Doctor Web: Clicker Trojan Installed from Google Play by Some 102,000,000 Android Users
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
August 8, 2019
The trojan is a malicious module, which, according to Dr.Web classification, was dubbed Android.Click.312.origin. It is built into ordinary applications, such as dictionaries, online maps, audio players, barcode scanners, and other software. All these programs are operable and look harmless to Android users. Additionally, Android.Click.312.origin only starts its malicious activity after 8 hours after launch, so as not to raise suspicion.
Once launched, the trojan sends the following information about the infected device to the C&C server:
- manufacturer and model;
- operating system version;
- user’s country of residence and default system language;
- User-Agent ID;
- mobile carrier;
- internet connection type;
- display parameters;
- time zone;
- data on application containing trojan.
In response, the server sends the necessary settings. Some functions of the malware are using reflection, and the settings contain the names of methods and classes along with the parameters for them. They are used, for example, to register a broadcast receiver and a content observer, which Android.Click.312.origin uses to monitor the installation and updates of applications.
Upon installation of a new application or download of an apk file by the Play Market client, the trojan sends information about this software along with some technical data about the device to the command and control server. In response, Android.Click.312.origin receives website addresses to open in an invisible WebView, as well as links to load in a browser or on Google Play.
Thus, depending on the settings of the command and control server and the instructions it sends, the trojan can not only advertise applications on Google Play, but also covertly load any websites, including advertisements (even videos) or other dubious content. For example, after installing applications with the built-in trojan, users complained about being automatically subscribed to expensive content provider services.
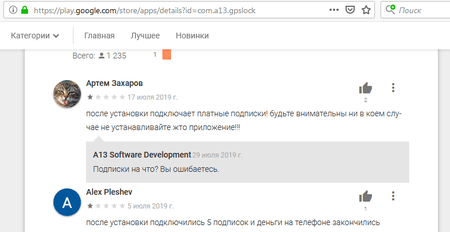
Fig. 1. First user comment: “After installation, it subscribes you to paid services! Be careful, do not install this application!!!”
Developer response: “What services? You're wrong.”
Second user: “After installation, I was subscribed to 5 services and now my phone account is empty.”
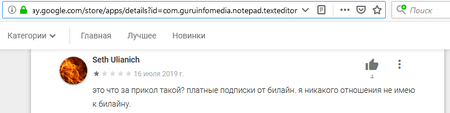
Fig. 2. User comment: “What kind of joke is this? Paid subscriptions to Beeline (Russian mobile carrier). I have nothing to do with Beeline.”
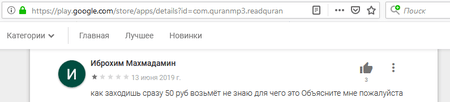
Fig. 3. User comment: “The moment you log in, it deducts 50 rubles. I don’t know what it is for, please explain.”
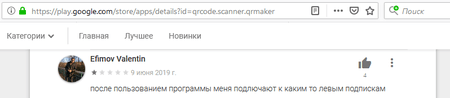
Fig. 4. User comment: “After I use the app, they subscribe me to some shady services.”
Doctor Web specialists were unable to recreate the conditions for the trojan to open such websites. However, in the case of Android.Click.312.origin, this fraudulent scheme can potentially be implemented quite simply. Since the trojan informs the command and control server about the current Internet connection type, the server can send a command to open a website of a partner service that supports the WAP-Click technology if the device is connected to the Internet via a mobile carrier. This technology simplifies the subscription to various premium services, but it is often used illegally. Our company covered this problem in 2017 and 2018. In some cases, no confirmation from the user is required to subscribe to an unnecessary service: it can be done by a script on the same page, or even the trojan than can “click” the confirmation button. Since Android.Click.312.origin opens pages in an invisible WebView, the whole procedure can be done without the victim’s knowledge.
Doctor Web virus analysts have identified 34 applications with the embedded Android.Click.312.origin. They were installed by over 51.7 million users. Additionally, the trojan’s modification, dubbed Android.Click.313.origin, was downloaded by at least 50 million people. Thus, the total number of mobile device owners threatened by this trojan, exceeded 101.7 million. See below the list of programs, where this clicker was found:
| GPS Fix |
| QR Code Reader |
| ai.type Free Emoji Keyboard |
| Cricket Mazza Live Line |
| English Urdu Dictionary Offline - Learn English |
| EMI Calculator - Loan & Finance Planner |
| Pedometer Step Counter - Fitness Tracker |
| Route Finder |
| PDF Viewer - EBook Reader |
| GPS Speedometer |
| GPS Speedometer PRO |
| Notepad - Text Editor |
| Notepad - Text Editor PRO |
| Who unfriended me? |
| Who deleted me? |
| GPS Route Finder & Transit: Maps Navigation Live |
| Muslim Prayer Times & Qibla Compass |
| Qibla Compass - Prayer Times, Quran, Kalma, Azan |
| Full Quran MP3 - 50+ Audio Translation & Languages |
| Al Quran Mp3 - 50 Reciters & Translation Audio |
| Prayer Times: Azan, Quran, Qibla Compass |
| Ramadan Times: Muslim Prayers, Duas, Azan & Qibla |
| OK Google Voice Commands (Guide) |
| Sikh World - Nitnem & Live Gurbani Radio |
| 1300 Math Formulas Mega Pack |
| Обществознание - школьный курс. ЕГЭ и ОГЭ (Social Sciences - School Curriculum. State Uniform Examinations, Basic State Examinations.) |
| Bombuj - Filmy a seriály zadarmo |
| Video to MP3 Converter, RINGTONE Maker, MP3 Cutter |
| Power VPN Free VPN |
| Earth Live Cam - Public Webcams Online |
| QR & Barcode Scanner |
| Remove Object from Photo - Unwanted Object Remover |
| Cover art IRCTC Train PNR Status, NTES Rail Running Status |
Doctor Web informed Google about this trojan, and some applications we had detected were quickly removed from Google Play. Additionally, several applications have been updated, removing the malicious component. However, at the time of this publication, most applications still contained a malicious module and remained available for download.
Virus analysts recommend that developers responsibly choose modules to monetize their applications and not integrate dubious SDKs into their software. Dr.Web for Android successfully detects and removes applications that have the known modifications of Android.Click.312.origin embedded into them, so it poses no threat to our users.
Read more about Android.Click.312.origin
#Android, #Google_Play, #clicker