Doctor Web’s July 2022 review of virus activity on mobile devices
August 31, 2022
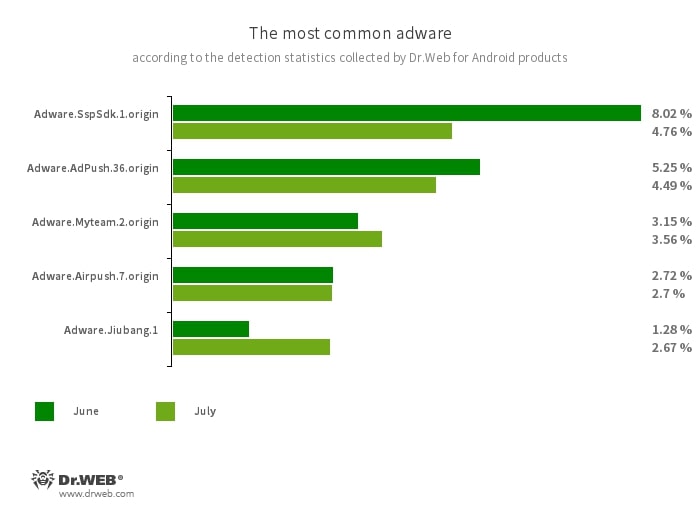
Despite their activity decreasing by 14.84% compared to the previous month, adware trojans from the Android.HiddenAds also remain among the most widespread Android threats.
In July, Doctor Web uncovered an attack on the WhatsApp and WhatsApp Business messengers where malware was infecting the firmware of counterfeit copies of famous smartphone models. The discovered threats could download additional trojan modules to execute a variety of malicious actions.
PRINCIPAL TRENDS IN JULY
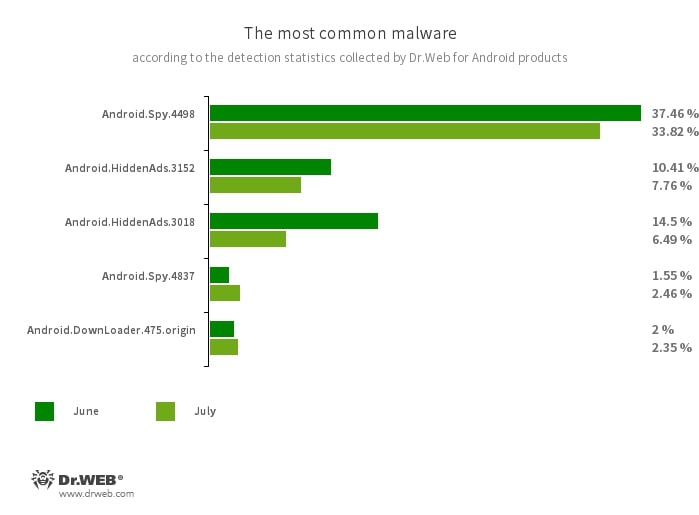
- A decline in Android.Spy.4498 trojan activity
- Decreased adware trojan activity
- An attack on WhatsApp and WhatsApp Business messenger users was identified
Mobile threat of the month
In July, Doctor Web’s anti-virus laboratory discovered a group of trojan applications in the firmware of several models of Android smartphones. These malicious apps targeted users of the WhatsApp and WhatsApp Business messengers. They downloaded additional malicious modules that allowed them to execute various attack scenarios. For example, these trojans could spy on victims, perform phishing attacks and send spam. Moreover, malicious actors could use them to gain remote access to infected devices. Read more about this incident in the special news report on our website.
According to statistics collected by Dr.Web for Android
The detection name for various modifications of the trojan that steals the contents of other apps’ notifications. In addition, it can download apps and prompt users to install them, and it can also display various dialog boxes.
- Android.HiddenAds.3152
- Android.HiddenAds.3018
Trojans designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these trojans infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.DownLoader.475.origin
A trojan that downloads other malware and unwanted software. It can be hidden inside seemingly harmless apps found on Google Play or malicious websites.
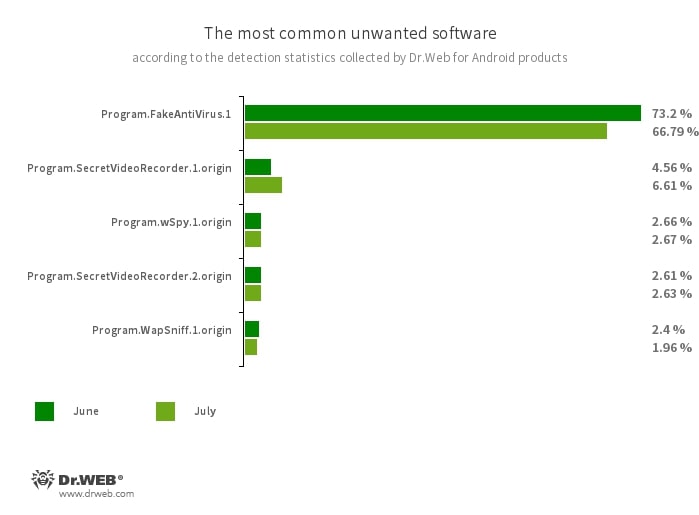
The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand that they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.wSpy.1.origin
A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to a phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.WapSniff.1.origin
An Android program designed to intercept WhatsApp messages.
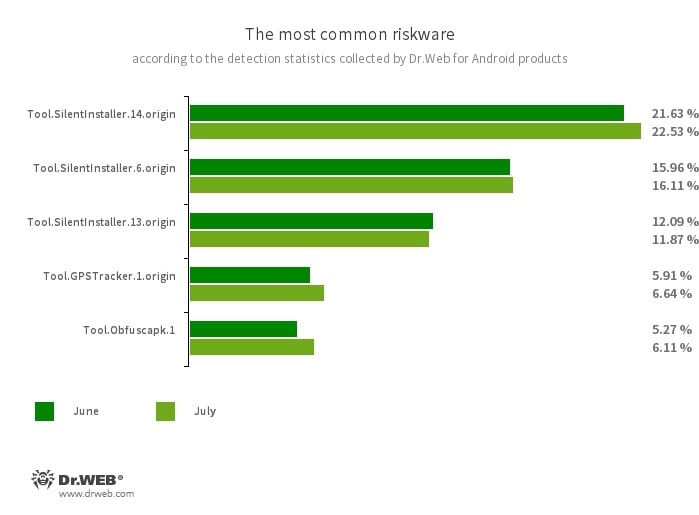
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
A specialized software platform designed to covertly track user location and movement. It can be built into various apps and games.
The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble the source code of Android apps to make reverse engineering more difficult. Cybercriminals use this tool to protect malicious applications from being detected by anti-virus programs.
Program modules incorporated into Android applications. These are designed to display obnoxious ads on Android devices. Depending on the family and modification involved, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.SspSdk.1.origin
- Adware.AdPush.36.origin
- Adware.Airpush.7.origin
- Adware.Myteam.2.origin
- Adware.Jiubang.1
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products