Politics and fraud: virus events of September 2010
Virus reviews | All the news | Virus alerts
Trojan.Stuxnet and politics
In September, news headlines screamed about Trojan.Stuxnet whose appearance attracted tremendous publicity due to the geographical extent of its impact. Many news posts related to the Trojan dealt mainly with politics and proposed that the makers of Trojan.Stuxnet aimed to disrupt the launch of a nuclear power plant in Iran. In the last days of September, media reports claimed that the Trojan had spread widely in China and was targeting Chinese companies. Amid such speculations little attention was paid to ethnological innovations employed by the virus makers. Yet some experts resorted to a linguistic analysis of the comments found in the Trojan’s code to discern what the goals of its makers really were
Trojan.Stuxnet is indeed a technologically advanced piece of malware that exploits several previously unknown Windows vulnerabilities. Politics aside, Doctor Web’s analysts consider the Trojan to be merely another piece of malware from which Dr.Web users must be protected. Currently there are a number of no less technologically advanced viruses in the wild, for example, the 64-bit version of Trojan.Tdss (a.k.a. TDL) for which curing routines are also diligently being developed.
Internet fraud
In September Doctor Web’s support service registered 124 requests concerning the inability to access Windows UI, web sites, or popular software. This was up from 107 such requests in the previous month of August.
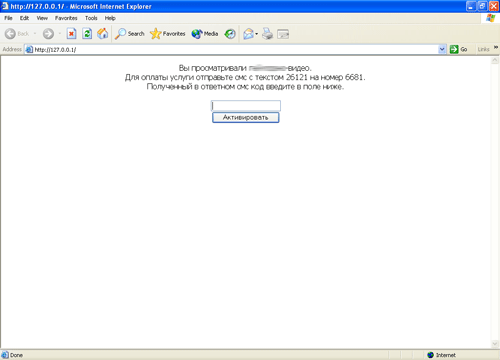
At the same time, Windows blockers were being superseded by other fraudware. In particular, several Trojans discovered in September used new redirection techniques for browsers. Some Trojans made it impossible to use instant messaging applications.
As for converting their illegal income into actual money, in September cyber fraudsters preferred to receive money via cell phone account refills (around 25%) and paid short messages (around 70%).
As before Doctor Web offers free technical support to users who have fallen victim to cyber fraud.
Redirection
In the last month criminals adopted two new techniques for directing users to fake web pages. As always the techniques involved modifying the hosts file, but new technologies were also applied.
Trojan.Hosts.1581 made the browser display fake pages of a Russian bank’s web site, allowing criminals to receive remote account access parameters submitted by duped victims. It has also been discovered that this modification of Trojan.Hosts features a rootkit component that allows it to filter file operations and operations performed with the Windows Registry.
Trojan.HttpBlock programs used another tactic: they launched their own web server in an infected system and used it to display pages that mimicked popular web sites–particularly search engine pages. Here criminals demanded a ransom from users in exchange for allowing them to regain access to the sites.
IM blocker
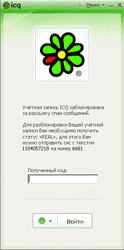
Trojan.IMLock, which blocks the launch of popular instant messaging clients such as ICQ and Skype, was discovered at the end of September. Instead of launching a program, the Trojan displayed a message, mimicking the design of the blocked messenger and informing the user that he had to send a paid short message in order to regain access to his IM account. To neutralize the Trojan, simply check your system with the Dr.Web scanner.
Malicious web site for Android only
A new malicious program for Android (Android.SmsSend.2) was discovered in September. Its functionality differed little from that of its predecessors (e.g. it sent paid short messages from infected mobile devices), with the exception of one significant difference: The downloading of the Trojan was initiated only if a potential victim loaded a bogus web page onto a device that was running Android. Perhaps, criminals believed that such a selective approach would make it more difficult to discover the malicious site.
New botnet trends
At the end of September, Doctor Web’s analysts discovered a botnet comprised of computers on which the server side of Radmin software was installed and running. This software is the most widely used for remote administration. The malicious program that infects computers and connects them to the botnet was classified by Dr.Web as Win32.HLLW.RAhack.
However, a system would only get infected if an administrator password used to access Radmin was found on the worm’s list. It turned out that many administrators were using weak passwords.
As for trends that could develop in October 2010, they will most likely be related to fraudware and new malicious programs that substitute fake web pages for real ones when certain sites are accessed. This is because criminals have found such programs to be the most profitable. Owners of botnets, which are often used to spread malware, will keep trying to create such networks using non-standard software and hardware solutions since such approaches ensure that infection remains undetected.
Viruses detected in e-mail traffic in September
| 01.09.2010 00:00 - 01.10.2010 00:00 | ||
|
1
|
337845 (11.46%)
| |
|
2
|
308357 (10.46%)
| |
|
3
|
252490 (8.57%)
| |
|
4
|
246976 (8.38%)
| |
|
5
|
230637 (7.82%)
| |
|
6
|
118139 (4.01%)
| |
|
7
|
102740 (3.49%)
| |
|
8
|
90503 (3.07%)
| |
|
9
|
65819 (2.23%)
| |
|
10
|
57658 (1.96%)
| |
|
11
|
52397 (1.78%)
| |
|
12
|
49619 (1.68%)
| |
|
13
|
49478 (1.68%)
| |
|
14
|
43600 (1.48%)
| |
|
15
|
32908 (1.12%)
| |
|
16
|
26135 (0.89%)
| |
|
17
|
24706 (0.84%)
| |
|
18
|
24681 (0.84%)
| |
|
19
|
22101 (0.75%)
| |
|
20
|
19668 (0.67%) | |
| Total scanned: | 22,631,101,955 |
| Infected: | 2,947,658 (0.01%) |
Viruses detected on user machines in September
| 01.09.2010 00:00 - 01.10.2010 00:00 | ||
|
1
|
8273098 (23.82%)
| |
|
2
|
5135896 (14.79%)
| |
|
3
|
3690668 (10.63%)
| |
|
4
|
1977696 (5.70%)
| |
|
5
|
1927627 (5.55%)
| |
|
6
|
1370895 (3.95%)
| |
|
7
|
1300940 (3.75%)
| |
|
8
|
1091703 (3.14%)
| |
|
9
|
1042949 (3.00%)
| |
|
10
|
823512 (2.37%)
| |
|
11
|
795502 (2.29%)
| |
|
12
|
620668 (1.79%)
| |
|
13
|
561893 (1.62%)
| |
|
14
|
298586 (0.86%)
| |
|
15
|
248724 (0.72%)
| |
|
16
|
228104 (0.66%)
| |
|
17
|
213306 (0.61%)
| |
|
18
|
151676 (0.44%)
| |
|
19
|
145085 (0.42%)
| |
|
20
|
136102 (0.39%) | |
| Total scanned: | 12,949,782,895,195,462 |
| Infected: | 34,724,949 (0.00%) |