Doctor Web: Android users threatened by fraudulent push notifications
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
June 14, 2019
The Web Push technology allows websites to send notifications even when the webpage is not open in the browser if the user agrees to that. When it comes to harmless websites, this feature can be useful and convenient. For example, social media can notify the users on new messages, and news agencies can spread information about new articles. However, cybercriminals and unscrupulous advertisers can abuse this technology by spreading advertising and fraudulent notifications that come from hacked or malicious websites.
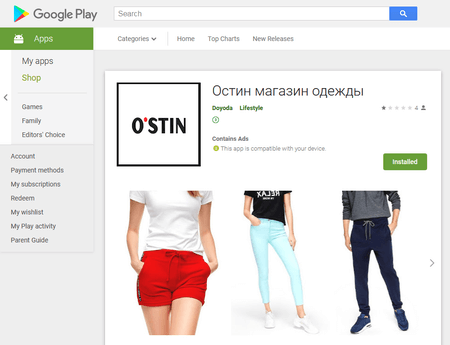
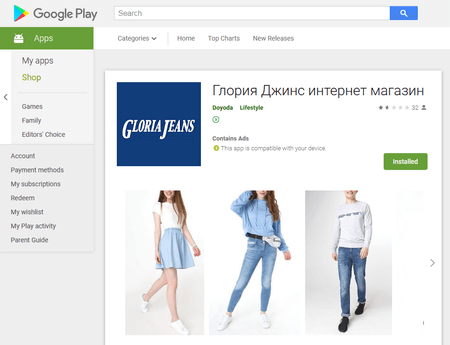
PC, laptop browsers, as well as mobile devices support these notifications. Typically, the victim gets to a questionable spamming website by clicking a unique link or an advertising banner. Android.FakeApp.174 is one of the first trojans that helps attackers increase the number of visitors of these websites and subscribe users of smartphones and tablets to such notifications.
Android.FakeApp.174 is distributed under the guise of useful programs; for example, official software of well-known brands. In early June, Doctor Web malware analysts detected two of the trojan modifications on Google Play. After contacting Google, the malware was removed, yet over 1,100 users have already downloaded malicious apps.
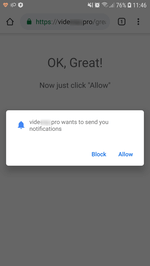
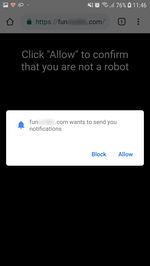
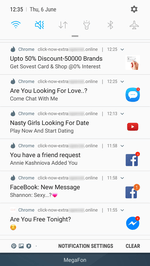
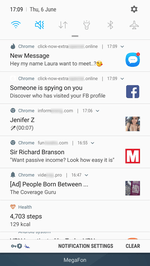
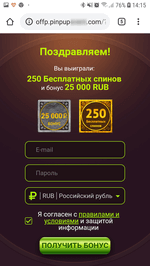
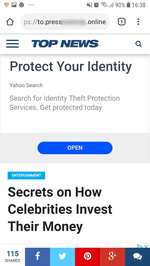
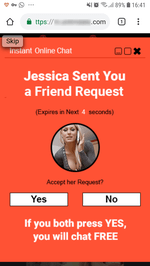
When launched, the trojan loads a website in Google Chrome. The website is specified in the trojan settings. According to its parameters, it performs several redirects to pages of various affiliated programs. Each of them prompts the user to allow notifications. To be convincing, they inform the victim that it is done for verification purposes (for example, that the user is not a robot), or simply hint on which dialog button to click. Thus, they increase the number of successful subscriptions. See examples of such queries in the images below:
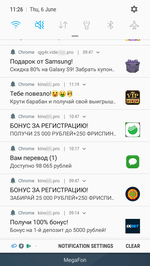
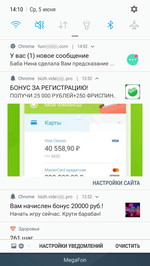
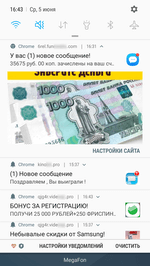
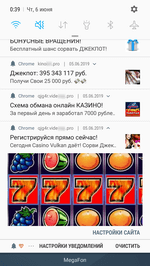
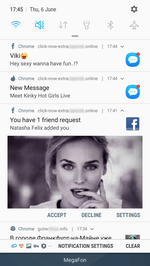
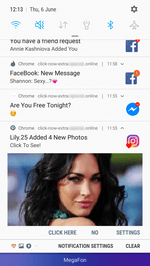
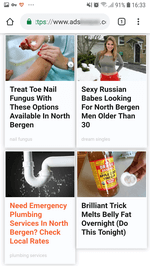
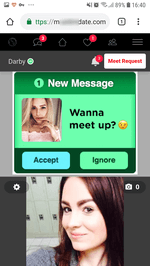
After activating the subscription, websites start sending the user numerous notifications of questionable content. Notifications are displayed in the status bar of the operating system even if the browser is closed and the trojan has already been removed. The contents can be anything, from false notifications about cash bonuses or transfers or new messages on social media to advertisements of horoscopes, casinos, goods and services, even various “news”.
Many of them look like real notifications of actual online services and applications installed on the device. For example, they display the logo of a bank, a dating website, a news agency, or a social network, as well as an eye-catching banner. Owners of Android devices can receive dozens of such spam messages per day.
Although these notifications also indicate the address of the website they come from, an unskilled user may fail to notice it, or not give it much thought. See below the examples of fraudulent notifications:
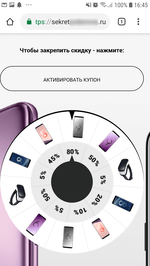
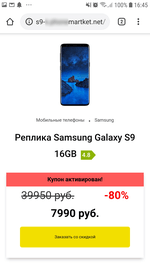
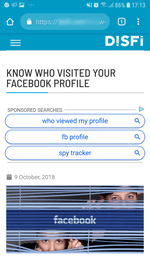
Having clicked a notification, the user is redirected to a website with questionable content. This may include advertising of casinos, betting shops, various Google Play applications, discounts and coupons, fake online polls and prize drawings, aggregators of partner links, and other online resources that vary depending on the country of residence of the user. See examples of such websites below:
Many of these resources are involved in well-known fraudulent schemes for stealing funds, but attackers can also launch an attack to steal confidential data at any time. For example, by sending an “important” notification via the browser on behalf of a bank or a social network. Potential victims can think the fake notification is real and tap it only to be redirected to a phishing site, where they will be prompted to indicate their name, credentials, email addresses, bank card numbers, and other confidential information.
Doctor Web experts believe that cybercriminals will make more active use of this method to promote questionable services, so mobile users should be careful while visiting websites and not subscribe to notifications if the website is unfamiliar or suspicious. If you are already subscribed to spam notifications, perform the following steps:
- Go to the Google Chrome settings, select “Site Settings” and then “Notifications”;
- On the list of websites with notifications, find the website address, tap it, and select “Clear & reset”.
Dr.Web for Android successfully detects and removes all known modifications of Android.FakeApp.174, so the trojan does not pose any threat to our users.
Read more about Android.FakeApp.174

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products