December 28, 2018
In the past year, Android mobile device owners were again targeted by many malicious and unwanted programs, many of which were distributed via Google Play. At the same time, the tendency noted in 2017 to use various means for disguising and hiding Trojans to make them harder to detect has noticeably increased.
One of the main threats to mobile device users over the past 12 months were Android bankers, attacking financial institution customers around the world. Malware that could download and run arbitrary code from the Internet posed a serious threat as well.
Virus writers were actively distributing Trojans to implement fraudulent schemes, as well as using other malicious apps to obtain illegal income. In addition, cybercriminals tried to launch mobile cryptocurrency mining and even used Trojan clippers to change the numbers of electronic wallets in the clipboard of Android devices.
The mobile firmware infection issue at the production stage remains relevant. In spring, Doctor Web virus analysts uncovered a Trojan embedded in the image of the Android operating system. More than 40 mobile device models were compromised.
Users were also threatened with malicious spyware throughout the year.
Principal trends of the year
- New detections of malicious and unwanted programs on Google Play
- Attempts of virus writers to hinder the detection of malware
- Banking Trojans attacking customers of financial institutions worldwide
- Trojans using Android Accessibility Service to automate malicious activities
- Spread of Trojan clippers capable of changing e-wallet numbers in clipboard
Most remarkable events
At the beginning of the year, information security specialists detected the spread of the Android.CoinMine.15 Trojan miner infecting smart TVs, routers, streaming boxes, and other Android devices. It infected the equipment using the Android Device Bridge debugger. To do this, Android.CoinMine.15 generated random IP addresses and tried to connect to open port 5555. If the connection was successful, the Trojan installed its copy on the accessible device along with auxiliary files, including mining software for Monero (XMR).
In March, Doctor Web reported a new case of detecting the Android.Triada.231 Trojan in the firmware of more than 40 Android smartphone and tablet models. Unidentified attackers have embedded Android.Triada.231 in one of the system libraries at the source code level, while other representatives of the Android.Triada family are usually distributed as separate applications. The Trojan embeds itself in the Zygote system process that launches programs. As a result, Android.Triada.231 infects other processes and can covertly perform malicious actions. For example, it can download, install, and remove software against the user’s will. More details on this case, investigated by Doctor Web experts, are available in this article.
Attackers are increasingly using a variety of methods to prevent the detection of malicious and unwanted programs. In 2018, this trend continued. A popular way to reduce malware visibility is to use loaders. They can help keep Trojans and other dangerous software out of antivirus software’s reach for a longer time and cause less suspicion among potential victims. Using such loaders, cybercriminals can distribute various malware such as Trojan spyware.
In April, the Android.DownLoader.3557 loader was found on Google Play. It downloaded onto devices and prompted users to install the malicious software Android.Spy.443.origin and Android.Spy.444.origin under the guise of important plugins. They tracked the location of an infected smartphone or tablet, received information about all available files, could send victim’s documents to attackers, send and intercept SMS messages, steal data from the contact list, record video, listen to the environment using the built-in microphone of the device, as well as intercept phone calls and perform other actions.
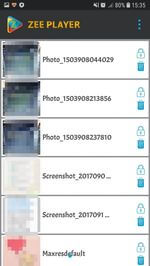
In August, we detected the Android.DownLoader.784.origin loader on Google Play. It downloaded Trojan spyware onto the device which was dubbed Android.Spy.409.origin. Virus writers distributed Android.DownLoader.784.origin under the guise of the Zee Player application, which allowed users to hide photos and videos stored in the memory of mobile devices. The program was fully operational, so the attackers’ victims had no reason to suspect anything bad.
However, Trojan downloaders are increasingly used to distribute Android bankers. In July, Android.DownLoader.753.origin was found on Google Play where it was disguised as financial applications. Some of them were actually functional to appear more trustworthy. Android.DownLoader.753.origin downloaded and tried to install various banking Trojans that stole confidential data.
Later, several similar malicious programs were detected on Google Play. One of them was given the name Android.DownLoader.768.origin. Cybercriminals distributed it under the guise of the official Shell software. Another addition to the Dr.Web virus database was Android.DownLoader.772.origin, which was disguised as a useful utility. Both Trojans were also used to download and install Android bankers.
Loaders are used to infect mobile devices with other malware. In October, virus analysts detected the Trojan Android.DownLoader.818.origin, distributed under the guise of a VPN client via Google Play. Later, Doctor Web experts uncovered several modifications hidden in fake games. They were named Android.DownLoader.819.origin and Android.DownLoader.828.origin. They were intended to install adware Trojans.
Multi-component malicious applications are becoming increasingly common. Each of the modules performs certain functions, which allows attackers, if necessary, to expand the Trojans’ capabilities. This operation principle helps hinder threat detection. Virus writers can quickly update these plugins and add new ones, leaving the Trojan body with a minimum set of functions and making it less noticeable.
Doctor Web experts discovered this combination in February and dubbed it Android.RemoteCode.127.origin. The Trojan, installed by over 4,500,000 users, covertly downloaded and launched malicious modules that performed various activities. One of the Android.RemoteCode.127.origin plugins updated itself with a patch, hidden in a seemingly normal image. This method of hiding malicious objects is known as steganography. Information security specialists have been aware of it for a long time, but it has rarely been used by virus writers.
After decryption and launch, the module downloaded another image with another hidden plugin, which loaded and launched the Android.Click.221.origin. It then opened websites in the background and clicked on elements, i.e. links and banners, to increase hit counters and earn money for clicks.
Examples of images with encrypted modules of Android.RemoteCode.127.origin:
For more information regarding this Trojan, refer to the news article on our website.
Android.RemoteCode.152.origin is another multi-component Trojan capable of loading and executing arbitrary code. It was installed by more than 6,500,000 users. This malicious program covertly downloaded and launched auxiliary modules, including advertising plugins. The Trojan used them to create invisible ad banners and clicked on them, earning profits for virus writers.
In August, Doctor Web analysts investigated the Trojan clipper Android.Clipper.1.origin and its modification Android.Clipper.2.origin. This malicious program substituted the e-wallet numbers of Yandex.Money, Qiwi and Webmoney (R and Z), as well as Bitcoin, Litecoin, Etherium, Monero, zCash, DOGE, DASH, and Blackcoin cryptocurrency in the clipboard. Virus writers distributed the Trojan under the guise of well-known and harmless applications.
When copying the e-wallet number to clipboard, Android.Clipper.1.origin hooked it and transferred it to the command and control server. In response, the malware received the number of the attackers’ e-wallet, and the Trojan set it to replace the one in the clipboard. As a result, if the user did not notice the substitution, they would transfer money to the cybercriminals’ account. See detailed information about Android.Clipper.1.origin in the news article on the Doctor Web website.
Mobile malware landscape
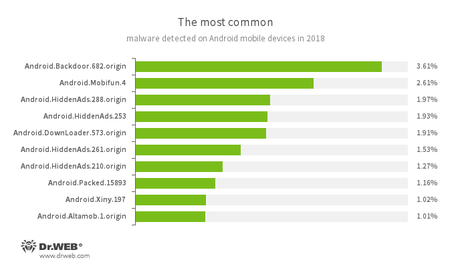
According to Dr.Web’s detection statistics for Android products in 2018, Android devices were most often targeted by adware Trojans, malware that downloaded malicious and unwanted software, as well as Trojans that executed cybercriminal commands.
- Android.Backdoor.682.origin
- Trojan that executes cybercriminal commands to launch malicious activities.
- Android.Mobifun.4
- Representatives of a Trojan family designed to display unwanted ads.
- Android.HiddenAds
- Representatives of a Trojan family designed to display unwanted ads.
- Android.DownLoader.573.origin
- Malware that downloads applications indicated by virus writers.
- Android.Packed.15893
- Detects Trojans protected by a program packer.
- Android.Xiny.197
- Trojan primarily intended for downloading and removing applications.
- Android.Altamob.1.origin
- Malware that downloads applications indicated by virus writers.
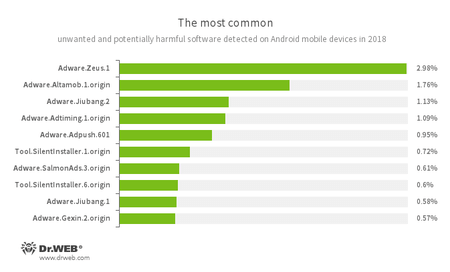
Among the unwanted and potentially dangerous applications found on Android devices during the year, ad-displaying modules were the most common. Applications for downloading and installing various software were also detected on smartphones and tablets.
- Adware.Zeus.1
- Adware.Altamob.1.origin
- Adware.Jiubang
- Adware.Adtiming.1.origin
- Adware.Adpush.601
- Adware.SalmonAds.3.origin
- Adware.Gexin.2.origin
They were unwanted modules that software developers and virus writers had injected into applications to display aggressive advertising.
- Tool.SilentInstaller.1.origin
- Tool.SilentInstaller.6.origin
Potentially dangerous programs designed to download and install other applications.
Banking Trojans
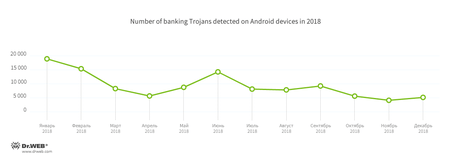
Banking Trojans are still a serious threat to mobile device owners. These malicious applications steal credentials to access the accounts of customers of financial institutions, bank card details, and other confidential data that can be used to steal money. Over the past 12 months, Dr.Web for Android detected over 110,000 of these Trojans on smartphones and tablets. The dynamics for Android banker detection is shown in the following graph:
When authors of the banking Trojan Android.BankBot.149.origin published its source code at the end of 2016, Doctor Web experts predicted the emergence of a variety of similar malware. This assumption turned out to be true: virus writers actively started producing similar bankers, also improving them and adding new functions. One of these Trojans, distributed in 2018, was Android.BankBot.250.origin, as well as its new and even more dangerous version Android.BankBot.325.origin. This banker, known as Anubis, is a multifunctional malicious application. It not only steals confidential data and money of users, but also is capable of executing numerous commands. It can help cybercriminals access infected devices using Android.BankBot.325.origin as a remote administration utility. The detailed study of this Trojan can be found in the article on our website.
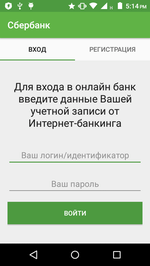
In March, Doctor Web experts detected the Android.BankBot.344.origin Trojan hiding in an application named “VSEBANKI – Vse banki v odnom meste” (ALLBANKS – all banks in one place) on Google Play. The attackers claimed it was a universal application for online banking systems of several Russian financial institutions.
When launched, Android.BankBot.344.origin prompted the potential victim to enter an already existing bank account, specifying the credentials, or register by providing bank card details. The information was then transferred to the attackers so they could steal money from the compromised account.
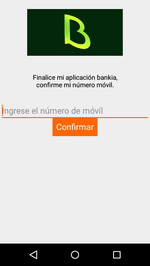
In autumn, virus analysts investigated the banker Android.Banker.2876, which was also distributed on Google Play and attacked the customers of financial institutions in Spain, France, and Germany. It displayed a phishing window and prompted the potential victim to enter their phone number, which was then transferred to virus writers. After that, Android.Banker.2876 started to hook SMS messages and send the contents to attackers. Thus, they could receive transaction confirmation codes and steal users' money.
Later, our experts uncovered Android.BankBot.495.origin intended for Brazilian users on Google Play. Android.BankBot.495.origin took advantage of the accessibility features on Android to read the contents of windows on running applications, transfer confidential data to attackers, and also independently press buttons and control the compromised programs. The Trojan could also display fraudulent windows that prompted users to enter their credentials, credit card details, and other confidential information.
Fraud
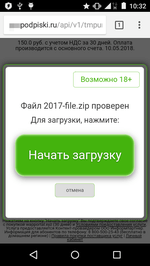
Cybercriminals are increasingly using malware for mobile Android devices for fraudulent campaigns. In 2018, we detected many of these Trojans. One of them is Android.Click.245.origin, which was described by Doctor Web in April. It was distributed under the guise of well-known applications, but only loaded fraudulent web pages, inviting potential victims to download various software after entering their mobile phone number. After entering the number, the victim received an SMS message with a confirmation code, which was supposedly needed to complete the application download. However, by entering the code on the website, the user subscribed to a chargeable service. If the owner of the infected device was using mobile Internet, they were subscribed to an expensive service with Wap-Click immediately after clicking on the fake download button. See below an example:
Over the year, our specialists found other Trojans on Google Play that could load any webpage on the command of the command and control server. The list included Android.Click.415, Android.Click.416, Android.Click.417, Android.Click.246.origin, Android.Click.248.origin, Android.Click.458 and several others. They were also distributed under the guise of useful programs, such as collections of recipes, manuals, voice assistants, games, and even bookmaker applications.
Cybercriminals also actively distributed the Android.FakeApp family of Android Trojans, which loaded fraudulent websites with fake polls. Users were asked to answer a few simple questions for a nice cash reward. To receive the payment, the victim had to make another payment for verification. However, the owner of the infected device never received any money after the transfer.
Over the year, malware analysts discovered dozens of fraudulent applications Android.FakeApp and Android.Click, installed by at least 85,000 owners of Android smartphones and tablets. See more details about some of these Trojans in the following article by Doctor Web.
Prospects and trends
Next year mobile device users will again face attacks from banking Trojans and virus writers will continue improving their functionality. It is likely that more Android bankers will turn into multi-function malware capable of performing a wide range of tasks.
The number of fraudulent applications and advertising Trojans will increase also. Virus writers will hardly abandon attempts to make money on cryptocurrency using the computing power of Android devices. We also cannot eliminate the possibility of further cases of firmware infection in the future.
Cybercriminals will improve methods for circumventing antiviruses, as well as new restrictions and protective features built in the Android operating system. Rootkits and Trojans that could bypass these barriers are not out of the question. Malicious programs with new operating principles and new ways to obtain confidential data could emerge on the market. For example, they might use mobile device and eye-tracking techniques to obtain information about text being typed. Furthermore, new malware might use machine learning algorithms and other means of artificial intelligence for the benefit of attackers.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 140 million downloads on Google Play alone
- Free for users of Dr.Web home products