Vulnerabilities in Log4j 2 threaten users
Real-time threat news | Hot news | All the news
December 27, 2021
The most critical vulnerability, Log4Shell (CVE-2021-44228), is based on Log4j 2 log message generation. When the messages are generated in a specific way, a call to a server controlled by the attackers occurs, followed by execution of the code.
Through these vulnerabilities, cybercriminals spread miners, which are malware for mining cryptocurrencies. They can also spread backdoors to gain remote access to a device and Trojan-DDoS that allow fraudsters to make DDoS attacks.
We record attacks using exploits for the vulnerabilities on one of our honeypots–a special server used by Doctor Web specialists as bait for fraudsters. The most active threat occurred between December 17th-20th, but attacks still continue.
| Day | Number of attacks |
|---|---|
| December 10 | 7 |
| December 11 | 20 |
| December 12 | 25 |
| December 13 | 15 |
| December 14 | 32 |
| December 15 | 21 |
| December 16 | 24 |
| December 17 | 47 |
| December 18 | 51 |
| December 19 | 33 |
| December 20 | 32 |
| December 21 | 14 |
| December 22 | 35 |
| December 23 | 36 |
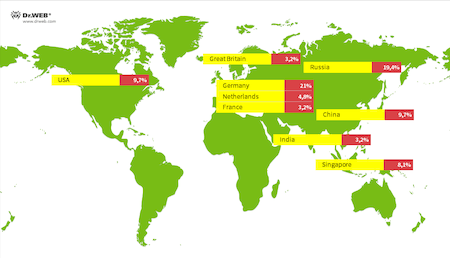
The attacks are carried out from 72 different IP addresses. Talking about the distribution by country, the largest number of attacks were carried out from German IP addresses, with 21%. Russian IP addresses are slightly behind with 19.4%. USA and Chinese IP addresses are ending the top three with 9.7% for both countries.
Some projects depend directly on Log4j 2, while others have one or more implicit dependencies. One way or another, vulnerabilities affect the performance of many projects worldwide. You need to closely watch the release of software updates that use the Log4j 2 library and install them as soon as possible.
Moreover, don’t forget to update Dr.Web regularly. Our products successfully detect the payload of malware that penetrates devices through the Log4j 2 vulnerabilities.