Doctor Web: Android banker Flexnet uses computer games to steal money from users
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
March 21, 2019
Flexnet is based on the GM Bot Trojan, researched by Doctor Web malware analysts back in February 2015. The malicious app’s source code was published in 2016. Soon, the first versions of Flexnet were created thanks to everything achieved by GM Bot’s authors. Attacks against Android mobile devices using this Trojan continue happening to this day.
The cybercriminals distribute Flexnet Trojans via spam texting. In the messages, the potential victims are encouraged to follow the link and download some program or game. The Trojan disguises itself as applications such as Drug Vokrug (a dating and chatting app), GTA V, tools for Instagram and VKontakte account promotion, as well as other software.
Fig. 1. Example of software icons used by the Trojan.
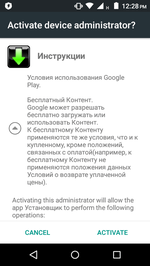
When launched, the Trojan requests admin privileges, displaying a standard dialog box. If the victim grants the permissions, the Trojan falsely reports an error and removes its icon from the home screen to hide from the user so as not to be removed.
Fig. 2-3. An attempt to request admin privileges and a false error message.
Compared with modern Android bankers, Flexnet’s capabilities are quite limited. The Trojan is capable of hooking and sending text messages, as well as performing USSD requests. However, these functions are enough to steal money using various fraudulent means.
One of them is topping up the in-game accounts of popular computer games via SMS. First, the Trojan checks a user's bank card balance by sending an SMS request to the mobile banking service system. Then it hooks the response message with the account balance and transmits this information to cybercriminals. Next, the attackers request to top up the gaming account, indicating the victim’s phone number and the amount to transfer. The user then receives a text message with a verification code. The Trojan intercepts this message, transfers its contents to the cybercriminals, and finally they give the Trojan a command to send the verification code to confirm the transaction.
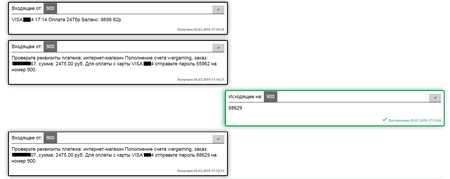
See below the example of money theft using this method:
Fig. 4. Top-up of Wargaming accounts. The Trojan hooks the messages from a bank’s billing system and, at the command of cybercriminals, sends a reply with a payment confirmation code to transfer RUB 2,475.
Other fraudulent schemes are implemented in a similar way. For example, the cybercriminals can pay for hosting using money from their victims’ mobile credit. To do this, the Trojan sends text messages with the necessary parameters to certain phone numbers. See below the example of such payment.
Fig. 5. Trojan texting the transfer amount (RUB 299 and RUB 1,000) and account names on the jino.ru hosting service to top up the balance of cybercriminals.
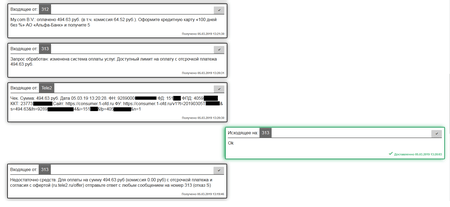
The attackers can steal money even if the victim does not have enough on the balance. They use the credit options provided by mobile carriers. As in other cases, the cybercriminals instruct the Trojan to send a text with the necessary parameters. Owners of the infected devices are oblivious to the money loss because the banker hides all suspicious messages.
Fig. 6. The fraudsters attempt to pay for the My.com service, but the amount on the victim’s mobile credit is not enough to do it. They command the Trojan to use the credit option and successfully perform the transfer. Thus, the device owner is left with a phone debt.
Additionally, the Trojan can transfer money from victims’ bank cards to cybercriminals’ accounts. However, financial institutions use specific algorithms to track suspicious transactions, so the probability of them being blocked is very high, while the above schemes allow the fraudsters to steal relatively small amounts for a long time and go unnoticed.
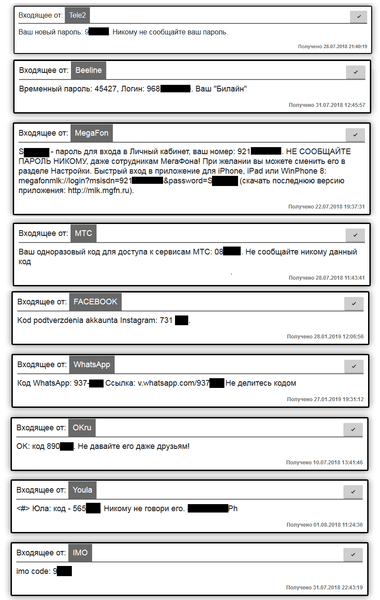
Another feature of Flexnet involves stealing confidential data. The cybercriminals can get ahold of accounts on social media, online stores, the websites of mobile carriers, and other online services. Knowing the victim’s mobile phone number, the cybercriminals try to log into their account. The service sends a text with a one-time verification code, which the Trojan hooks and sends to the attackers.
Fig. 7. Texts with one-time access codes of various services, hooked by the Trojan.
If the number used on the infected device is not registered with the target services, the cybercriminals can use it to register a new account. In the future, those compromised and newly created accounts can enter the black market and then be used to send spam and arrange phishing attacks.
With the assistance of the REG.ru registrar, several Flexnet command and control servers were blocked, and the cybercriminals no longer control some of the infected devices.
Doctor Web reminds owners of Android smartphones and tablets that software and games should only be installed from reliable sources such as Google Play. You are strongly advised to pay attention to the reviews of other users and use software from trusted developers.
Dr. Web for Android detects all known modifications of the Flexnet Trojan as parts of the Android.ZBot family and successfully removes them from infected devices. This malware poses no threat to our users.
#Android, #banking_Trojan, #two_factor_authentication
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 140 million downloads on Google Play alone
- Free for users of Dr.Web home products