March 21, 2019
The most important changes affect the analyser's core components—the hypervisor, which facilitates file analysis under Windows, has been revamped. Now analysed samples will have an even harder time determining whether they are being run in a virtual environment. API 2.0 is another important innovation in Dr.Web vxCube 1.3. While the previous API version only offered access to basic features, the updated version offers an extensive set of options for interacting with the service. The resulting analysis reports are now more highly detailed, the analysis speed has increased, and identified defects have been corrected.
The new version of the service is already available to all the users who have a Dr.Web vxCube license. You can also evaluate the analyser on Doctor Web's site.
To purchase a license, please, contact our sales support.
Let's take a closer look at the key changes in the new version.
Enhanced protection from VM awareness
A variety of approaches can be taken to set up a virtual environment for analysing a suspect file. Hooking SSDT (System Service Descriptor Table) calls is the most common one. As a rule, this task is performed by a specific engine module. Despite the fact that this technique is regarded as obsolete, some researchers still use it. The main drawback here is the presence of a third-party driver that can be detected by the sample being examined. Furthermore, disabling the hooks will blind the analyser completely.
Since Dr.Web vxCube was originally designed using a different technique, the service is impervious to such issues. Because hardware virtualisation is utilised for hooking functions, the analyser has become even more unobtrusive and prevents suspicious samples from disrupting the analysis.
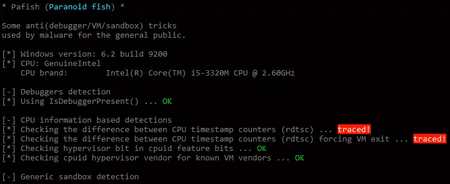
Doctor Web has equipped Dr.Web vxCube 1.3 with cutting-edge technologies to make the analyser even more inconspicuous for the sample being analysed. Now Dr.Web vxCube remains invisible to anti-sandbox and virtual machine tools such as Pafish. Pafish incorporates a number of techniques for detecting sandboxes and virtual machines—the same techniques that malware usually employs. For example, Pafish checks the following system parameters:
- Hard disk and RAM size;
- Screen resolution;
- Mouse cursor movements;
- TSC (timestamp counter) time difference;
- The presence of software, device IDs, and MAC addresses that indicate a virtual machine is being used.
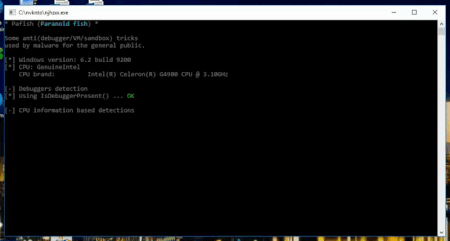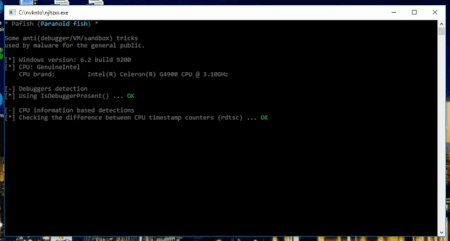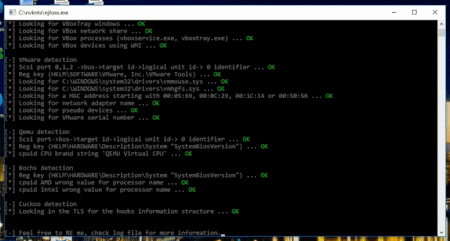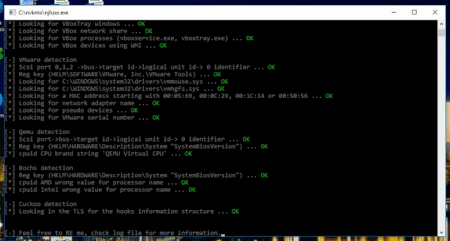
The screenshot demonstrates that Pafish has successfully detected an analysis environment by measuring a timestamp counter difference. Even though hardware virtualisation can be used to circumvent this limitation, configuring the software properly is not an easy task—the exact number of clock cycles for the vmexit and vmresume routines needs to be determined. The method adopted by our security software researchers enables Dr.Web vxCube 1.3 to remain undetected and bypass verification. Below you can see the results of using the latest Pafish version against Dr.Web vxCube 1.3.
However, there is more to Dr.Web vxCube 1.3 than just the ability to remain undetected by Pafish. Thanks to information contributed by Doctor Web’s malware researchers, the analyser also factors in many other VM detection techniques used by malware.
These techniques include:
- Checking CPU fan information;
- The presence of ACPI temperature readings;
- The availability of shortcuts, installed applications and Windows updates;
- The presence of a Xeon CPU.
Currently, Dr.Web vxCube 1.3 passes all existing anti-VM checks.
Dr.Web vxCube API 2.0
Users are now offered a wider range of options for interacting with the service. With the new API you can:
- Receive analysis results and a list of previous analysis sessions;
- Obtain a list of supported formats and platforms;
- Receive a list of all downloaded files;
- Request license information;
- Create additional HTTP API keys;
- Download an archive containing analysis results or retrieve a specific file from the archive;
- Use WebSocket to track the progress of an analysis.
In response to customer feedback, PCAP files can now be obtained without downloading an entire archive, and reports can now be deleted.
For the full list of API 2.0 features, please refer to the documentation.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments