Dangerous trojan spreads via copied website of Russia’s Federal Bailiffs Service
Real-time threat news | Hot news | All the news | Virus alerts
October 4, 2019
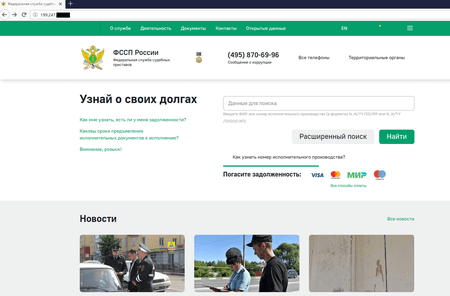
Our experts discovered the copy of Russia’s FSSP website at 199.247.**.***. The fake looks almost no different from the original, but some elements are displayed incorrectly, unlike the official website.
If a user tries to click some of the links, they will be redirected to a page prompting to update Adobe Flash Player. At the same time, an .EXE file will be downloaded to the user's device. If the user launches it, Trojan.DownLoader28.58809 will be installed.
This trojan adds itself to the autorun list in the user's system, connects to the command and control server, and downloads another malicious module, Trojan.Siggen8.50183. In addition, a file with a valid Microsoft digital signature is downloaded to the user's device to run the main malicious library. Then Trojan.Siggen8.50183 collects information about the user's system and sends it to the command and control server. After installation, the trojan will always be active on the user's device and will be able to perform various actions upon a command from the server.
When launched on a victim’s device, the trojan can do the following:
- obtain information about disks;
- obtain information about any file;
- obtain information about any folder (i.e. the number of files, subfolders, and their size);
- obtain the list of files in a specified folder;
- delete a file;
- create a folder;
- move a file;
- run a process;
- stop a process;
- obtain the list of processes.
According to our data, cybercriminals have not yet launched any large-scale virus campaigns using the fake website, but it could be used in attacks aimed at individual users or organizations.
Both of these trojans are successfully detected and removed by Dr.Web products and pose no threat to our users.