New trojan detected on AppGallery app catalog
Real-time threat news | Hot news | Threats to mobile devices | All the news
November 23, 2021
The Android.Cynos.7.origin is one of the modifications of the Cynos program module. This module can be integrated into Android apps to monetize them. This platform has been known since at least 2014. Some of its versions have quite aggressive functionality: they send premium SMS, intercept incoming SMS, download and launch extra modules, and download and install other apps. The main functionality of the version discovered by our malware analysts is collecting the information about users and their devices and displaying ads.
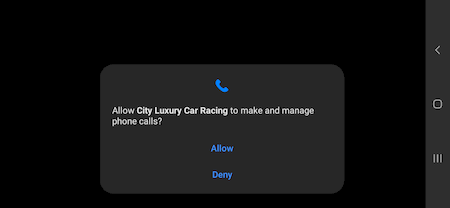
The apps that contain the Android.Cynos.7.origin ask users for permission to make and manage phone calls. That allows the trojan to gain access to certain data.
When the user grants permission, the trojan collects and sends the following information to a remote server:
- User mobile phone number
- Device location based on GPS coordinates or the mobile network and Wi-Fi access point data (when the application has permission to access location)
- Various mobile network parameters, such as the network code and mobile country code; also, GSM cell ID and international GSM location area code (when the application has permission to access location)
- Various technical specs of the device
- Various parameters from the trojanized app’s metadata
At first glance, a mobile phone number leak may seem like an insignificant problem. Yet in reality, it can seriously harm users, especially given the fact that children are the games’ main target audience.
Even if the mobile phone number is registered to an adult, downloading a child’s game may highly likely indicate that the child is the one who actually using the mobile phone. It is very doubtful that parents would want the above data about the phone to be transferred not only to unknown foreign servers, but to anyone else in general.
We found the Android.Cynos.7.origin in 190 games on AppGallery, like simulators, platformers, arcades, strategies, and shooters. More than 9.300.000 users have downloaded these games combined (the number of installations is calculated based on the number of downloads listed on the AppGallery for each app). Some of these games target Russian-speaking users: they have Russian localization, titles, and descriptions. Others target Chinese or international audiences. The below shows examples of games containing this trojan.
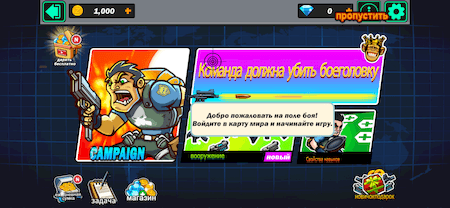
The “Команда должна убить боеголовку” game with over 8.000 installs:
A “Cat game room” game with over 427.000 installs:
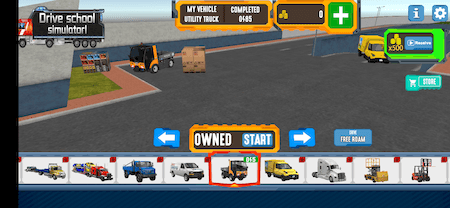
A “Drive school simulator” game game with over 142.000 installs::
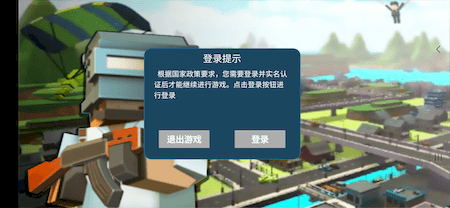
A “快点躲起来” game with over 2.000.000 installs:
Doctor Web has notified Huawei about the threats it discovered. At the time of this publication, the apps containing this trojan have been removed from AppGallery.
Dr.Web anti-virus products for Android successfully detect and delete apps containing all known modifications of the Android.Cynos trojans, so they pose no threat to our users.
More details on Android.Cynos.7.origin

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products