Grandmasters of cyber-fraud look for gains: November 2010 virus review from Doctor Web
Virus reviews | All the news | Virus alerts
December 3, 2010
In November cyber-criminals demonstrated even greater creativity than before. As a result, anti-virus vendors and users were confronted with new fraud techniques involving bootkit technologies. New modifications of encoder Trojans targeted European users. Criminals seeking the biggest gains attacked online banking systems.
Windows boot blocker
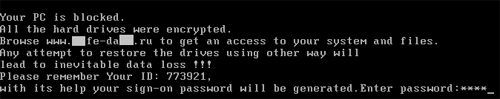
As soon as Trojan.MBRlock.1 appeared in the wild in November, it was employed by cyber-fraudsters. This malicious program is unlike any other malware used to implement fraud schemes.
It bypasses the UAC protection mechanism, so its installation goes unnoticed by users. Once installed, the Trojan writes its code into the MBR and into other nearby disk sectors.
The code, written to the MBR, loads information from the neighbouring disk sectors. The result is a message to users demanding that they pay $100 to unlock their systems.
The message also informs a user that all of the files located on all of the computer’s disks are encrypted. This is not true.
In any event curing the Trojan-compromised system can’t be done from inside the system since it wouldn’t boot.
Entering a correct password restores the MBR after which the installed operating system boots normally.
Currently several modifications of Trojan.MBRlock.1 are known, but Dr.Web detects them as the same piece of malware.
To cure the system, enter an ekol or jail unlock code. If neither works, contact the free Doctor Web technical support service for victims of cyber-fraud.
Certain modifications of Trojan.MBRlock.1 had been detected by the Dr.Web heuristic analyzer as MULDROP.Trojan before a corresponding entry was added to the Dr.Web virus database. Dr.Web users were protected from the Trojan even when no virus definitions for this malicious program were available.
New Trojan encoder
Encoder Trojans drew the public’s attention once again in November. This time criminals targeted European users.
Trojan.Encoder.88 uses the AES-256 encryption algorithm to encrypt documents in many popular formats which complicates decryption. To search all possible decryption keys for one that would help restore files on a single computer, 2^256 operations are required. The resulting number exceeds the number that ends in 77 zeros.
A unique encryption key is generated for each compromised machine. It is encrypted using the RSA algorithm and saved to a disk as a text file.
Origins Tracing technology enabled Dr.Web to detect Trojan.Encoder.88 as Trojan.Encoder.origin even before an entry for this program was added to the database.
Fraud in November: winlocks returned
In November the free technical support service received around 4,700 requests from cyber-fraud victims which constituted 42% of all requests. The daily average of requests amounted to 146 which exceeded the October figure by one third.
Trojan.Winlock became the most widely spread malicious program used for fraud (73% of all requests). A significant number of fraud incidents were related to Trojan.Hosts that blocked access to popular web resources.
Criminals also changed routines for converting their profit into actual money. Malicious programs demanding that users send paid short messages were less popular in November, and the number of requests related to such programs reached only 31% of the total. Meanwhile the option that involves paying criminals via terminals became more appealing to fraudsters (60% of all requests).
Banking Trojans on the offensive
November saw the emergence of new Trojans targeting users of online banking systems, both individuals and businesses.
In particular, several modifications of Trojan.PWS.Ibank.213 were added to the Dr.Web virus database.
Variations of the Trojan serve as containers of malicious payloads. Their most harmful feature is their ability to disable security software components. The Trojan can detect whether it is being launched in a virtual environment where it can be safely analyzed. Disabling the system restore service is also among its malicious capabilities.
To collect the information required to access bank accounts online, the Trojan intercepts certain system routines as well as functions of online banking systems, and stores information entered by a user with a keyboard. The fact that Trojan.PWS.Ibank.213 can communicate with a remote server, and download and launch executable files, shows that systems compromised by this program become nodes of a botnet.
November 2010 showed that criminals can make use of various malicious programs to accomplish a wide variety of tasks. When it comes to neutralizing them, anti-viruses capable of protecting a system from all kinds of malware and of curing it proved to be the most efficient. Yet, it is users who still remain the weakest element of the computer defense system. Doctor Web would like to emphasize once again that following basic information security rules dramatically reduces the probability of system infection.
Viruses detected in e-mail traffic in November
| 01.11.2010 00:00 - 01.12.2010 00:00 | ||
| 1 | Trojan.DownLoader.62844 | 887472 (16.61%) |
| 2 | Trojan.DownLoad1.58681 | 560304 (10.49%) |
| 3 | Trojan.Packed.20878 | 409498 (7.67%) |
| 4 | Win32.HLLW.Texmer.51 | 386408 (7.23%) |
| 5 | Win32.HLLM.Netsky.18401 | 317070 (5.93%) |
| 6 | Trojan.Oficla.zip | 296642 (5.55%) |
| 7 | Win32.HLLM.MyDoom.33808 | 270438 (5.06%) |
| 8 | Trojan.Packed.20312 | 246743 (4.62%) |
| 9 | Trojan.DownLoad.41551 | 231569 (4.33%) |
| 10 | Trojan.Oficla.38 | 139866 (2.62%) |
| 11 | Win32.HLLM.Netsky.35328 | 121814 (2.28%) |
| 12 | Trojan.AVKill.2788 | 103700 (1.94%) |
| 13 | Win32.HLLM.Beagle | 98470 (1.84%) |
| 14 | Trojan.PWS.Panda.114 | 90471 (1.69%) |
| 15 | W97M.Killer | 74444 (1.39%) |
| 16 | Trojan.DownLoader1.17157 | 65832 (1.23%) |
| 17 | Trojan.PWS.Panda.387 | 49461 (0.93%) |
| 18 | Trojan.Oficla.73 | 49351 (0.92%) |
| 19 | Trojan.Oficla.48 | 49342 (0.92%) |
| 20 | Trojan.Botnetlog.zip | 41304 (0.77%) |
| Total scanned: | 40,984,945,769 |
| Infected: | 5,342,395 |
Viruses detected on user machines in November
<| 01.11.2010 00:00 - 01.12.2010 00:00 | ||
| 1 | Win32.HLLP.Neshta | 7665428 (24.91%) |
| 2 | Win32.HLLP.Whboy.45 | 6184396 (20.09%) |
| 3 | Trojan.DownLoader.42350 | 2364188 (7.68%) |
| 4 | Win32.HLLP.Novosel | 1644766 (5.34%) |
| 5 | Win32.HLLP.Rox | 1177270 (3.82%) |
| 6 | Trojan.Click.64310 | 727694 (2.36%) |
| 7 | ACAD.Pasdoc | 610404 (1.98%) |
| 8 | Win32.HLLM.Dref | 520690 (1.69%) |
| 9 | Exploit.Cpllnk | 413622 (1.34%) |
| 10 | VBS.Redlof | 320729 (1.04%) |
| 11 | Trojan.WinSpy.925 | 284258 (0.92%) |
| 12 | Win32.HLLW.Shadow.based | 278980 (0.91%) |
| 13 | Trojan.PWS.Ibank.238 | 252705 (0.82%) |
| 14 | HTTP.Content.Malformed | 244692 (0.80%) |
| 15 | Trojan.MulDrop1.48542 | 183156 (0.60%) |
| 16 | Trojan.Click1.6029 | 180330 (0.59%) |
| 17 | Win32.Sector.22 | 142436 (0.46%) |
| 18 | Win32.HLLW.Kati | 121106 (0.39%) |
| 19 | Trojan.DownLoad.32973 | 114280 (0.37%) |
| 20 | Win32.HLLW.Autoruner.5555 | 100817 (0.33%) |
| Total scanned: | 92,810,136,138 |
| Infected: | 30,778,334 |