Android.Circle.1 adware trojan found on Google Play is capable of executing BeanShell scripts
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
March 24, 2020
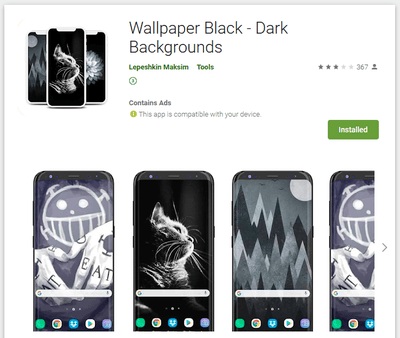
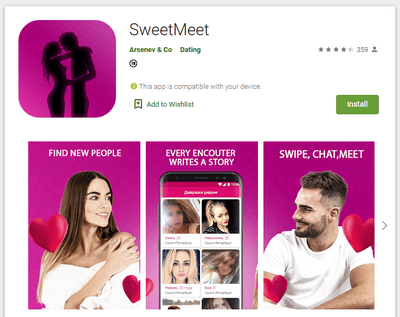
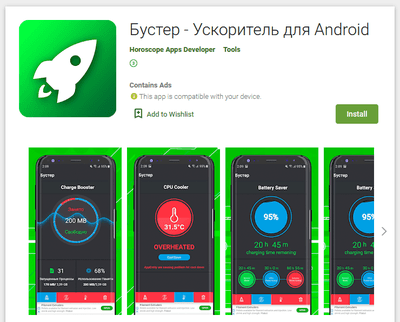
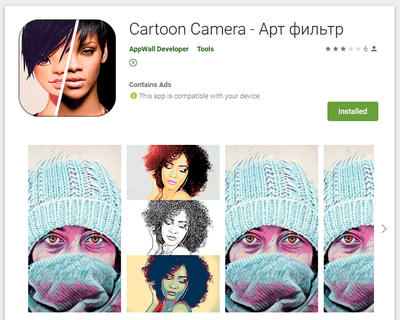
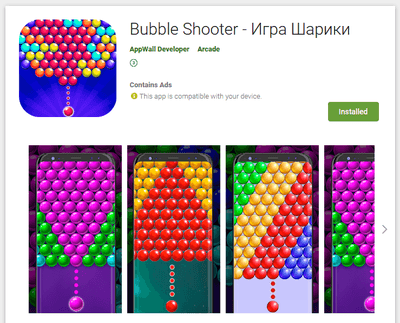
Dubbed Android.Circle.1, the trojan has been spread as wallpaper collections, horoscopes apps, image editors, games, system tools, online dating apps and other software. Our specialists have found 18 modifications of this malware downloaded more than 700,000 times. After Doctor Web’s report to Google, all of them have been deleted from Google Play. Moreover, the C2 server domains have been terminated as well.
Examples of the discovered trojan apps are shown below:
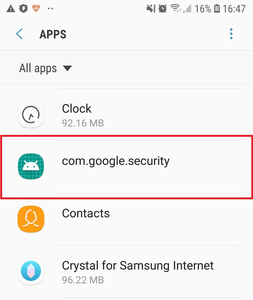
All these apps seemed harmless and worked as advertised, thus, users had no reasons to perceive them as threats. In addition, some of these apps pretended to be an important system component after installation, providing an additional layer of protection from possible deinstallation.
Android.Circle.1 is a bot that performs malicious tasks at the command of cybercriminals. It’s bot functionality is implemented via the built-in open source library BeanShell. This library presents a Java code interpreter with Java-based scripting language capabilities and allows the malware to run arbitrary code “on the fly”. Upon launch, the malware connects to the C2, sends information about the infected device to it and waits for incoming commands.
Android.Circle.1 receives tasks via the Firebase Cloud Messaging service. The trojan saves them into the configuration file and extracts BeanShell scripts with the commands, which it then executes. Doctor Web virus analysts tracked several such commands received by the malware:
- delete the trojan’s app icon from the apps list on the home screen;
- delete the trojan’s app icon and load the URL specified in the command in the browser;
- perform a click action on the loaded website, and
- display an advertisement banner.
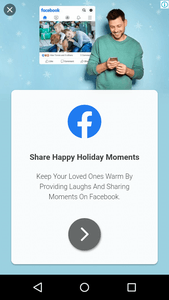
Thereby, the main purpose of Android.Circle.1 1 is to show ads and load various websites where the trojan imitates user actions. For instance, it can click on links, ads and other interactive elements on loaded websites, implementing the clicker functionality.
However, these are not the only functions this bot has. In fact, the trojan can load and execute any arbitrary code it receives. Its capabilities are only limited with system permissions available to the app that the malware is built in. Let the C2 server send the specific command, Android.Circle.1 will be able to load WebView with a fraudulent or malicious website to perform phishing attacks. Herewith, executing the arbitrary code received outside of Google Play is prohibited by the catalogue’s policy.
See the examples of the obnoxious advertisements displayed by the trojan:
Android.Circle.1 is created using the Multiple APKs mechanism. It allows developers to prepare and host multiple versions of a single program on Google Play to support various device models and processor architectures. Thanks to this mechanism, the size of APK files is reduced, since they contain only the necessary components for working on a particular device. At the same time, files with resources, as well as modules and application libraries can be located in separate APK files (the so-called Split APKs mechanism) and may or may not exist at all depending on the target device. Such auxiliary APKs are automatically installed together with the main program package and are perceived by the operating system as a whole.
Part of the malicious functionality of Android.Circle.1 has been taken to the native library, which is located in one of the such auxiliary APK. Therefore, Multiple APKs turns into a kind of self-defense mechanism of the Trojan. If information security specialists find only the main Android.Circle.1 without the rest of the APK files with the components necessary for analysis, studying a malicious application may be significantly difficult or even impossible.
Moreover, in case of a potential targeted attack, it is possible for the attackers to create multiple “clean” variants of an app and build a trojan into only one or a few of them. Malicious modifications will only be installed on specific device models. To other users, the application will remain harmless, which will reduce the chance of timely discovery of the threat.
Even though all discovered Android.Circle.1 modifications have been deleted from the Google Play, it is possible that cybercriminals will create and distribute more versions of the trojan. Therefore, Android users should be vigilant and avoid installing unknown software. Dr.Web for Android Anti-Virus solutions reliably detect and delete Android.Circle.1 from Android devices, keeping our users well protected from this threat.
More details about Android.Circle.1

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products