Doctor Web’s September 2018 virus activity review
Doctor Web’s September 2018 virus activity review
[% DEFAULT FILE_REVIEW = ''; NAME_SOME_ARRAY_IN_MACROSNAME = [ { box => "Overview" }, { box => "Threat of the month" }, { box => "Statistics" }, { box => "Encryption ransomware" }, { box => "Dangerous websites" }, { box => "Mobile devices" } ] %] [% BLOCK global.tpl_blueprint.content %]September 28, 2018
September 2018 is marked by the spread of a banking Trojan posing a threat to clients of Brazilian financial institutions. Doctor Web specialists detected over 300 unique samples of this malicious software and over 120 online media sites from which the banking Trojan downloaded its components. Over the past month, virus analysts also detected new dangerous Android applications.
Principal trends in September
- The distribution of a new banking Trojan
- Detection of new malicious programs for Android
Threat of the month
Banking Trojans designed to steal money from financial institutions’ clients are highly spread all over the world. In September, Doctor Web security researchers examined a new Trojan of this kind. It was named Trojan.PWS.Banker1.28321. This banking Trojan targeted Brazilian people. So far, 340 unique Trojan.PWS.Banker1.28321 samples and 129 domains and IP addresses have been detected. These domains and IP addresses belong to cybercriminals, and the Trojan used them to download archives with malicious library.
The Trojan is distributed under the guise of an application designed to view Adobe Reader PDF documents. It infects computers running Microsoft Windows if Portuguese is specified in the language settings as the primary language. All Trojan.PWS.Banker1.28321 malicious functions are located in an encrypted and packed dynamic library that is downloaded by the banking Trojan from cybercriminals’ websites.
When users open the Internet banking websites from various Brazilian financial institutions in the browser window, the Trojan imperceptibly replaces the web page, showing the victim a fake authentication form. In some cases, the Trojan requests an authorization verification code from an SMS message the banks sends users. This information is then transmitted to cybercriminals. For more information regarding this incident, refer to this news article.
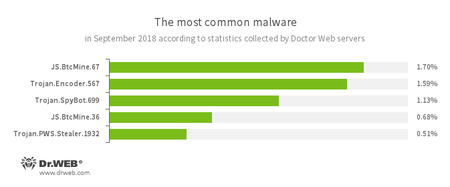
According to Doctor Web’s statistics servers
- JS.BtcMine.7
- A family of JavaScript scenarios designed to secretly mine cryptocurrencies (mining).
- Trojan.Encoder.567
- A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom to decrypt compromised data.
- Trojan.SpyBot.699
- Spyware designed for keyboard clickjacking on an infected device, executing commands and stealing confidential information.
- Trojan.PWS.Stealer.1932
- A Trojan for Windows that steals confidential information, including user passwords.
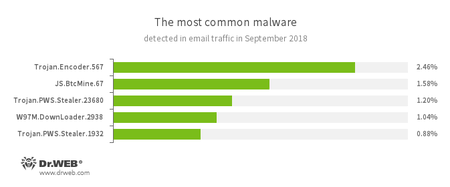
Statistics concerning malicious programs discovered in email traffic
- Trojan.Encoder.567
- A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decrypting compromised data.
- JS.BtcMine.7
- A family of JavaScript scenarios designed to stealthily mine cryptocurrencies (mining).
- Trojan.PWS.Stealer
- A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
- W97M.DownLoader
- A family of downloader Trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised computer.
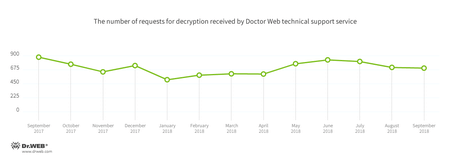
Encryption ransomware
In September, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.567—16.94% of requests;
- Trojan.Encoder.858—12.71% requests;
- Trojan.Encoder.11464—10.68% requests;
- Trojan.Encoder.25574—4.79% requests;
- Trojan.Encoder.24249—4.42% requests;
- Trojan.Encoder.11539—1.84% requests;
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During September 2018, 271,605 URLs of non-recommended websites were added to the Dr.Web database.
| August 2018 | September 2018 | Dynamics |
|---|---|---|
| + 538,480 | + 271,605 | - 49.5% |
Malicious and unwanted programs for mobile devices
In the past month, Doctor Web security researchers again detected the distribution Trojans of the Android.Click family on Google Play. Many of them were distributed under the guise of official programs of bookmakers’ offices. Upon cybercriminals’ command, these Trojans open bookmaker offices’ websites; however, at any moment, they can download any website, including fraudulent ones. Moreover, Android.Click.265.origin again penetrates Google Play. This Trojan was distributed under the guise of official software from well-known companies. Android.Click.265.origin downloads websites of premium services and automatically clicks the confirmation button to subscribe to expensive services.
Also, the following malicious programs were detected on Google Play in September: Android.Banker.2855, Android.Banker.2856, and Android.Banker.283.origin. They were hidden in programs that seem to be harmless at the first glance.
In the first autumn month of 2018, cybercriminals also distributed the dangerous Android.Spy.460.origin Trojan. It was designed for cyber espionage. Among other threats detected in September, new versions of commercial spyware were found, such as Program.SpyToMobile.1.origin, Program.Spy.11, Program.GpsSpy.9, Program.StealthGuru.1, Program.QQPlus.4, Program.DroidWatcher.1.origin, Program.NeoSpy.1.origin, Program.MSpy.7.origin, and Program.Spymaster.2.origin. These applications monitor SMS messages, call histories, detect device locations, copy contact lists to a remote server, and are able to steal browser histories and other private user information.
Among the most notable September events related to mobile malware:
- the detection of malicious applications on Google Play
- the distribution of spyware;
- the detection of a new commercial program designed for espionage for Android device users.
Find out more about malicious and unwanted programs for mobile devices in our special overview.