Doctor Web’s annual virus activity review for 2020
January 19, 2021
In 2020, one of the most common threats users faced en masse were trojan droppers, which distribute and install other malware and numerous advertising applications that interfere with the normal functioning of devices. Various modifications of trojan downloaders running executable files with a set of malicious functions were also a common threat. In addition, hacker groups were actively distributing trojan programs that exploit the functionality of popular remote desktop software. The Doctor Web virus laboratory registered several RAT malware attacks, which allows attackers to remotely control infected computers and deliver a malicious payload.
Also this year, Doctor Web analysts investigated several large-scale, targeted attacks aimed at the corporate sector. During the investigation, several trojan families that infected the computers of various state institutions were discovered.
The most active threats among mail traffic included banking trojans, stealers, various modifications of backdoors written in VB.NET, as well as malicious scripts that redirected users to dangerous and unwanted websites. The attackers also used email to actively distribute programs that exploit vulnerabilities in Microsoft Office documents.
Even though most of the detected malware targeted Windows users, computer owners operating macOS were also at risk. During the year, macOS users were continually threatened by trojan encoders, spyware and rootkits that hid running processes. Disguised as various common and even useful applications, adware installers were also actively distributed. They functioned to place potentially dangerous payload onto computers. Users who disabled the built-in security systems and downloaded applications from untrusted sources were most at risk.
Android mobile device users were also threatened by adware, spyware and banking trojans, as well as all sorts of malicious droppers that downloaded other malicious applications and executed arbitrary code. Much of the malware was distributed via the Google Play catalog.
Principal trends of the year
- A growing number of targeted attacks, including those involving ransomware
- An increase in the number of phishing attacks and campaigns using social engineering
- New threats to macOS
- Rapid distribution of Android malware throughout Google Play
Most notable events of 2020
In February, Doctor Web virus analysts reported that the VSDC video editor’s download link had been compromised on the popular software platform CNET. Instead of the genuine program, visitors received a modified installer bundled with malicious software, allowing cybercriminals to access the infected computers remotely. The remote access was accomplished using the TeamViewer components and the BackDoor.TeamViewer malicious library, which established an unauthorized connection. Using the backdoor, attackers were able to deliver payload as other malicious applications to infected devices.
In March, Doctor Web virus analysts reported that certain websites, from blogs to corporate pages created using WordPress CMS, had been compromised. The JavaScript script embedded in the hacked pages’ code redirected visitors to a phishing site where they were prompted to install an important security update for Chrome. The downloadable file was a malware installer that allowed attackers to remotely access and control the infected computers. This time, attackers again used legitimate TeamViewer components with a trojan library that established a connection and concealed the running program.
In the summer 2020, the Doctor Web virus laboratory released a large-scale study of malware used in APT attacks on government institutions in Kazakhstan and Kyrgyzstan. During the investigation, analysts discovered a previously unknown family of multi-module trojan programs called XPath, designed to gain entry into computers and then perform various malicious actions at the command of intruders. The trojan used a complex infection mechanism in which each program component corresponds to a specific stage of malware operation. The XPath family also has a rootkit for hiding network activity and any trace of its presence within a compromised system.
The Doctor Web virus laboratory later received new samples of malware found on the infected computers in the local network of a Kyrgyzstan state institution. The most interesting finding was a multi-module backdoor called ShadowPad, which according to our data, may be an evolution of another multi-module APT backdoor — PlugX, also previously found lurking in compromised state networks. Code similarities between the ShadowPad and PlugX malware samples, as well as some intersections in their network infrastructure, were covered in a separate study.
In September, Doctor Web reported the detection of a spear phishing campaign using social engineering, aimed at several Russian fuel and energy companies. For the initial infection, attackers used emails with malicious attachments. Upon being opened, backdoors were installed that allowed cybercriminals to take control of infected computers. Analysis of documents, malware, and the infrastructure used allowed us to conclude one of the Chinese APT groups carried out the attack.
In November, Doctor Web virus analysts detected a phishing attack targeting corporate users. The emails in question contained trojan malware that covertly install and launch Remote Utilities software. The software components were also included in the attachment. The attackers used social engineering to trick possible victims into opening the malicious attachments.
This email was disguised as an official notification requesting the recipient appear at the Prosecutor's office for investigative actions in a criminal case.
Malware landscape
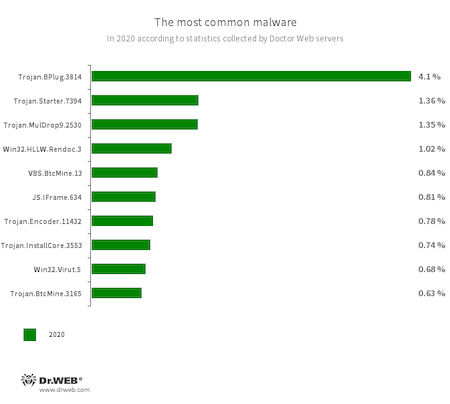
Analysis of Dr.Web’s statistics showed that in 2020, users were most often exposed to trojan droppers and downloaders that installed other malicious applications and executed arbitrary code. Additionally, trojans and scripts that covertly mine cryptocurrency on devices continued to threaten users.
- Trojan.BPlug.3867
- A malicious browser extension designed to perform web injections into viewed webpages and block third-party advertisements.
- Trojan.Starter.7394
- A trojan whose main purpose is to launch an executable file with a specific set of malicious functions within an infected system.
- Trojan.MulDrop9.2530
- A trojan dropper that distributes and installs malware.
- Win32.HLLW.Rendoc.3
- A network worm that, among other channels, spreads via removable storage media.
- VBS.BtcMine.13
- A malicious script written in VBS and designed to covertly mine cryptocurrencies.
- JS.IFrame.634
- A script incorporated into HTML pages. Upon opening these pages, the script redirects users to malicious or unwanted websites.
- Trojan.Encoder.11432
- A multi-component network worm known as WannaCry. The malicious program itself has several components; the trojan encoder is only one of them.
- Trojan.InstallCore.3553
- A family of obfuscated installers that uses unscrupulous methods to distribute the bundled software.
- Win32.Virut.5
- A polymorphic virus that infects executable files. It functions for managing infected computers using IRC channel.
- Trojan.BtcMine.3165
- A trojan program that silently mines cryptocurrency using the computing power of the infected devices.
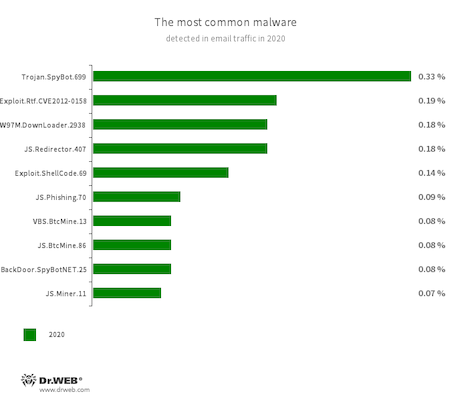
Email traffic was dominated by bankers, backdoors and malware that exploit vulnerabilities in Microsoft Office programs. In addition, cybercriminals distributed scripts for concealed mining, as well as for phishing and redirecting users to unwanted and potentially dangerous sites.
- Trojan.SpyBot.699
- A multi-module banking trojan that allows cybercriminals to download and launch various applications on an infected device and run arbitrary code.
- Exploit.CVE-2012-0158
- A modified Microsoft Office document that exploits the CVE-2012-0158 vulnerability in order to run malicious code.
- W97M.DownLoader.2938
- A family of downloader trojans that exploits vulnerabilities in Microsoft Office documents and can download other malicious programs onto a compromised computer.
- JS.Redirector.407
- Malicious JavaScript script placed in the code of web pages. It is designed to redirect users to phishing or advertising sites.
- Exploit.ShellCode.69
- A malicious Microsoft Office Word document that exploits the CVE-2017-11882 vulnerability.
- JS.Phishing.70
- Malicious JavaScript script that generates a phishing web page.
- VBS.BtcMine.13
- A malicious script written in VBS and designed to covertly mine cryptocurrencies.
- JS.BtcMine.86
- A malicious script written in JavaScript and designed to covertly mine cryptocurrencies.
- BackDoor.SpyBotNET.25
- A backdoor written in .NET and designed to operate with a file system (to copy, create, delete, etc. catalogs), terminate processes, and take screenshots.
- JS.Miner.11
- A family of JavaScript scripts designed to covertly mine cryptocurrencies.
Encryption ransomware
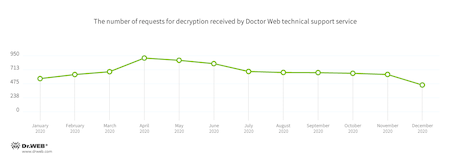
In 2020, Doctor Web’s virus laboratory registered 18.4% fewer requests to decode files encoded by trojan ransomware than in 2019. See the request dynamics for 2020 below.
The most common ransomware programs in 2020:
- Trojan.Encoder.26996
- A trojan encoder known as STOP Ransomware. It attempts to obtain a private key from the server, and in cases of failure, uses the hardcoded one. It is one of the few encoders that encrypts user data with the Salsa20 stream cipher.
- Trojan.Encoder.567
- A trojan encoder written in Delphi. This encoder has many versions that use various encryption algorithms. Generally it is distributed as email attachments.
- Trojan.Encoder.29750
- This trojan encoder belongs to the Limbo/Lazarus family. It carries the hardcoded key, which is used when it is not possible to connect to the C&C server and upload the private portion of the generated key.
- Trojan.Encoder.858
- A trojan encoder known as Troldesh Ransomware. It is compiled using Tor, which is initialized immediately upon launch. The connection is made to one of the bridges, the address of which is hardcoded into the trojan. It uses the AES algorithm in CBC mode to encrypt user data.
- Trojan.Encoder.11464
- A trojan encoder known as Scarab Ransomware. It was first discovered in June 2017. It was initially distributed via the Necurs botnet. It uses the AES-256 and RSA-2048 algorithms to encrypt user data.
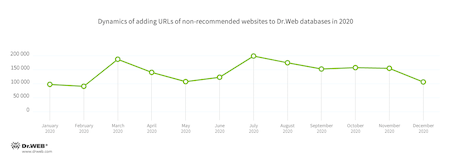
Dangerous and non-recommended websites
SpIDer Gate's Parental (Office) Control and Web Antivirus databases are regularly updated with new addresses of non-recommended and potentially dangerous websites. Many fraudulent and phishing resources, as well as malware distributing pages can be found there. The largest number of such websites was recorded in the third quarter, dropping to the lowest in the second quarter. See the dynamics of the updates to the databases over the last year below.
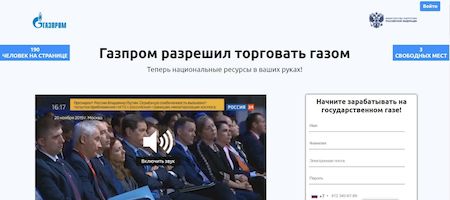
Network fraud
In February, Doctor Web experts warned users about the launch of a large-scale phishing campaign on Instagram. The campaign was based on messages to users about a one-off payment to all Russian citizens. Fraudsters provided information as extracts from news releases, using relevant fragments from real broadcasts. With that, the advertising video has additional frames showing someone using a phishing website and browsing its pages, which were presented as official resources from the Russian Ministry of Economic Development.
During 2020, Doctor Web’s Internet analysts identified numerous fraudulent websites presented as official resources of state organizations. Cybercriminals most commonly offered non-existent compensation to targets or proposed that they invest in large companies.
To get the promised benefits, visitors were most often coaxed into entering their personal data including banking card details and proceed with the advance payment. Thus, victims lost money and unknowingly transferred their personal data to scammers.
Mobile devices
In 2020, Android devices users were threatened by various malicious and unwanted applications. For example, users often encountered all modifications of adware trojans displaying obnoxious notifications and banners. Many malicious programs of the Android.HiddenAds family were distributed via the Google Play catalog, including other channels. During the year, Doctor Web’s virus analysts identified dozens of these trojans on Google Play, which were downloaded by more than 3,300,000 users. Malicious applications of this type accounted for more than 13% of the total number of threats detected on Android devices.
In addition, in March, virus analysts discovered a multifunctional trojan on Google Play — Android.Circle.1, which received commands using BeanShell scripts and could also display ads. It was able to follow the links to download websites and click on banners placed there. Subsequently, the virus laboratory found other malware from this family.
Various trojan downloaders were also a common threat. They included a large number of malicious apps from the Android.RemoteCode family that downloaded and executed arbitrary code. This type of malware accounted for more than 14% of the total number of threats detected by Dr.Web on Android devices. In addition, trojans of the Android.DownLoader and Android.Triada families, which were able to download and install other applications, also threatended Android device users.
Potentially dangerous utilities that allow apps to run without installation were also widespread. They included the Tool.SilentInstaller and Tool.VirtualApk utilities. Malware creators actively used these tools to distribute various software, receiving rewards from partner services.
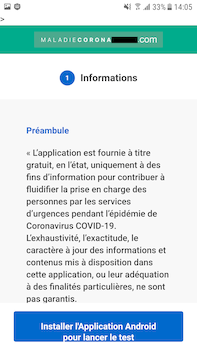
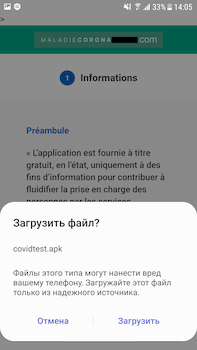
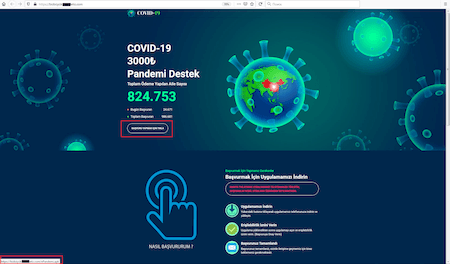
To spread malicious and unwanted applications, cybercriminals actively exploited the COVID-19 pandemic. For example, they created various fraudulent websites where victims were tricked into installing reference or medical apps related to the coronavirus, as well as applications for obtaining welfare assistance. In fact, spyware, various bankers, ransomware, and other malware were downloaded from such websites to the Android devices.
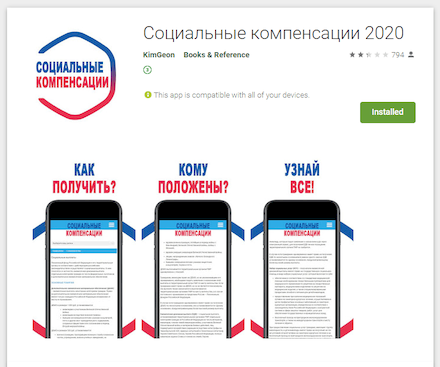
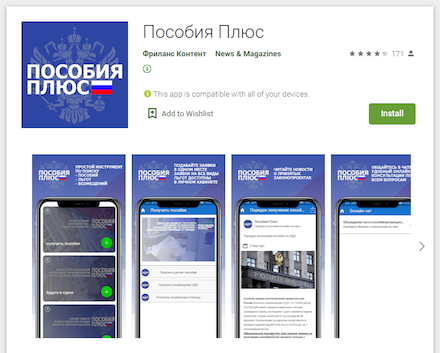
During the year, Doctor Web’s virus analysts identified many malicious applications of the Android.FakeApp family, designed to load fraudulent websites, in the Google Play catalog. The attackers passed off these trojans as reference books with information about social payments and compensation. Given the pandemic and the harsh economic situation, users were naturally interested in this kind of information, and many Android device users fell for the trick.
Also in 2020, the virus laboratory uncovered numerous Android applications that enable owner tracking. These apps could be used for cyber espionage and collecting a wide range of personal information — from correspondence, photos and documents, to personal contact lists, device location, contact information, phone conversations, etc.
Prospects and possible trends
The past year has demonstrated the steady spread of not only mass malware, but also APT threats faced by organizations worldwide.
Digital ransomware is expected to continue spreading in 2021, with targeted attacks using encryption ransomware increasingly targeting private companies and the corporate sector. The expansion of the RaaS model (Ransomware as a Service) has facilitated this development. Possible reductions in information security costs may also lead to the number of such incidents rising rapidly.
Banking and adware trojans, miners and encoders, as well as spyware will continue to threaten users in 2021. Besides that, new fraudulent schemes and phishing campaigns are likely to emerge with the help of attackers who will try to obtain money and personal data.
Owners of devices running macOS, Android, Linux, and other OS will remain targets and malware will continue to spread to these platforms. Attacks on IoT devices are also expected to become more frequent and sophisticated. So, it’s safe to say that cybercriminals will continue using any means necessary to continue developing these attacks. That being said, users need to comply with information security rules and apply reliable anti-virus tools on all devices.