July 9, 2021
Over the past month, Doctor Web’s malware analysts discovered a large number of threats on Google Play. Trojans that stole Facebook account logins and passwords, dangerous programs subscribing victims to premium mobile services, and trojans that loaded fraudulent websites were among them.
PRINCIPAL TREND IN JUNE
- A large number of malicious software was found on Google Play
Mobile threat of the month
Last month, Doctor Web’s specialists discovered malicious programs spread on Google Play and designed to steal Facebook accounts logins and passwords. The trojans dubbed Android.PWS.Facebook.13, Android.PWS.Facebook.14, Android.PWS.Facebook.17, and Android.PWS.Facebook.18 hid in seemingly harmless apps that were downloaded over 5,850,000 times.
To steal confidential information, they loaded genuine Facebook login pages and asked potential victims to log in to the social network. Next, using a special JavaScript, the trojans hijacked the entered logins and passwords and, combined with some other data, sent them to the remote server that belonged to the attackers.
More information on this case is available in one of our news publications.
According to statistics collected by Dr.Web for Android
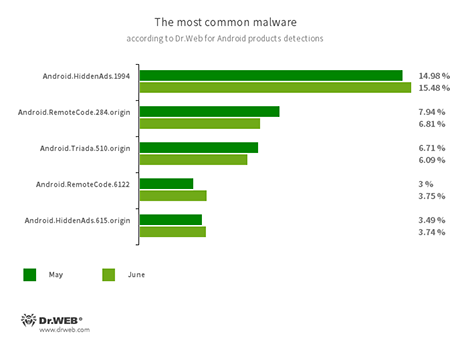
- Android.HiddenAds.1994
- Android.HiddenAds.615.origin
- Trojans designed to display obnoxious ads. They are distributed as harmless applications and, in some cases, are installed in the system directory by other malware.
- Android.RemoteCode.284.origin
- Android.RemoteCode.6122
- Malicious applications that download and execute arbitrary code. Depending on their modification, they can load various websites, open web links, click on advertising banners, subscribe users to premium services, and perform other actions.
- Android.Triada.510.origin
- A multifunctional trojan performing various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family were found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
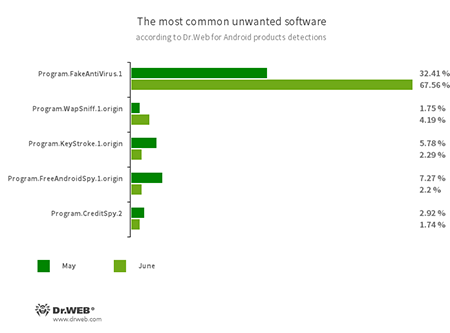
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand they purchase the full version of the software.
- Program.WapSniff.1.origin
- An Android program designed to intercept messages from WhatsApp.
- Program.KeyStroke.1.origin
- An Android application capable of intercepting keystrokes. Some modifications of this software can also track incoming SMS, control calls history and record phone calls.
- Program.FreeAndroidSpy.1.origin
- An application that spies on Android users and can be used for cyber espionage. It controls the location of the device, gains access to a phone book and user contact list, and can also copy multimedia files, such as photos and videos.
- Program.CreditSpy.2
- The detection name for programs designed to assign credit ratings to users based on their personal data. These applications upload SMS, contact information from phonebooks, call history, and other information to the remote server.
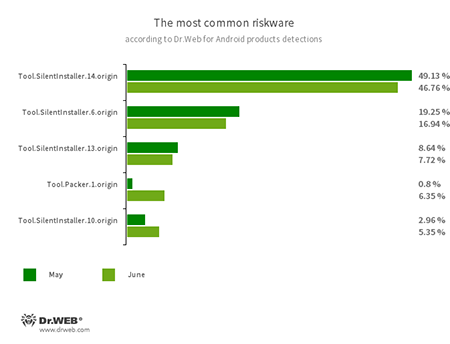
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.10.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from their unauthorized modification and reverse engineering. This tool is not malicious by itself, but it can be used to protect both harmless and malicious software.
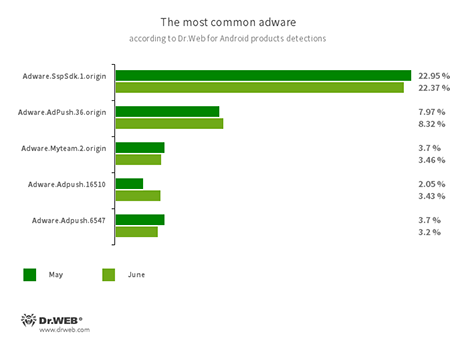
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts and load websites.
- Adware.SspSdk.1.origin
- Adware.Adpush.36.origin
- Adware.Adpush.16510
- Adware.Adpush.6547
- Adware.Myteam.2.origin
Threats on Google Play
Along with stealer trojans that hijack Facebook logins and passwords, Doctor Web’s specialists also uncovered other malicious applications on Google Play. The Android.Joker.758 and Android.Joker.766 trojans subscribing victims to paid mobile services and capable of executing arbitrary code were among them. The former was spread as a video editing app, while the latter was distributed as an image collection app for changing the Android home screen looks.
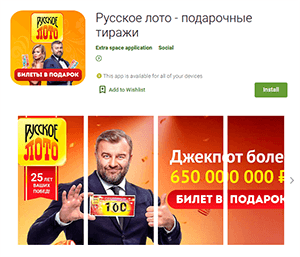
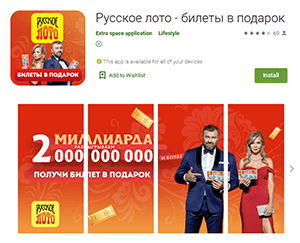
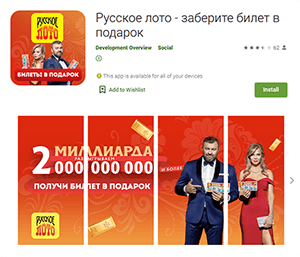
Other trojans belonged to the Android.FakeApp malware family of fake apps that were distributed under the guise of various legitimate software. For example, malicious actors passed off the Android.FakeApp.278, Android.FakeApp.279, Android.FakeApp.294, Android.FakeApp.295, Android.FakeApp.296, and Android.FakeApp.298 trojans as official «Русское лото» (Russian Lotto) lottery apps that allegedly could allow users to receive free lottery tickets and get information about draws.
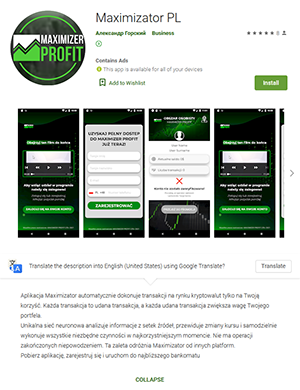
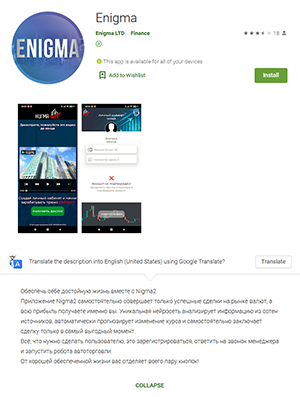
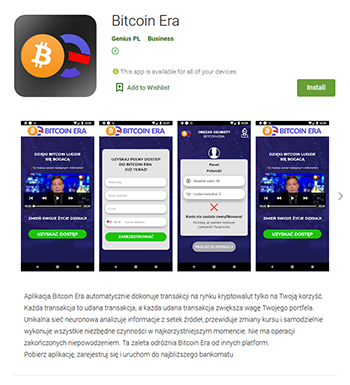
On the other hand, the Android.FakeApp.280, Android.FakeApp.281, Android.FakeApp.282, Android.FakeApp.283, Android.FakeApp.284, Android.FakeApp.285, and Android.FakeApp.286 trojans were spread under the guise of software that was allegedly designed to make money on financial and commodities markets; for example, by trading currency, oil, natural gas, and cryptocurrencies.
According to the developers’, these apps made “automatic successful deals”. Users were only required to register and contact a “manager”. Some of these applications were allegedly created with the support of the government and the president of the Russian Federation. At the same time, part of the apps was oriented to users from other countries as well, such as Poland. In reality, these fake apps didn’t provide the advertised functionality and only lured victims to scammers by loading dubious and phishing sites.
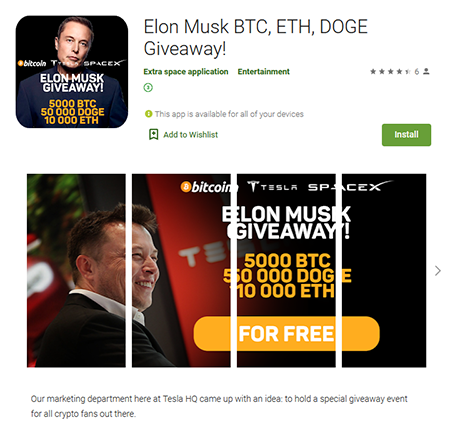
Another “financial” software that was added to the Dr.Web virus base as Android.FakeApp.277 was distributed as an Elon Musk-backed investment app. When launched, this app tempted victims to “double” the amount of cryptocurrency they had by sending it to “Tesla” company wallets. However, this trojan had no connection with Tesla or its owner. In reality, the users that were tricked by this scam only sent their cryptocurrency to the scammers.
Another trojan dubbed Android.FakeApp.297 was spread as digital wallet software. Similar to other fake apps, this malicious application loaded fraudulent sites.
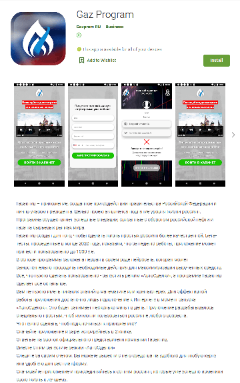
Moreover, new fake apps allegedly designed to help users find the information about payments, allowances and compensations, and receive financial support from the Russian government were discovered. Dr.Web anti-virus products for Android detect them as Android.FakeApp.291, Android.FakeApp.292, and Android.FakeApp.293.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products