November 30, 2018
The last month of autumn 2018 witnessed the occurrence of several interesting information security events. In November, Doctor Web’s experts detected a mining Trojan for Linux that can remove antivirus programs from infected devices. Soon thereafter, they discovered a clicker Trojan for Windows that has an exceptionally curious way of infecting the computers of potential victims. Virus writers’ interest in the Android platform does not seem to be decreasing either: new Android-targeting malicious programs were detected and added to the Dr.Web virus databases in November.
PRINCIPAL TRENDS IN NOVEMBER
- The distribution of a clicker Trojan for Windows
- A Linux miner capable of removing antiviruses
- Detection of new malicious programs for Android
Threat of the month
The Trojan, added to the Dr.Web virus database as Trojan.Click3.27430, is a malicious program designed to covertly increase website traffic. It is distributed under the guise of a DynDNS application that can bind a subdomain to a computer with no static IP address. The attackers created a special website to help spread the Trojan.
The archive containing the executable file setup.exe, which is actually a downloader, is downloaded from this website. In turn, the archive downloads another file disguised as an ARJ archive online. This file is in fact a dropper that installs the Trojan and the actual DynDNS application in the system. If the user later decides to uninstall it from their infected computer, only DynDNS will be removed, and Trojan.Click3.27430 will remain in the system and continue its malicious activity. More detailed information about this Trojan and how it works can be found in an article published on our website.
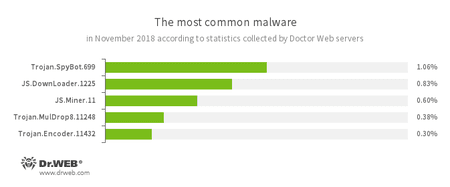
According to Doctor Web’s statistics servers
- Trojan.SpyBot.699
- A multi-module banking Trojan. It allows cybercriminals to download and launch various applications on an infected device and makes it possible for their commands to be executed. The Trojan is intended to be used to steal money from bank accounts.
- JS.DownLoader
- A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer.
- JS.Miner
- A family of JavaScript scenarios designed to covertly mine cryptocurrencies (mining).
- Trojan.MulDrop
- А Trojan that can install other malicious programs on a computer.
- Trojan.Encoder.11432
- An encryption worm, also known as WannaCry.
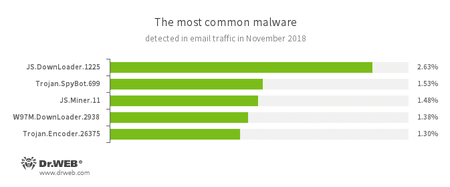
Statistics for malware discovered in email traffic
- JS.DownLoader
- A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer.
- Trojan.SpyBot.699
- A multi-module banking Trojan. It allows cybercriminals to download and launch various applications on an infected device and makes it possible for their commands to be executed. The Trojan is intended to be used to steal money from bank accounts.
- JS.Miner
- A family of JavaScript scenarios designed to covertly mine cryptocurrencies (mining).
- Trojan.Encoder.26375
- An encryption ransomware Trojan that encrypts files and demands a ransom to decrypt the compromised data.
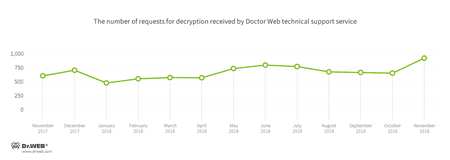
Encryption ransomware
In November, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.858—32.15% of requests;
- Trojan.Encoder.11464—11.17% of requests;
- Trojan.Encoder.11539—10.80% of requests;
- Trojan.Encoder.25574—4.91% of requests;
- Trojan.Encoder.567—1.35% of requests;
- Trojan.Encoder.10700—1.35% of requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
Phishing websites form a separate category of dangerous and non-recommended websites. Phishing is a type of online fraud whose ultimate goal is to steal a victim’s confidential information, e.g., logins and passwords for Internet services and social media credentials. To do this, attackers create fake websites that mimic the design of different online platforms, and use all sorts of methods to lure users there. Cybercriminals can use the information they obtain to send ads for the purposes of fraud or blackmail.
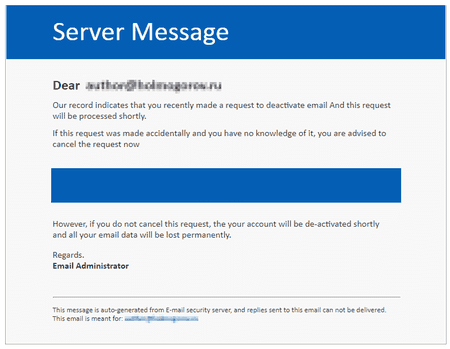
In November, Doctor Web’s experts detected several cases of similar fraudulent mailings. Cybercriminals sent users emails that appeared to have come from the administrators of the mail services they were using. The emails alleged that the users had sent a request to deactivate their mailboxes, and in order to cancel this request, they needed to follow the link included in the email.
The link led to a phishing website with a form in which the users were to enter the login and password used to access their mailboxes. Any visitor-entered data would lead to an error message; meanwhile, the information was immediately transmitted to the attackers. Doctor Web’s specialists identified several such websites, and their URLs were added to SpIDer Gate’s databases.
In November 2018, 231,074 URLs of non-recommended websites were added to the Dr.Web database.
| October 2018 | November 2018 | Dynamics |
|---|---|---|
| + 156,188 | + 231,074 | + 47.94% |
Linux malware
Linux.BtcMine.174 is certainly not the first Linux Trojan known by Doctor Web’s analysts to use an infected computer to mine cryptocurrency. What is interesting about this malware is its ability to search and delete antiviruses installed on an infected device.
The Trojan is a shell script with more than 1,000 lines of code. It consists of several components that are downloaded from the attackers’ server. Upon successful installation, the script downloads a version of the Trojan Linux.BackDoor.Gates.9, which is designed to perform DDoS attacks and can execute attacker-issued commands.
Once installed in a system, Linux.BtcMine.174 searches for other miners and, when it detects them, terminates their processes. If Linux.BtcMine.174 was launched with no root access, it uses a set of exploits to escalate its privileges. It then attempts to detect running antivirus programs and terminate them, and then, using package managers, deletes their files and the whole directory in which they were installed. Moreover, the Trojan downloads and launches a rootkit on the infected device, collects information about the other devices previously connected to it via SSH, and tries to infect them too. More detailed information about this malware can be found in the review article published on our website.
Other events in information security
Statistics collected by Doctor Web’s servers on infected computers and in mail traffic suggest that Trojan.SpyBot.699 was one of the malware products being spread most widely in November. It is distributed by the RTM hacker group and is a multi-module banking Trojan.
The malicious functions of Trojan.SpyBot.699 are mainly in the core.dll dynamic library, which is uploaded into the device memory. The Trojan adds itself to the Windows autorun list and encrypts all the data transmitted to a command and control server.
Upon the attackers’ command, Trojan.SpyBot.699 can download, save to a disk, and run executable files; download and run programs without saving them; upload dynamic libraries into the memory; run updates; install digital certificates in the system storage; and execute other external commands.
This malware can search for bank clients among running processes, in the names of open windows, and in files stored on disks. The Trojan also looks for bank-client system information in browser cookies. Once they obtain the information, the attackers can use Trojan.SpyBot.699 and its downloadable modules to perform a detailed scan of the infected system, ensure that it’s permanently infected by other Trojans, and imbed malware in the accounting and bank-client software. The cybercriminals’ ultimate goal is to steal money from their victims’ bank accounts. Dr.Web antivirus products successfully detect and remove Trojan.SpyBot.699 and all the malicious modules attackers are currently known to use with this Trojan.
Malicious and unwanted programs for mobile devices
This November, Doctor Web’s virus analysts found the Trojan Android.Banker.2876 being distributed via Google Play. Attackers were using it to steal confidential customer data from several European banks. Other threats were found on Google Play, including the downloader Android.DownLoader.832.origin, which downloaded and tried to install other malware. Our experts also discovered Trojans from the Android.FakeApp family, which are used by cybercriminals to earn money illegally. In addition, they identified applications with Adware.HiddenAds advertising modules imbedded into them.
The following November events related to mobile malware are the most noteworthy:
- the distribution of malicious and unwanted applications on Google Play.
Find out more about malicious and unwanted programs for mobile devices in our special overview.