Android users risk falling victim to fraudsters during online job searches
Real-time threat news | Hot news | Threats to mobile devices | All the news
November 21, 2022
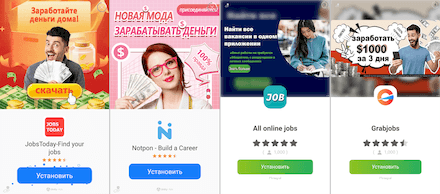
The criminal scheme identified by Doctor Web’s specialists works as follows. Using Google Play, cybercriminals distribute apps that can allegedly help users find a job. To attract the attention of potential victims and increase the chances of successfully deceiving them, scammers can pass off such trojan applications as genuine job-search software. One of them, for instance, was distributed under the guise of an official client for the Job Today service. It had a similar-looking icon and app name and also had a misleading description on its page on Google Play. With that, these trojans are actively advertised; for example, in other apps through built-in advertising systems. This allows installs of them to increase in number.
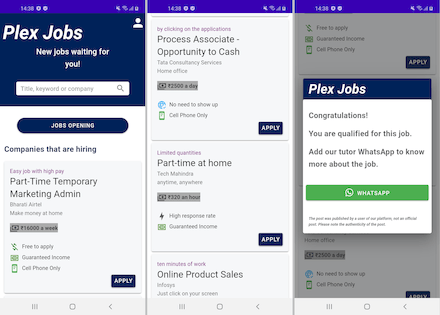
Below are several examples of such ads. Fraudsters lure potential victims by providing lucrative, false promises of easy working conditions and high income.
At the time of this material’s publication, Doctor Web’s anti-virus laboratory had discovered as many as 7 such fakes:
- Jobs Today-find your jobs
- Notpon - Build a Career
- JobsFinder
- Nanoss
- All online jobs
- Jobs Online
- Grabjobs
All of them were added to the virus database as members of the Android.FakeApp family. At the same time, it is possible that more such programs will emerge in the future, given the fact that malware creators do not need strong programming skills to create similar trojans.
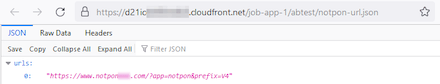
Basically, these trojans are web apps. Upon launch, they load websites inside their own windows—in this case, such websites contain fake job listings. Some of the trojans’ modifications have hardcoded web addresses from the start, while others connect to a remote server to receive target URLs. The server then transmits the necessary parameters in JSON format, as shown in the example screenshot below.
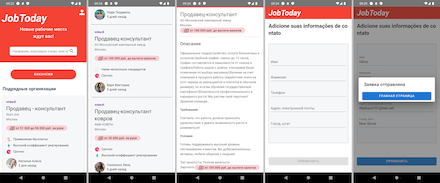
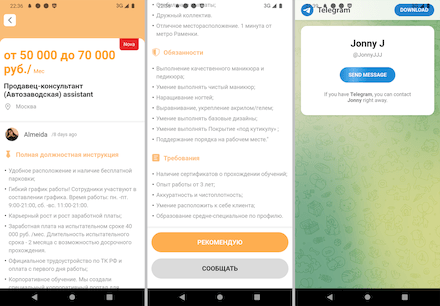
Depending on the contents of the loaded website, different attack scenarios can be implemented. One of the basic scenarios involves the collection of personal information. When a user selects a job promotion they like and tries to apply for it, the website asks them to fill out a mini-form with their personal data. In reality, this is a phishing form, and the “candidate’s” information entered in the fields is then sent not to the hiring company but to the attackers instead. After that, cybercriminals update their databases with their victims’ information and can use the obtained data themselves—to execute various attacks, or they can sell it on the black market.
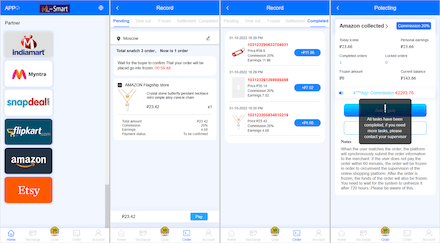
An example of a phishing website with a fake job listing loaded by one of the trojans:
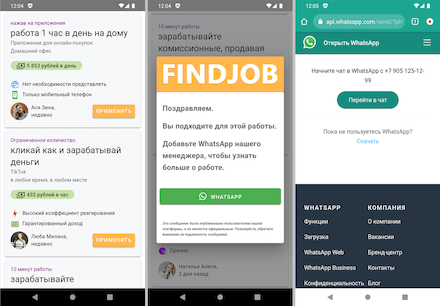
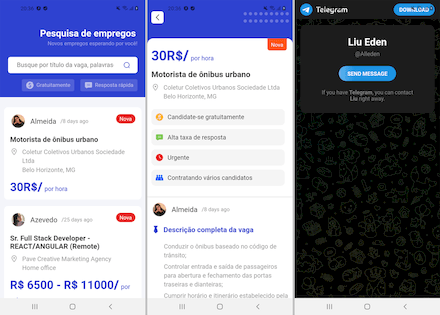
But more complicated scenarios could also be implemented. For example, when a user selects a job promotion, they see a message asking them to contact the “employer” directly—for instance, through WhatsApp, Telegram or other messengers.
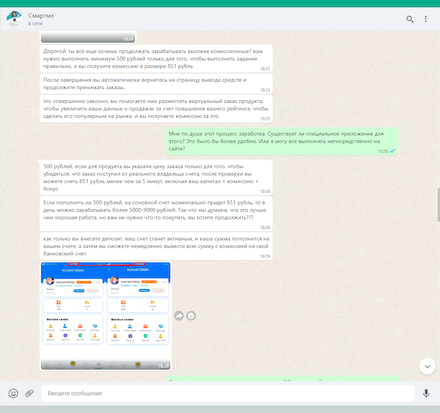
By agreeing to this, the user risks coming into contact with a variety of fraudulent schemes. In particular, malicious actors can introduce themselves as employees of certain companies and actually offer a job in order to interest a potential victim. However, this would be a trick, and in the end, the scammers will not only try to get their hands on users’ personal information but also on their money. In the example in question, cybercriminals pass themselves off as representatives of a company called “ML-Smart International E-commerce” and have a WhatsApp Business account.
At the beginning of the dialog, the scammers introduce themselves as representatives of a large global electronics manufacturer and then ask the user to provide their name, age, and occupation. Having received the answer, they reveal the essence of the “job” they are proposing and describe all of its alleged virtues. According to their statements, the user will join a special platform and participate in improving the ratings of the products listed in online stores by placing virtual orders for the goods. In turn, the sellers will allegedly pay commissions for that. At the same time, the malicious actors promise that the received income can then be withdrawn from this platform at any time.
To become a member of this platform, the user must register on the corresponding website, for which they are given a web link. After registering, the user receives 120 rubles into their account as a “bonus”. And this amount of money is just enough to complete several “training tasks”.
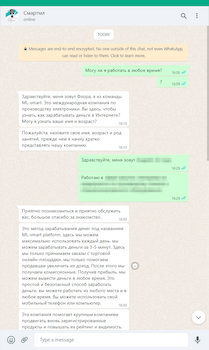
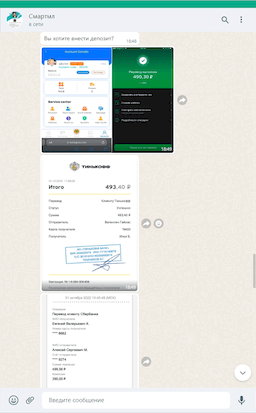
When executing this scheme, fraudsters are in constant contact with the victim. They provide instructions and walk them through every step, maintaining their interest in the service and also the illusion that it is perfectly efficient and secure. However, after successful test “purchases” and initial “reward payments” are made to the internal user’s account, the scammers inform their victim that in order to continue working, a top up of 500 rubles is required. Allegedly this is necessary for account activation. With that, the fraudsters are doing their best to assure the victim that after the money is added, it will immediately return to the user’s internal account—and not only the original sum but with interest. And all this money can then allegedly be withdrawn from the system to a bank account. To make it look more persuasive, cybercriminals can additionally send the user screenshots of some payments that were allegedly received by other members.
In the screenshots below, malicious actors ask the victim to top up their account to activate it and claim that this money, with interest, will be immediately available for withdrawal. They also send screenshots of some payments to convince the user.
In such schemes, scammers can either instantly steal the money that users put into the system or indeed allow them to withdraw their first “income” as a lure. In the latter case, users will be given tasks that involve placing orders for goods with higher and higher prices, and they will not have enough money for it. To solve the issue, they will constantly be asked to put more of their personal money into their account. In the end, the fraudsters will stop contacting their victims once they have received a sufficient amount of money from them. Or the victims themselves, suspecting that something is wrong, will try to withdraw the money but will not be able to do so due to false reasons invented by the scammers.
So, this fraudulent scheme is all about capitalizing on users’ desire to get easy and fast income on the Internet. And it can be implemented against users from any country.
An example of a website where cybercriminals can lure potential victims:
Doctor Web reminds users that any offer of easy income on the Internet must be treated with the utmost care and reasonable skepticism. If the conditions that you are offered look too tempting and lucrative, most likely you are dealing with scammers.
When searching for a job online, you should use trusted resources. And it is very important to make sure that you are dealing with genuine recruiting services. For this, check websites for signs of forgery like an absent or expired security certificate, an incorrect domain name, typos, grammar or punctuation mistakes in the website’s contents, etc. Also, only install services’ dedicated applications from reputable sources—directly from the websites of these services or from app markets. In the second case, you should also make sure that the publisher of the app is not a copycat and not trying to impersonate the original developer of the software in question. In addition, it is important to use an anti-virus with parental control and web-filter functions. It will not only protect you from malicious and fraudulent apps but also from dangerous websites.
Our specialists notified Google about the discovered malware. At the time of this material’s publication, most of the applications remained available for download.
Dr.Web anti-virus for Android successfully detects and neutralizes all known modifications of the above-described trojan apps from the Android.FakeApp family, so they pose no threat to our users.