.85%) |
| 9 | Trojan.AVKill.2788 | 113477 (1.78%) |
| 10 | Trojan.PWS.Panda.114 | 95805 (1.51%) |
| 11 | Trojan.PWS.SpySweep.17 | 92209 (1.45%) |
| 12 | W97M.Killer | 87092 (1.37%) |
| 13 | Trojan.MulDrop1.54160 | 73523 (1.16%) |
| 14 | Trojan.DownLoader1.17157 | 69678 (1.10%) |
| 15 | Win32.HLLW.Autoruner.35407 | 60963 (0.96%) |
| 16 | Trojan.PWS.Panda.387 | 52532 (0.83%) |
| 17 | Trojan.Oficla.48 | 52257 (0.82%) |
| 18 | Trojan.Oficla.73 | 52254 (0.82%) |
| 19 | Trojan.AVKill.3097 | 46052 (0.72%) |
| 20 | Win32.HLLM.MyDoom.54464 | 45653 (0.72%) |
| Total scanned: | 56,551,758,514 |
| Infected: | 6,363,080 |
Viruses detected in January on users' computers
| 01.01.2011 00:00 - 01.02.2011 00:00 | ||
| 1 | Win32.HLLP.Whboy.45 | 27057874 (43.80%) |
| 2 | Win32.HLLP.Neshta | 13487529 (21.83%) |
| 3 | Win32.HLLP.Whboy.105 | 4525965 (7.33%) |
| 4 | Win32.HLLP.Rox | 2224917 (3.60%) |
| 5 | Win32.Siggen.8 | 1583325 (2.56%) |
| 6 | Win32.HLLP.Novosel | 1582034 (2.56%) |
| 7 | Win32.Antidot.1 | 1003419 (1.62%) |
| 8 | Trojan.Packed.21230 | 558842 (0.90%) |
| 9 | Win32.HLLP.Whboy | 396674 (0.64%) |
| 10 | Win32.Sector.22 | 338383 (0.55%) |
| 11 | Trojan.MulDrop.54146 | 285091 (0.46%) |
| 12 | JS.Nimda | 279705 (0.45%) |
| 13 | Win32.Virut.56 | 274936 (0.45%) |
| 14 | Win32.Virut.5 | 271705 (0.44%) |
| 15 | ACAD.Pasdoc | 260004 (0.42%) |
| 16 | Win32.HLLW.Shadow.based | 259855 (0.42%) |
| 17 | Trojan.DownLoad.32973 | 246686 (0.40%) |
| 18 | Trojan.MulDrop1.48542 | 243739 (0.39%) |
| 19 | Win32.Sector.21 | 208654 (0.34%) |
| 20 | Win32.Gael.3666 | 178199 (0.29%) |
| Total scanned: | 127,566,192,623 |
| Infected: | 61,779,350 |