Doctor Web registers over 51,000 installations of Downloader Trojan from Google Play
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
October 22, 2018
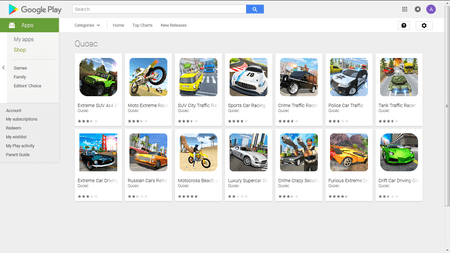
Android.DownLoader.819.origin is a downloader that installs other malicious applications to Android devices and launches them. The Trojan was distributed by the Quoac developer under the guise of games. Doctor Web experts have found 14 copies of Android.DownLoader.819.origininstalled by at least 51,100 Android mobile device users. Our malware analysts have sent the data on the identified software to Google. At the time we published this article, it was removed from Google Play.
Information about the detected malicious applications is in the table below:
| App name | Software package name | Version |
|---|---|---|
| Extreme SUV 4x4 Driving Simulator | com.quoac.extreme.suv.driving | 0.3 |
| Moto Extreme Racer 3D | com.quoac.moto.extreme.racing | 0.3 |
| SUV City Traffic Racer | com.suv.traffic.racer | 0.3 |
| Sports Car Racing | com.quoac.sports.car.racing | 0.3 |
| Crime Traffic Racer | com.quoac.crime.traffic.game | 0.3 |
| Police Car Traffic | com.quoac.police.car.traffic | 0.3 |
| Tank Traffic Racer | com.quoac.tank.traffic.racer | 0.3 |
| Extreme Car Driving Simulator | com.quoac.extreme.car.driving.simulator | 0.3 |
| Russian Cars Retro | com.quoac.russian.car.retro | 0.3 |
| Motocross Beach Jumping - Bike Stund Racing | com.quoac.motocross.beach.jumping | 0.4 |
| Luxury Supercar Simulator | com.quoac.luxury.supercar.simulator | 0.3 |
| Crime Crazy Security | com.quoac.crime.crazy.security | 0.4 |
| Furious Extreme Drift | com.quoac.furious.extreme.drift | 0.3 |
| Drift Car Driving Simulator | com.quoac.car.driving.simulator | 0.5 |
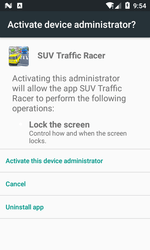
Android.DownLoader.819.origin is a modification of the Trojan Android.DownLoader.818.origin and has the same features. When launched, it requests read and write access to the SD card, and then prompts the user to assign it as one of the mobile device administrators. If the access is granted, the Trojan removes its own icon from the main screen menu of the operating system and hides itself on the device. After that, launching the “game” is impossible and the malicious application can only be found in the list of installed programs in the system settings.
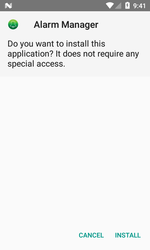
When granted the necessary privileges, the Trojan connects to the remote server and downloads an APK file in the background. It then offers the device user to install it. If the user refuses, the malware tries to perform the installation again, showing the same dialog every 20 seconds until the user agrees to install the application. The file the Trojan downloads and installs is the malware. Android.HiddenAds.728, which displays ads whenever the screen of the affected smartphone or a tablet is on.
All known modifications of the Downloader Trojan Android.DownLoader.819.origin, as well as the malware they download, are successfully detected and removed by Dr.Web products for Android and, therefore, pose no threat to our users.
Your Android needs protection!
Use Dr.Web
- First Russian anti-virus for Android
- Over 135 million downloads—just from Google Play!
- Available free of charge for users who purchase Dr.Web home products