Risks and Threats of the Internet of Things (IoT)
Hot news | All the news | Virus alerts
August 7, 2019
Introduction
In addition to computers, smartphones, tablets, and routers, the World Wide Web now increasingly covers smart TVs, surveillance cameras, smart watches, refrigerators, cars, fitness trackers, video recorders, and even children's toys. The number of IoT devices already exceeds several billion, and this number is growing every year.
Many of them are badly or not at all protected from attacks. For example, they can be connected using simple or well-known credentials, set for hundreds of thousands of models by default. The owners either do not think about changing the factory settings, or are not able to do this due to restricted access. Cybercriminals can relatively easy access such devices by matching combinations from a dictionary (the so-called brute force method). They can also exploit the vulnerabilities of the operating systems.
Since 2016, Doctor Web have been closely following the threats of the Internet of Things. To do this, our experts have set up a network of baits, i.e. honeypots. They imitate various types of smart devices and record attempts to infect them. Honeypots cover several hardware platforms, including ARM, MIPS, MIPSEL, PowerPC, and Intel x86_64. They allow us to monitor attack vectors, detect and research new malware samples, improve the detection mechanisms, and deal with attacks more effectively.
This article dwells on the identified smart device-targeted attacks, as well as the most common IoT threats.
Statistics
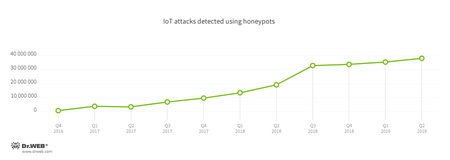
When they only started the monitoring, our malware analysts recorded a relatively low activity of malware aimed at IoT devices. In the first four months of 2016, Doctor Web experts detected 729,590 attacks. However, the number grew 32-fold over a year, hitting 23,741,581. Twelve months later, the figure rose to 99,199,444. Now, the first half of the current year already saw 73,513,303 attacks, almost as many as the entire 2018.
The patterns of attack detection by honeypots is shown on the diagram:
In less than three years, the number of hacking attempts and infecting the IoT devices has increased by 13,497%.
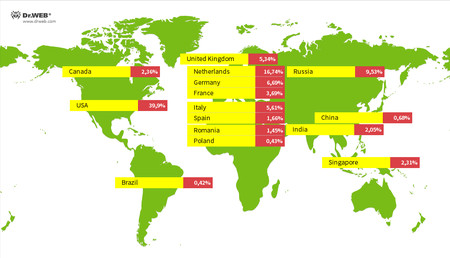
Smart devices were targeted from IP addresses in more than 50 countries. Most attempts were made from the US, the Netherlands, Russia, Germany, Italy, the United Kingdom, France, Canada, Singapore, India, Spain, Romania, China, Poland, and Brazil.
The geographic spread of attack sources and the percentage is shown on this diagram:
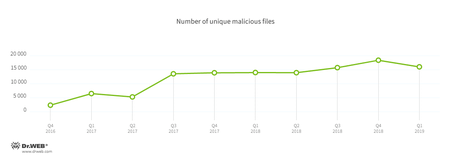
After compromising the devices, cybercriminals downloaded one or several trojans onto them. The total number of unique malicious files detected by our traps during the observation period was 131,412. The detection patterns are shown below.
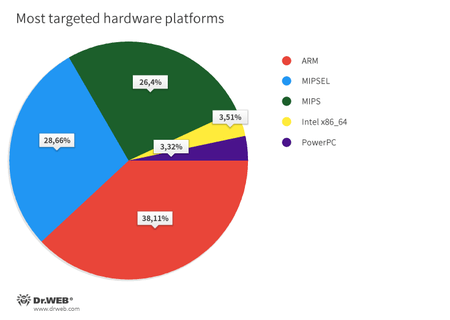
Smart devices run on different processor architectures, and malware often has versions for several hardware platforms at once. Among those mimicked by our honeypots, devices with ARM, MIPSEL, and MIPS processors are targeted more often than the others. This is clearly seen on the diagram:
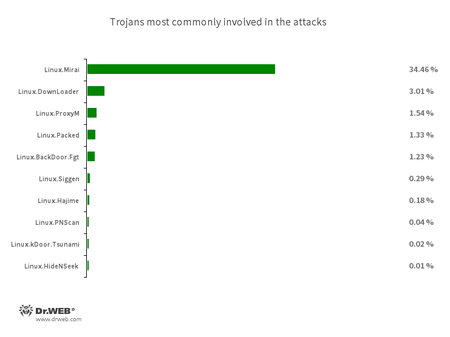
According to statistics gathered by honeypots, the most active malware is the Linux.Mirai family, responsible for over 34% of attacks. They are followed by Linux.DownLoader (3% of attacks) and the Linux.ProxyM trojans (1.5% of attacks). The Linux.Hajime, Linux.BackDoor.Fgt, Linux.PNScan, Linux.BackDoor.Tsunami, and Linux.HideNSeek malware are also ranked among the top ten. This figure shows the percentage of the most active trojans:
Malicious code that targets smart devices falls under several basic categories according to the main features:
- DDoS trojans (such as Linux.Mirai);
- trojans that distribute, download, and install other malware and components (such as Linux.DownLoader, Linux.MulDrop);
- trojans that enable the remote control of the infected devices (such as Linux.BackDoor);
- trojans that turn devices into proxy servers (such as Linux.ProxyM, Linux.Ellipsis.1, Linux.LuaBot);
- trojans for cryptocurrency mining (such as Linux.BtcMine);
- others.
However, most malware pose multifunctional threats, since many of them can combine several functions at once.
Threat Trends for Smart Devices
- Due to the availability of trojan source codes, such as Linux.Mirai, Linux.BackDoor.Fgt, Linux.BackDoor.Tsunami, and others, the number of new malware is growing.
- A growing number of malicious applications in non-trivial programming languages, such as Go and Rust.
- Cybercriminals have access to information about many vulnerabilities that can be exploited to infect smart devices.
- The persisting popularity of cryptocurrency miners (mainly Monero) for IoT devices.
See the information below on the most common and notable IoT trojans.
More on IoT Threats
Linux.Mirai
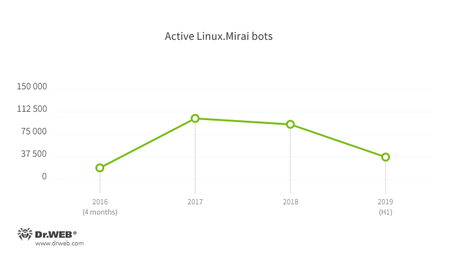
Linux.Mirai is one of the most active trojans targeting IoT devices. The first version of this malware appeared in May 2016. Then, its source codes were published in open, quickly introducing a large number of modifications by various virus writers. Now Linux.Mirai is the most common trojan for Linux, which works on many processor architectures, such as x86, ARM, MIPS, SPARC, SH-4, M68K, etc.
After infecting the target device, Linux.Mirai connects to the command and control server and waits for further commands. Its main function is to perform DDoS attacks.
The following diagram shows the patterns of detecting active copies of this malware by honeypots:
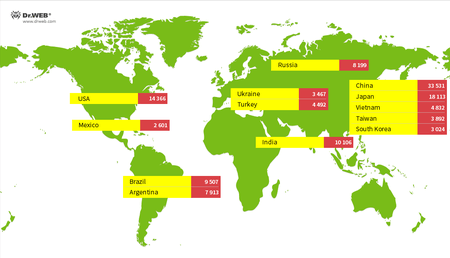
Modifications of Linux.Mirai are the most active in China, Japan, USA, India, and Brazil. Below are the countries with the highest number of bots of this family detected during observation.
Linux.Hajime
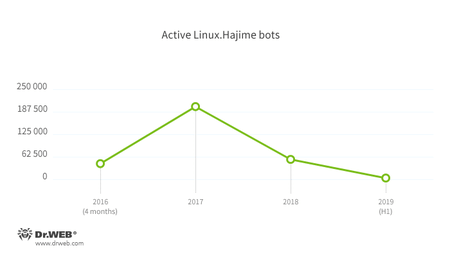
Another dangerous malware for smart devices is Linux.Hajime. This trojan has been known to virus analysts since late 2016. It works on ARM, MIPS, and MIPSEL architectures and acts as a worm, using the Telnet protocol to spread. Infected devices become part of a decentralized P2P botnet and are used to infect other available online objects. The malware blocks the access to the compromised devices for other malicious software, closing ports 23, 7547, 5555, and 5358.
The peak of Linux.Hajime activity was in late 2016—early 2017, when the number of simultaneously active copies of trojans of this family exceeded 43,000. After that, the activity of this malware dropped and keeps gradually decreasing. Now, the number of active Linux.Hajime bots is no more than a few hundred.
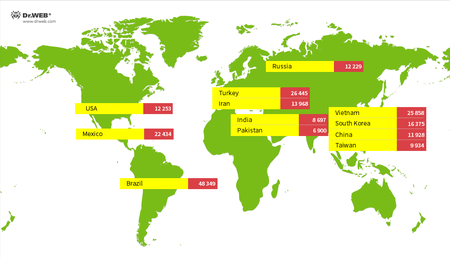
These trojans are most common in Brazil, Turkey, Vietnam, Mexico, and South Korea. The map shows the countries with the largest number of active Linux.Hajime trojans, recorded during the entire observation period.
Linux.BackDoor.Fgt
The top five trojans designed for IoT devices include Linux.BackDoor.Fgt, which has been spreading since autumn 2015. Its different versions support MIPS, SPARC, and other architectures and run on Linux. Linux.BackDoor.Fgt source code is publicly available, which is why it is so popular among virus writers.
These backdoors are distributed via the Telnet and SSH protocols, brute-forcing credentials to access the objects. The main purpose of these trojans is to perform DDoS attacks and remotely monitor the infected devices.
Linux.ProxyM
Linux.ProxyM trojan is one of the malware that cybercriminals use to stay anonymous on the Internet. It runs a SOCKS proxy server on infected Linux devices, using it to transfer the network traffic of cybercriminals. Doctor Web specialists discovered the first versions of Linux.ProxyM in February 2017, and this trojan is still active.
Linux.Ellipsis.1
Linux.Ellipsis.1 is another trojan designed to transform IoT devices and Linux computers into proxy servers. It was detected by Doctor Web analysts in 2015. Once launched, it deletes the log files and prevents the device from creating new ones, deletes some system utilities, and also blocks access to certain IP addresses. If the trojan detects suspicious traffic from one of the IP addresses, it also blacklists the IP. Linux.Ellipsis.1 can also terminate applications connecting to the forbidden addresses at the command of the C&C server.
Linux.LuaBot
Doctor Web has discovered the first versions of the Linux.LuaBot family of trojans in 2016. These malware are written in the Lua scripting language and support devices with the Intel x86_64, MIPS, MIPSEL, Power PC, ARM, SPARC, SH4 and M68k architectures. They consist of several dozen modules, each for a specific task. The trojans can receive updates for these modules from the C&C server, as well as download new ones. Linux.LuaBot are multifunctional. Depending on the modification and the set of scripts, cybercriminals can use them to remotely control the infected devices, as well as create proxy servers to anonymize themselves on the Internet.
Linux.BtcMine.174
Cryptocurrency mining is one of the main reasons for infecting IoT devices for cybercriminals. The Linux.BtcMine family of trojans and other malware help them with this. One of them, Linux.BtcMine.174, was detected by Doctor Web experts in late 2018. It mines Monero (XMR). Linux.BtcMine.174 is a shell script. If it was not launched with root privileges, the trojan attempts to elevate its privileges using several exploits.
Linux.BtcMine.174 searches for anti-malware processes and attempts to terminate them, as well as remove their files from the device. Then it downloads and launches several additional components, including a backdoor and a rootkit module, then launches a miner on the system.
The trojan adds itself to autorun, so that rebooting of the infected device does not help. It also keeps checking whether the mining software process is active. If necessary, the trojan initiates it again, ensuring that cryptocurrency is mined at all times.
Linux.MulDrop.14
The Linux.MulDrop trojan family is used to distribute and install other malware. They work on many hardware architectures and device types. In 2017, Dr.Web virus analysts discovered the Linux.MulDrop.14 trojan that purposefully attacked Raspberry Pi computers. This dropper is a script with an encrypted cryptocurrency miner embedded in its body. Once launched, the trojan unpacks and launches the miner, and then attempts to infect other devices available in the local area network. In order to prevent “competitors” from accessing the resources of an infected device, Linux.MulDrop.14 closes network port 22.
Linux.HideNSeek
The Linux.HideNSeek malware infects smart devices, computers, and servers running Linux, integrating them into a decentralized botnet. To spread itself, the trojan generates IP addresses and attempts to connect to them using a brute-force attack, as well as a list of known combinations of authentication data. It can also exploit various hardware vulnerabilities. Linux.HideNSeek can be used to remotely control the infected devices, i.e. execute commands from cybercriminals, copy files, etc.
Linux.BrickBot
Unlike most other malware, the Linux.BrickBot trojans are not intended to bring any profit. They are vandals, designed to disable computers and smart devices. They have been known since 2017.
Linux.BrickBot trojans are trying to infect devices via the Telnet protocol, brute-forcing the credentials. Then they try to erase the data from the permanent storage modules, reset the network settings, block all connections, and perform a reboot. As a result, to restore the objects, the user would need to reflash them or even replace the components. Those trojans are rare, but extremely dangerous.
In late June 2019, the Linux.BrickBot.37 trojan, also known as Silex, became popular. It acted in a similar way as other members of the Linux.BirckBot family, i.e. erasing data from device drives, deleting the network settings, and performing a reboot, after which they could no longer correctly switch on and operate. Our traps detected over 2,600 attacks using this trojan.
Conclusion
Millions of high-tech devices, increasingly used in everyday life, are actually small computers with the corresponding flaws. They are targeted by similar attacks and have the similar vulnerabilities, but due to the nature and limitations of their form, they are far more difficult or even impossible to protect. Additionally, many users are not fully aware of the potential risks and still perceive smart devices as safe and convenient toys.
The IoT market is actively developing and largely repeating the start of the mass distribution of personal computers, when the mechanisms against threats were only being developed. While manufacturers and owners of smart devices are adapting to new realities, cybercriminals have huge opportunities to attack them. Thus, we should expect new malware for the Internet of Things in the near future.
Doctor Web continues to monitor the spread of trojans and other threats aimed at smart devices and will inform our users about all noteworthy events in this area. Dr.Web anti-virus products successfully detect and remove the malware mentioned in this review.