Doctor Web’s overview of virus activity on mobile devices in July 2019
August 5, 2019
Last month Doctor Web reported the dangerous Android.Backdoor.736.origin trojan that executed malicious commands, stole confidential data and displayed fraudulent windows and messages. In July, malware analysts discovered many new adware trojans of the Android.HiddenAds family on Google Play. The Dr.Web virus database has also been updated to detect the unwanted adware Adware.HiddenAds.9.origin, as well as the spyware trojans Android.Spy.567.origin and Android.Spy.568.origin.
PRINCIPAL TRENDS IN JULY
- Distribution of an Android backdoor that was spying on users and executing commands from cybercriminals
- Detection of new trojans and unwanted applications on Google Play
- Distribution of spyware trojans
Mobile threat of the month
In mid-July, Doctor Web virus analysts investigated the Android.Backdoor.736.origin trojan, spreading under the guise of OpenGL Plugin software. It allegedly checked the version of the OpenGL ES interface and installed its updates.
This backdoor spied on users, sending information about their contacts, phone calls, and their device location to the attackers. It also uploaded files from devices to a remote server, as well as download and installed software. Features of Android.Backdoor.736.origin:
- the main malicious component of the trojan was hiding in an auxiliary module, encrypted and stored in the application’s resource directory;
- with root privileges, it could automatically install software;
- could execute shell commands, received from the C&C server.
For more information regarding Android.Backdoor.736.origin, refer to the news article on our website.
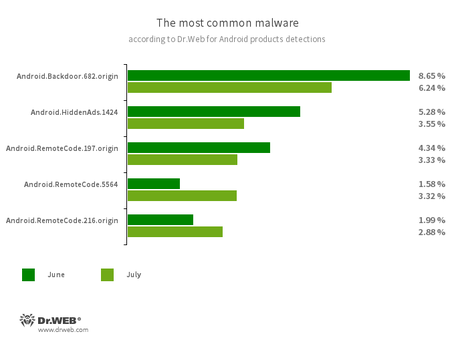
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- A trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.HiddenAds.1424
- A trojan designed to display obnoxious ads. It is distributed under the guise of popular applications.
- Android.RemoteCode.197.origin
- Android.RemoteCode.5564
- Android.RemoteCode.216.origin
- Malicious applications designed to download and execute arbitrary code.
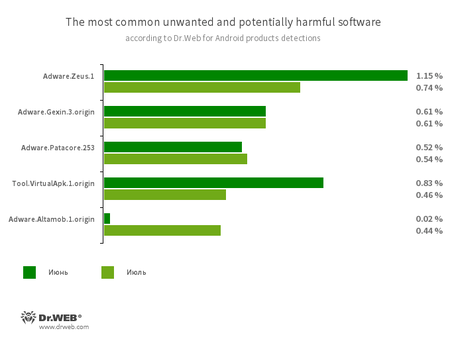
Program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices:
- Adware.Zeus.1
- Adware.Gexin.3.origin
- Adware.Patacore.253
- Adware.Altamob.1.origin
A riskware platform that allows applications to launch APK files without installing them:
- Tool.VirtualApk.1.origin
Threats on Google Play
Since the beginning of July, Doctor Web malware analysts have detected many new adware trojans of the Android.HiddenAds family on Google Play, installed by over 8.2 million users. These malware spread under the guise of harmless games and useful applications, such as camera filters, system utilities, alarm clocks, etc. After launching, the trojans hid their icons from the software list on the main screen and started displaying banners that interfered with device operation.
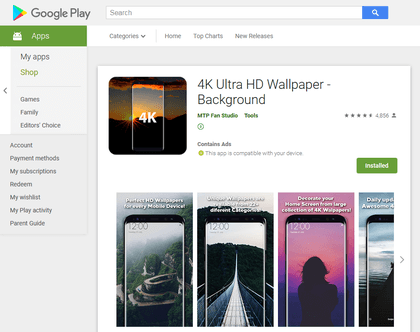
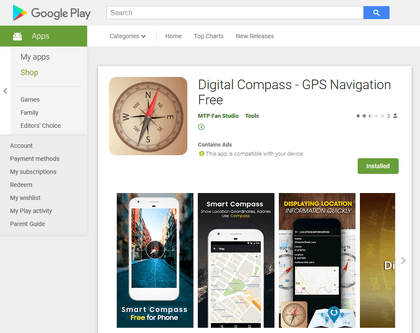
In addition, a new unwanted advertising module named Adware.HiddenAds.9.origin was uncovered. It was embedded into the compass software and a collection of wallpapers for the desktop. It displayed ads even when these applications were closed.
Cyberespionage
Last month, the Dr.Web virus database was also updated to detect the spyware trojans Android.Spy.567.origin and Android.Spy.568.origin. The first one transferred the data from text messages, phone calls, calendar, and phone book entries to a remote server, as well as information about files stored on the device.
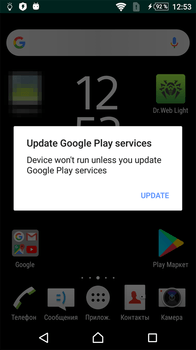
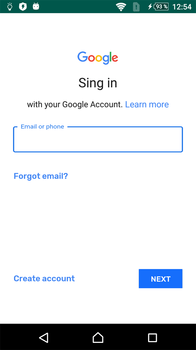
The second one displayed a fraudulent message, prompting a potential victim to update a Google Play component. If the user agreed, the trojan displayed a phishing window that simulated a Google account login page.
Virus writers made a spelling mistake in the phrase “Sign in”, which could indicate a fake. If the victim did not notice this and logged into the account, Android.Spy.568.origin stole the data of the current session, and the attackers gained access to confidential information, such as calendar entries, verification codes, phone numbers, and email addresses to restore access to the account.
To protect your Android device from malware and unwanted programs, we recommend you install Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products