January 21, 2022
Throughout the year, Doctor Web’s specialists observed a significant amount of threats on Google Play. Among those threats were trojans that subscribed victims to paid services, fake software used in various scam schemes, stealer trojans that hijacked confidential information, and adware apps.
At the same time, malicious actors tried to find new ways to infect users’ devices and explored new platforms to exploit to continue their expansion. For instance, trojans were discovered on Huawei’s AppGallery catalog for the first time. One of the APKPure app’s versions was also infected with a dangerous downloader trojan. In addition, malware creators continued using special instruments to help them infect Android devices more efficiently. Various packers, obfuscators, and tools that allow launching apps without their installation were among them.
As in the previous year, cybercriminals used the COVID-19 pandemic hot topic in their favor. For example, they spread all sorts of trojans disguised as useful and harmless software related to coronavirus and vaccination.
PRINCIPAL TRENDS IN 2021
- The number of adware trojans attacks has increased
- An increased activity of Android banking trojans
- Malware that downloaded and installed other software was among most widespread threats discovered on Android devices
- The emergence of new threats on Google Play
- The appearance of first malicious applications on AppGallery
- High activity of scammers and fake apps
- Spreading of spying trojans and apps designed to monitor users
- Malicious actors continued to exploit the COVID-19 pandemic topic in their attacks
Most notable events of 2021
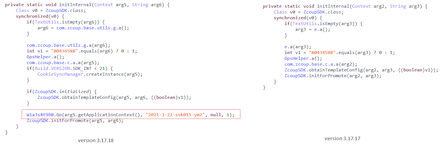
At the end of March, Doctor Web malware analysts discovered a malicious functionality in the client application of an APKPure alternative Android software catalog. Version 3.17.18 of this app was affected, where perpetrators planted a multi-component Android.Triada.4912 trojan. This malware loaded various sites and downloaded other trojan modules and third-party apps.
Below are the code fragments of the trojanized version of the app (left) and its clean variant (right). The highlighted string is responsible for the Android.Triada.4912 initialization.
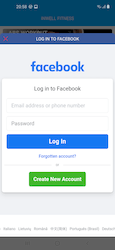
In July, Doctor Web reported on Android.PWS.Facebook trojan apps found on Google Play. These were designed to steal logins, passwords, and other confidential information required to hack into victims’ Facebook accounts. The software in question was fully operational, which weakened the potential victims’ vigilance. Users were asked to log in to their social network account to access the apps’ full functionalities. Here lies the main danger. The trojans loaded a genuine Facebook authentication page into WebView and then injected special JavaScript into the same WebView. This script performed the data hijack. After that, cybercriminals successfully received the stolen passwords, logins, and session cookies.
Many other trojans of the same type have been discovered over the year. Below is an example of how these malicious apps try to steal users’ data:
Also in July, our malware analysts uncovered a brand new family of banking trojans dubbed Android.BankBot.Coper. These are modular malicious apps that execute a multi-stage infection. They spread under the guise of real banking software and other apps. When they infect Android devices, they try to obtain access to Accessibility Services that will grant them full control over the affected system and allow them to imitate the user’s actions. The trojans had rich functionality. They could intercept and send SMS, send USSD requests, lock and unlock the screen, display push notifications and phishing windows, uninstall apps, execute keylogger functionality by hijacking keystrokes, and so on. They also had a variety of self-defense mechanisms.
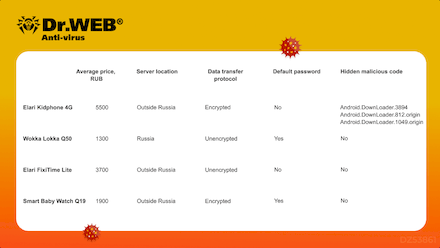
In November, Doctor Web published a study of popular children’s smartwatches in Russia. Our goal was to search for potential vulnerabilities in these devices. The analysis revealed that their safety level was unsatisfactory. For instance, one of the models had preinstalled trojan apps. Some other models used default passwords to access remote control functionality, while the passwords themselves in some cases could not be changed. Moreover, some smartwatches transferred sensitive information without encryption. Below is a summary table with the main discovered vulnerabilities:
Our specialists also discovered the very first malware on AppGallery, an official app catalog for Huawei Android devices. Multi-component Android.Joker trojans were among them, and we reported on this case in spring. One of these trojans’ main functions is subscribing Android device owners to paid mobile services. They covertly downloaded and ran malicious modules, then loaded websites where they automatically subscribed users to various services. To do this, they used the victim’s mobile phone number and a verification code hijacked from a confirmation SMS and input them into the appropriate web-form fields.
Several examples of these malicious apps are shown on a screenshot below:
Already in the fall, dozens of games with built-in Android.Cynos.7.origin trojan module were found on AppGallery. This module represented a specialized piece of software that collected information about users’ mobile phone numbers and their devices. It sent this information to malicious actors and also displayed ads. According to the statistics available on the apps’ AppGallery pages, over 9.300.000 users have installed them.
During the year, threat actors again actively exploited COVID-19 pandemic and vaccination topics to distribute all sorts of malware. For example, an Android.SmsSpy.830.origin trojan that hijacked SMS was hiding in an app called Free NET COVID-19, which was allegedly designed to provide free Internet access.
Another trojan, the Android.SmsSend.2134.origin, was spread under the guise of an app called CoWinHelp, which claimed to help victims to sign up for vaccination. In reality, this malware sent SMS with the link to download a copy of the trojan to every contact in the user phonebook.
When installing an app called Coronavirus Tracker, which allegedly allowed monitoring coronavirus infections statistics, users encountered a ransom trojan Android.Locker.7145. It locked devices and demanded a ransom to unlock them.
Banking trojans were not forgotten, either. For instance, threat actors created fake copies of existing software designed to voluntarily share and trace contacts, send notifications of possible coronavirus exposure and infection, and verify users’ vaccination status. That way, the Android.BankBot.904.origin banking trojan was masquerading as an official NHS COVID-19 app from the National Health Service of UK, while Android.BankBot.612.origin banker was mimicking an app TousAntiCovid supported by the French Ministry for Solidarity and Health.
Statistics
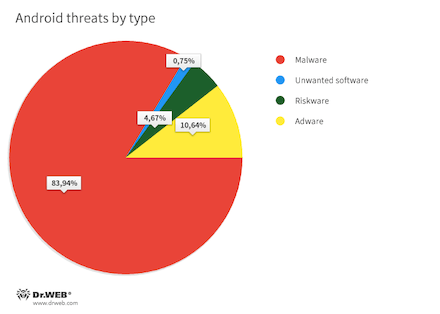
In 2021, like the year before, Android device users most often encountered various malicious applications. According to detection statistics collected by Dr.Web anti-virus products for Android, they accounted for 83.94% of all threats detected on protected devices. The second most widespread threat was adware software and specialized adware modules, embedded into games and other apps. Their share was 10.64% of all detections. Riskware apps retained third place, with a share of 4.67%. Unwanted software kept status-quo and remained at fourth place—it was detected in 0.75% cases.
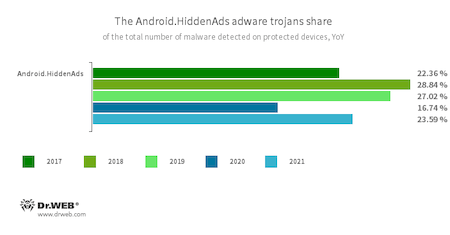
Compared to the year before last, the balance of power in the camp of malware has slightly changed. Thus, trojans from the Android.HiddenAds family, known from 2016, came to the fore. They are dangerous because they display aggressive and annoying ads, like banners and video clips, which often overlay windows of other apps and even the operating system’s UI. This can affect the normal usage of Android devices. With that, such malware often “hides” from users. For example, these trojans conceal their apps’ icons from the home screen menu. The number of attacks involving them has increased by 6.7%, while they accounted for 23.59% of total malware detections. Thus, almost one in four trojans users came across last year belonged to this veteran family. That makes it one of the most prevalent Android threats today.
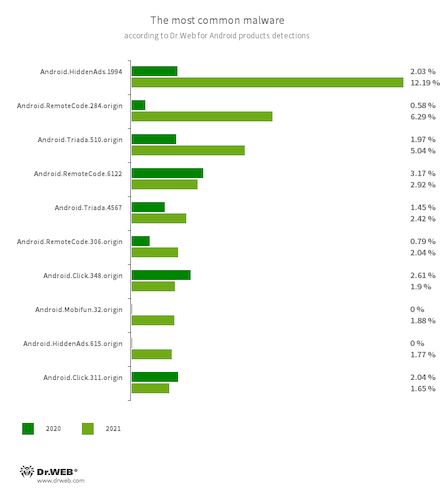
The statistics analysis showed that Android.HiddenAds.1994 modification was among the most active modifications of this family (12.19% of attacks). With that, in October, our specialists discovered its new version dubbed Android.HiddenAds.3018. This trojan is peculiar because its copies receive packets’ names of real apps on Google Play from malware creators. This tactics can be used to escape apps’ verification on Android devices or Internet services through which such malicious apps are distributed. Since this updated modification emerged, it gradually began to dominate over its predecessor whose activity, in contrast, was decreasing. We have every reason to believe that, over time, a new version will completely replace it.
We noted a decrease in the malicious apps that primarily download other software and execute arbitrary code. Still, they remain one of the most active and serious Android threats. Such malware includes trojans from the Android.RemoteCode family (15.79% of total malware detections), Android.Triada (15.43%), Android.DownLoader (6.36%), Android.Mobifun (3.02%), Android.Xiny (1.84%), and others. All of them also help malware creators make money. To achieve this, they participate in various affiliating programs and execute a variety of criminal schemes. These include traffic monetization by artificially increasing downloads counters and installing games and apps, subscribing users to paid mobile services, distributing other trojans, and so on.
Clicker trojans from the Android.Click family (10.52% of total malware detections) remain among the most popular malicious software, and they are another instrument to make illegal profits. They can imitate user actions, like loading websites with ads, clicking on banners and links, automatically subscribing victims to paid services, and executing other malicious functionalities.- Android.HiddenAds.1994
- Android.HiddenAds.615.origin
- Trojans designed to display obnoxious ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these trojans infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.RemoteCode.284.origin
- Android.RemoteCode.6122
- Android.RemoteCode.306.origin
- Malicious applications that download and execute arbitrary code. Depending on their modification, they can load various websites, open web links, click on advertising banners, subscribe users to premium services, and perform other actions.
- Android.Triada.510.origin
- Android.Triada.4567.origin
- Multifunctional trojans performing various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family can be found in the firmware of Android devices, which attackers implanted during the manufacturing process. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
- Android.Click.348.origin
- Android.Click.311.origin
- Malicious applications that load websites, click on banner ads, and follow links. They can be distributed as harmless programs without arousing suspicion among users.
- Android.Mobifun.32.origin
- A malicious dropper that distributes an Android.Mobifun.29.origin trojan. The latter is a dropper itself and acts as an intermediate in a payload (other malware) delivery chain to Android devices.
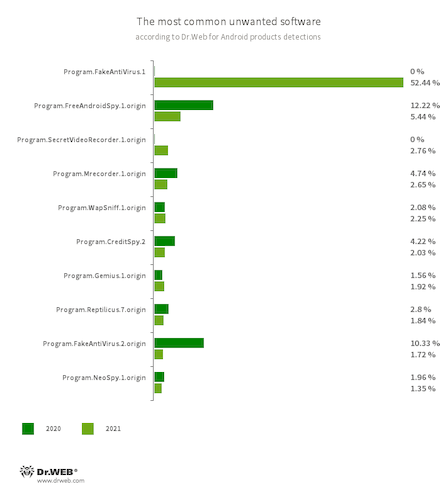
In 2021, more than half (55.71%) of unwanted programs detected on Android devices were apps from the Program.FakeAntiVirus family. This is almost 3.5 times more than the previous year. Such apps imitate anti-virus programs, detect non-existing threats, and ask users to buy their full versions—allegedly to cure infections and fix problems.
In addition, Dr.Web anti-virus products for Android detected many specific applications that can monitor users’ activity, collect information about them, and remotely control their devices.
- Program.FakeAntiVirus.1
- Program.FakeAntiVirus.2.origin
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand they purchase the full version of the software.
- Program.FreeAndroidSpy.1.origin
- Program.SecretVideoRecorder.1.origin
- Program.Mrecorder.1.origin
- Program.Reptilicus.7.origin
- Program.NeoSpy.1.origin
- Applications that spy on Android users and can be used for cyber espionage. Depending on their modification and version, they can control the device’s location, collect information on calls, SMS, and social media chats, and gain access to a phone book and user contact list. They can also record the surroundings, and copy multimedia and other files, such as photos, videos, documents, etc.
- Program.WapSniff.1.origin
- An Android program designed to intercept messages from WhatsApp.
- Program.CreditSpy.2
- The detection name for programs designed to assign credit ratings to users based on their personal data. These applications upload SMS, contact information from phonebooks, call history, and other information to the remote server.
- Program.Gemius.1.origin
- An application that collects information about Android devices and how their owners are using them. With technical data, it also collects confidential information, like device location, browser bookmarks, web history, and typed URLs.
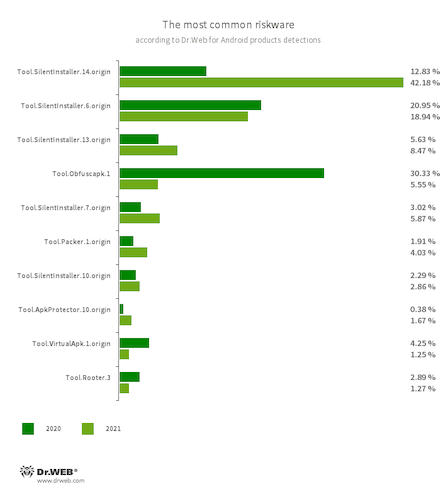
The most common riskware again were specialized tools that allow launching Android apps without installing them. Various members of the Tool.SilentInstaller family were among them. They confidently took first place by the number of detections with a result of 79.51% of the total number of riskware detected on user devices. This is 53.28% more than a year earlier.
In addition, using all sorts of obfuscators and packer tools by threat actors remain relevant. Through these tools, cybercriminals try to protect malware from anti-virus detection. They also impede the information security specialists from studying the malware. Applications protected by such tools have been detected on Android devices in 14.16% of cases.
The third place in the number of detections was secured by tools that allow obtaining root privileges. Such instruments can work in conjunction with trojan apps, allowing them, for example, to infect the system directory on Android devices. Such utilities accounted for 2.59% of total riskware detections.
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.10.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Tool.VirtualApk.1.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cybercriminals use it tool to protect malicious applications from being detected by anti-virus programs.
- Tool.ApkProtector.10.origin
- The detection name for Android apps protected by the ApkProtector software packer. This packer is not malicious in itself, but cybercriminals can use it when creating malware and unwanted applications to make it more difficult for the anti-virus software to detect them.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorized modifications and reverse engineering. This tool is not malicious by itself, but it can be used to protect both harmless and malicious software..
- Tool.Rooter.3
- A utility designed to obtain root privileges on Android devices through various exploits. While it may be used by device owners themselves, cybercriminals and malware can also deploy it.
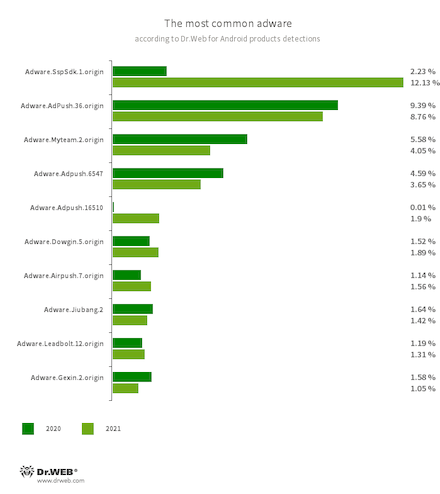
Concerning adware, applications with modules that displayed notifications and dialog boxes and also downloaded and offered users to install various games and apps were most often detected on protected devices. In addition, modules built into various apps and designed to display advertisement banners outside such host apps were common again.
- Adware.SspSdk.1.origin
- Adware.AdPush.36.origin
- Adware.Adpush.6547
- Adware.Adpush.16510
- Adware.MyTeam.2.origin
- Adware.Dowgin.5.origin
- Adware.Airpush.7.origin
- Adware.Jiubang.2
- Adware.Leadbolt.12.origin
- Adware.Gexin.2.origin
- Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
Threats on Google Play
A large number of trojans from the Android.Joker family were among the threats found on Google Play in 2021. These are dangerous because they can download and execute arbitrary code and automatically subscribe users to paid mobile services. Such trojans were spread as all sorts of apps, like photo and video editors, music players, messengers, office apps allowing to work with documents, healthcare apps, translators, system optimization tools, and others. With that, they performed as expected, executing claimed functionality, so that potential victims would not suspect them to be malicious. Throughout the year, Doctor Web malware analysts discovered more than 40 previously-unknown modifications of these malicious apps, with more than 1.250.000 installations combined.
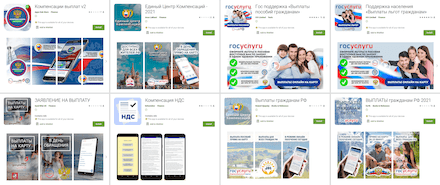
Another massive threat was the malicious fake apps from the Android.FakeApp family. Cybercriminals use these in a variety of scam schemes. Such trojans also spread under the guise of useful and harmless applications. In this case, though, they do not provide any real functionality. Most of these trojans primarily aim to trick users and lure them to fraudulent websites, while fishing out as much confidential information as possible. Our specialists discovered hundreds of these trojans, downloaded by more than 1.700.000 users.
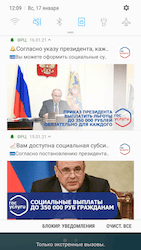
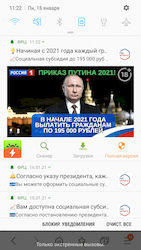
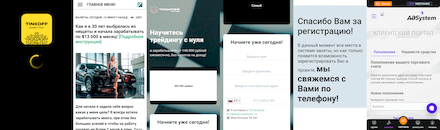
Just like the year before, one of the popular schemes was apps exploiting the topic of financial support provided to citizens by the Russian government. For this, many Android.FakeApp trojans disguised themselves as useful applications, meant for searching information about social benefits and allowance payments, VAT returns, and so on. What’s more, these fakes claimed that users could receive payment through them. Yet, they only loaded fraudulent sites where every visitor was promised to receive hefty sums. To get the “money”, victims had to pay a “state tax” or a “bank commission”, from as low as a few hundred to as much as several thousand rubles. In reality, though, scammers’ victims did not receive any payments at all. Instead, users only transferred money to cybercriminals and provided them with their personal data.
Some modifications of these trojans periodically displayed notifications with messages informing users about allegedly available payments and compensations. This way, threat actors tried to catch the attention of more potential victims, so they visit fraudulent sites more often. Below are examples of such notifications:
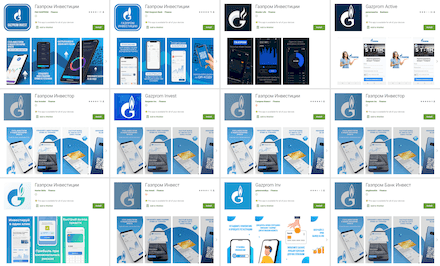
Another popular scheme was the investment offerings and earnings on trading cryptocurrencies, oil, natural gas, and other assets. PC owners have been facing similar schemes for several years now. Last year, they began to be more actively used against mobile device users as well. For this, corresponding fake programs were created. With their help, users allegedly could get passive income from the investments without any experience or special economic knowledge. To make them more appealing, attackers often distributed these trojans under the guise of official software from well-known companies or copied the looks of real financial applications.
Many of them loaded websites where the users were asked to specify personal information to register their account. Then they had to wait for an “operator” to call back. The cybercriminals could use the data provided during the registration to conduct more attacks and scams or sell them on the black market. This information included the victims’ names and last names, emails, mobile phone numbers, etc.
The examples of how these trojans work are shown below:
With that, financial fake apps targeted not only Russian people, but also users from other countries. They equally risked visiting fake websites and getting into the scammers’ traps.
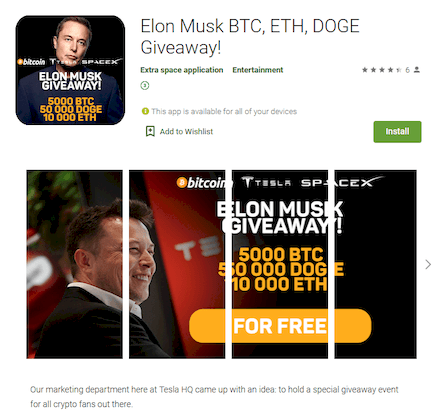
One of these trojans dubbed Android.FakeApp.277 was even spread as an investing app from Elon Musk. It offered potential victims to “double” their available cryptocurrency by sending it to Tesla’s alleged crypto-wallets. This fake had nothing to do with the famous company or its owner, and the tricked users were only sending their cryptocurrency to scammers.
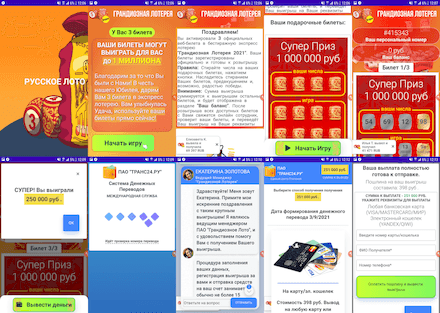
Another group of trojans from this family has been actively distributed under the guise of official software of popular Russian lotteries. Through these apps, users could allegedly get free lottery tickets and take part in prize draws. In reality, tickets were fake and the game was only simulated with the “lucky one” always winning whenever they “played”. At the same time, to receive the “prize”, victims had to pay a “fee” or a “commission”. Of course, this money ended up in the scammers’ pockets.
An example of how these trojans scam users:
Cybercriminals used other schemes as well. For example, some Android.FakeApp trojans were spread as apps that threat actors passed off as harmless programs of a variety of subjects. Reference software about fashion, animals, nature, various horoscopes, and other topics were among them. Others were distributed under the guise of apps with information on diseases and ways to treat them. In the first case, scammers did not even try to conceal the signs of fakes. Upon these apps’ launch, potential victims unexpectedly ended up on dubious and straight fraudulent “online dating” sites. There, to attract potential victims’ attention, cybercriminals simulated communication with real people, while users were offered to register, sometimes in exchange for a fee. In the second case, victims ended up on sites that advertised some miracle drugs that they were “lucky” to find in stock and could allegedly purchase at a very favorable price.
Fake apps were also spread as software that allegedly helped users get discounts, promotions, bonus cards, and gifts from well-known stores and companies. To look more appealing, they used logos and names of the respective brands—electronics manufacturers, gas stations, and retail stores.
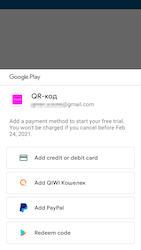
Depending on their modification, these trojans offered the potential victims to subscribe for a paid service starting from 400 rubles per day or per week. Allegedly, this was to get access to the apps’ full functionality and bonuses. However, the victims only received useless barcodes or QR codes. Within 3 days from the subscription, users could cancel it. In this scheme, the malicious actors expected that victims would either forget they installed these programs and activated a paid service, or simply would not pay attention that they had activated any paid service with periodic charges.
Other types of malware have also been found on Google Play. Android.Proxy trojans, for instance, that turned infected devices into proxy servers through which perpetrators redirected Internet traffic. Our specialists also discovered new modifications of adware trojans from the Android.HiddenAds family.
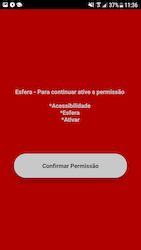
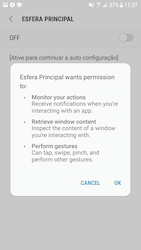
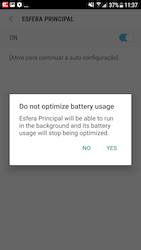
In addition, banking trojans appeared in the official Android app catalog. One of them, dubbed Android.Banker.3679, was spread under the guise of an app designed to work with Santander bank’s Esfera rebate and bonus program. It was targeting Brazilian users.
Its main functionality was phishing and stealing confidential data, while its primary target was the banking application Santander Empresas. The trojan requested access to an Android OS’s Accessibility Services. It used these capabilities to gain control over the device. Then, it could automatically interact with various menus, press buttons, and read the contents of other apps’ windows.
Another trojan, Android.Banker.4919, was distributed under the guise of genuine Resalat Bank and Tose'e Ta'avon Bank banking apps. It targeted Iranian users. It loaded phishing sites and had the ability to hijack SMS, but could not do the latter due to the lack of necessary system permissions.
An example of one of the phishing websites this trojan loaded:
Our specialists also discovered apps with built-in adware modules from the Adware.NewDich family. Upon C&C server command, they loaded various websites in the Android devices’ browsers. These sites were loaded only when users weren’t using those programs, to avoid raising suspicions.
Adware.NewDich modules often load pages of various affiliate and advertising services that redirect users to sections of apps hosted on Google Play. One of them was an app that turned out to be a banking trojan. Dubbed Android.Banker.3684, this trojan was intercepting typed passwords and logins, incoming verification codes, and the contents of incoming notifications, for which it requested appropriate system permission. Another advertised app was plugged with an Adware.Overlay.1.origin adware module that loaded web pages and displayed them on top of windows of other applications.
Banking trojans
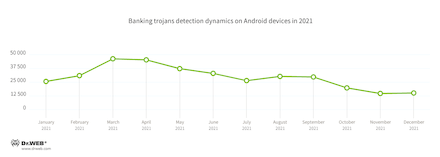
In 2021, the number of banking trojans detected on protected Android devices increased by 43.74% compared to the previous year. Their numerous modifications accounted for 5.4% of all malware detections. Their peak activity occurred at the beginning of spring, after which their attack intensity gradually decreased, with a slight activity increase in August and September.
The increased overall activity of these malicious apps was largely due to the emergence of new families. For example, at the beginning of January, Oscorp (Android.BankBot.792.origin) banking trojan started circulating, while in July, virus records for the S.O.V.A. (Android.BankBot.842.origin) trojan detection were added to Dr.Web virus database. Around the same time, it became known about the Coper and Abere (Android.BankBot.Abere.1.origin) trojans. The latter is notable because it is controlled through Telegram messenger bots. Already in October, various modifications of the SharkBot (Android.BankBot.904.origin) started to threaten users.
Moreover, the threat actors spread Anatsa (Android.BankBot.779.origin) and Flubot (Android.BankBot.780.origin, Android.BankBot.828.origin) bankers. Even though their first modifications emerged at the end of 2020, their primary activity occurred just in the last 12 months.
At the same time, the old families remained active. These include Anubis (Android.BankBot.518.origin, Android.BankBot.670.origin, Android.BankBot.822.origin, and other modifications), Ginp (Android.BankBot.703.origin), Gustuff (Android.BankBot.657.origin, Android.BankBot.738.origin), Medusa (Android.BankBot.830.origin), Hydra (Android.BankBot.563.origin), BRATA (Android.BankBot.915.origin), Alien (Android.BankBot.687.origin, Android.BankBot.745.origin), and Cerberus (Android.BankBot.612.origin, Android.BankBot.8705). With that, new “descendants” of the Cerberus trojan have also emerged, based on its source code that leaked at the end of 2020. One of them was the ERMAC (Android.BankBot.870.origin) banker that began attacks in July.
Prospects and trends
Making profit remains one of the malware writers’ main goals. Because of that, next year we should expect the emergence of new trojans and unwanted apps allowing the perpetrators to earn money. Since advertisement is a reliable and relatively easy source of income, adware trojans will remain relevant. The number of malware designed to load and install other software is also likely to increase.
New banking trojans will continue to appear, many of which will combine broad functionality. They will not only steal money from user accounts but also perform other tasks.
Threats coming from scammers and a variety of fake apps they spread will remain. Moreover, it is possible to see new attacks using stealer trojans that hijack confidential information and an increase in spyware usage.
We should also expect that more and more cybercriminals will use a broad range of obfuscators and packers to protect their malware.
As for Doctor Web, we will continue monitoring the activity of threat actors and uncovering the most relevant threats, providing reliable protection for our users. To protect Android devices from Android threats, we recommend using Dr.Web anti-virus products for Android and to apply all necessary updates to your operating system and installed apps on time.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products