Banking trojans disguised as shopping apps attack Malaysian Android users
Real-time threat news | Hot news | Threats to mobile devices | All the news
October 19, 2022
Cybercriminals use various methods to disguise malicious Android applications, particularly banking trojans. One involves creating fakes or modifying genuine banking software that is then distributed under the guise of the originals, including via third-party websites. Mobile device users, however, are regularly warned by experts that they should download mobile banking software only from official and reputable app catalogs or directly from their bank’s website. Moreover, as they become more experienced users, they are paying more attention to the signs that can give away a fake—such signs include, for example, an unusual UI, grammatical or graphic errors in the design of a program, a lack of certain functionality, etc. Therefore, as Android device users become more literate in terms of information security, such methods may lose their effectiveness.
Another method is to “hide” a banking trojan where potential victims of an attack will least expect to be tricked. For example, in apps that have no relation to banks but in one way or another are of particular interest to users. These can be a wide variety of apps: those for communicating in social networks, document-editing software, apps for accessing online cinemas, and many others. It is this approach that was taken by the creators of the Android.Banker.5097 and Android.Banker.5098 trojans discovered by our malware analysts.
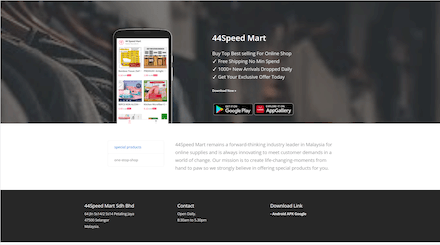
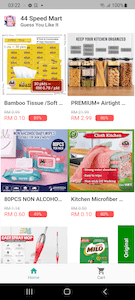
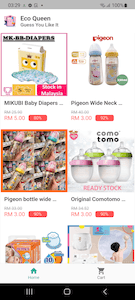
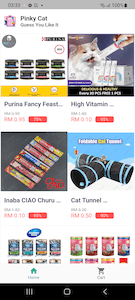
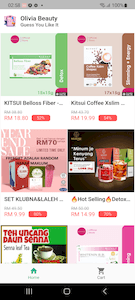
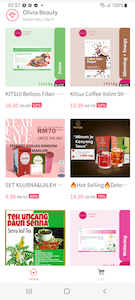
These banking trojans are distributed as mobile shopping apps called “Olivia Beauty”, “44 Speed Mart”, “Eco Queen”, and “Pinky Cat”. Each of them is dedicated to a particular category of goods: food, cosmetics, household products, and supplies for children and pets.
Malicious actors are betting on the fact that users are becoming more accustomed to modern trends in the digital economy and the growing popularity of the “Service―Application” concept—that is, to the fact that many companies, online stores and even groups and communities in social networks have their very own mobile app. Because they are less aware of the potential danger and underestimate the risks, mobile device owners tend to download such apps even from unknown websites. And since the main function of an online store is to provide an opportunity to buy goods and services, potential victims are more likely to disclose their bank card details and other confidential information to such a program. This is what malware creators exploit.
The Android.Banker.5097 and Android.Banker.5098 trojans target Malaysian users. They are distributed through malicious websites, using standard social engineering methods. For example, potential victims that visit these sites are told that they can download the mobile app of one or another of these shops from the Google Play or AppGallery catalogs. In reality, the malicious APKs are downloaded from these websites directly, and the famous app catalogs are only mentioned to confuse and mislead users. To install downloaded trojan apps, users must allow the appropriate action in the settings of their mobile devices.
At first glance, these trojans do indeed look like real shopping apps. They have a list of goods that the user can explore, add to their cart and try to buy. However, this is only a trick, and there is no real functionality in them. With that, to look more appealing, these apps offer users the chance to purchase products at a substantial discount of 49% to 95%.
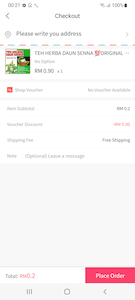
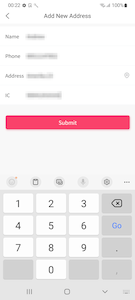
Upon trying to purchase the goods added to their cart, a potential victim is asked to provide their personal data, which is allegedly necessary to ship the order. The information includes the user’s name, residential address, mobile phone and IC number (Identification Card Number), and―in some modifications of the trojans―additionally the date of birth. When provided, this data is sent to a remote server.
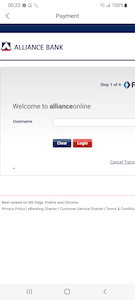
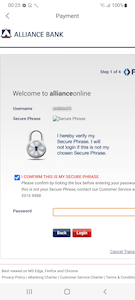
Next, the trojans ask the user to select a bank in order to make payment. When a bank is selected from the provided list, a phishing form is downloaded from the C&C server. This form is created in the style of the bank selected earlier. It contains fields for entering the login and password from the account of the remote banking service. At the time of the analysis, the C&C server had prepared forms to attack the clients of the following credit institutions:
- Maybank
- HLB Connect
- CIMB Group
- Public Bank Berhad
- Affin Bank
- BSN (Bank Simpanan Nasional)
- Bank Islam
- AmBank
- Alliance Bank
However, over time, this list can be changed and expanded with new targets.
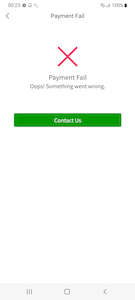
When the user is “authorized” in the remote banking system through this fake form, they are shown an error message, and at this point the “purchasing” process is over. The truth is that the data provided by the victim is transferred to malicious actors. After that, they can log in to the victim’s account and control it.
In order to bypass 2FA protection, and to make sure that a victim does not suspect illegal activity too early, these banking trojans have the functionality needed to intercept SMS containing one-time passwords. At the same time, this functionality in Android.Banker.5097 and Android.Banker.5098 is implemented differently. For example, Android.Banker.5097 uses a specialized framework based on JavaScript, while Android.Banker.5098 uses a special plugin for the Flutter framework.
To conclude, cybercriminals can use these malicious apps not only to steal data required to access banking accounts, but also to obtain valuable personal information. Later this information can be used to execute more attacks or sold on the black market.
Doctor Web warns users once again that downloading and installing Android applications from the Internet, bypassing official sources, significantly increases the risk of their devices getting infected. In this case, both personal data and money can be targeted by malicious actors. To protect your devices from banking trojans and other Android threats, we recommend using an anti-virus. The Android.Banker.5097 and Android.Banker.5098 trojans are successfully detected and neutralized by Dr.Web for Android anti-virus products, so they pose no threat to our users.
More details on Android.Banker.5097
More details on Android.Banker.5098

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products