Doctor Web’s October 2022 review of virus activity on mobile devices
December 2, 2022
Banking trojans and apps that facilitate spying on users were noticeably active. For example, Android device users again encountered the Android.Spy.4498 trojan and its various modifications. This malicious program is capable of hijacking the contents of other apps’ notifications, which can cause leaks of confidential and sensitive data.
In addition, Doctor Web’s malware analysts discovered many new threats on Google Play, including malware, adware, and unwanted software.
PRINCIPAL TRENDS IN OCTOBER
- Trojan applications that display unwanted ads remain among the most common Android threats
- The emergence of new threats on Google Play
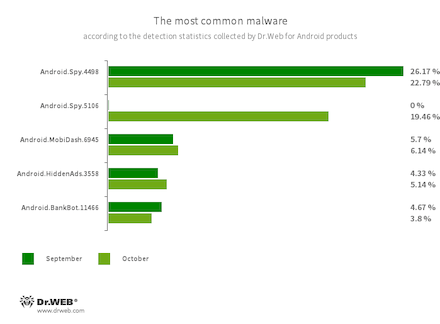
According to statistics collected by Dr.Web for Android
- Android.Spy.4498
- Android.Spy.5106
- The detection name for various modifications of the trojan that steals the contents of other apps’ notifications. In addition, it can download apps and prompt users to install them, and it can also display various dialog boxes.
- Android.MobiDash.6945
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
- Android.HiddenAds.3558
- A trojan designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.BankBot.11466
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
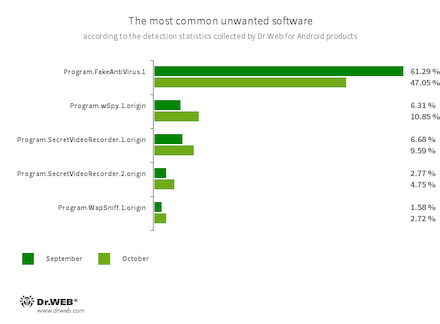
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.wSpy.1.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to a phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.WapSniff.1.origin
- An Android program designed to intercept WhatsApp messages.
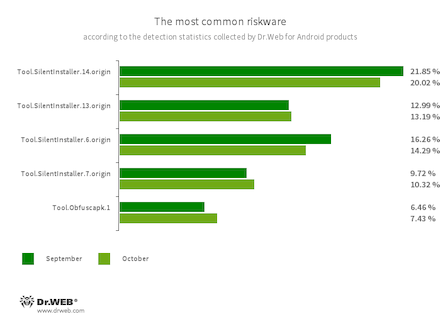
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble the source code of Android apps to make reverse engineering more difficult. Cybercriminals use this tool to protect malicious applications from being detected by anti-virus programs.
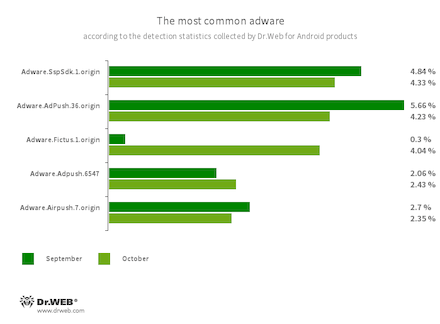
Program modules incorporated into Android applications. These are designed to display obnoxious ads on Android devices. Depending on the family and modification involved, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.SspSdk.1.origin
- Adware.AdPush.36.origin
- Adware.Adpush.6547
- Adware.Fictus.1.origin
- Adware.Airpush.7.origin
Threats on Google Play
In the beginning of October, Doctor Web’s malware analysts discovered the Fast Cleaner & Cooling Master trojan application on Google Play. Malicious actors passed it off as an OS optimization tool. This trojan is controlled with commands that are received through Firebase Cloud Messaging or AppMetrica Push SDK. Depending on the command involved, this app displays ads or launches a proxy server on an affected device. Third parties can use this proxy to channel traffic through it. Various modifications of this malware are detected by Dr.Web as Android.Proxy.35, Android.Proxy.36, and Android.Proxy.37.
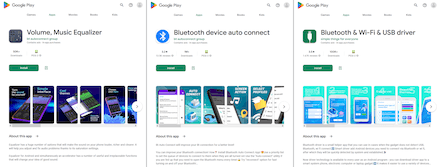
Later, apps containing a new adware module were identified. Dubbed Adware.FireAd, this module receives commands through Firebase Cloud Messaging and loads the websites specified in them. The module was built into some versions of such apps as Volume, Music Equalizer (versions 2.9-3.5 are affected and detected by Dr.Web as Adware.FireAd.1), Bluetooth device auto connect (found in versions 46-58 and detected as Adware.FireAd.2) and Bluetooth & Wi-Fi & USB driver (found in versions 15-19 and detected as Adware.FireAd.2).
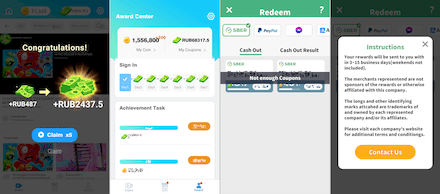
At the end of the month, the Program.FakeMoney.3 virus record for detecting an unwanted application called TubeBox was added to the Dr.Web anti-virus database. With the help of this app, users allegedly could make money by watching videos and ads.
For each view, they allegedly had a reward—coins and coupons—allocated to their internal account. It was claimed that this reward could be converted into real money and easily withdrawn in a convenient way—for example, by bank transfer or through payment systems. And to withdraw the money, they had to accumulate the minimum allowable amount. Even if they collected the required sum over time, users could not receive payments due to certain problems reported by the program. The creators of this app tried to string their victims along for as long as possible so that they would continue watching videos and ads, earning money not for themselves but for the fraudsters.
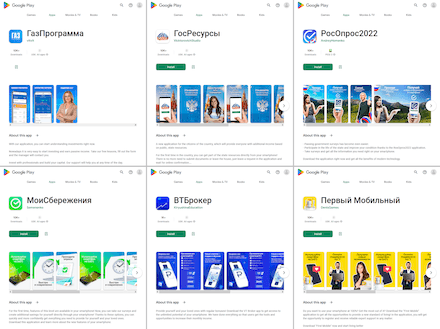
Also, many new fake apps from the Android.FakeApp, trojan family were found during the past month. Cybercriminals used these in various fraudulent schemes. The trojans were disguised as investing applications that allegedly had a direct relationship with Russian banks and commodity companies. They were also distributed as directories and survey programs. Scammers claimed—including through advertisements—that uses could learn how to invest so that they would be able to make profitable investments and trade natural gas themselves, and that they would even receive free stocks of the affiliated companies that allegedly back up all these services. In reality, such fake apps loaded specially crafted sites that were designed to get users to participate in dodgy surveys, register accounts, and submit applications in order to collect their personal information.
Below are examples of ads where potential victims are offered trojan apps to install. The attackers use images of famous personas and companies, and also make loud statements. In particular, they promise high income and accompany their ads with Russian phrases like “Против санкций всей страной” (Protiv sankciy vsei stranoy—“The entire country against sanctions”), “Дарим 10 акций бесплатно” (Darim 10 akciy besplatno—“We grand 10 free shares”), “Заработайте уже во время обучения” (Zarabotayte uzhe vo vremya obucheniya—“Earn while you still learning”), “Я дам вам 100 000 USD, если вы не станете миллионером за 6 месяцев” (Ya dam vam 100 000 USD, yesli vy ne stanete millionerom za 6 mesyacev—"I will give you 100 000 USD if you are not a millionaire in 6 months"), etc.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products