Doctor Web detects 130 fraudulent applications on Google Play
Real-time threat news | Hot news | All the news | Virus alerts
August 29, 2018
Cybercriminals use one of the malicious programs called Android.Click.265.origin to subscribe users to paid mobile services. This is a well-known type of network fraud, which has been popular among cybercriminals for many years. Android.Click.265.origin is spread under the guise of an official application designed to work with the online store of the “Eldorado” trade network. Doctor Web security researchers detected two instances of the Trojan attempting to appear in Google Play. At the moment this news article was posted, two modifications of the Trojan had been deleted from Google Play.
Android.Click.265.origin actually performed the functions its creators claimed. It downloaded the mobile version of the “Eldorado” online store on its window, allowing the program to work normally with the store. However, in addition to the intended functions, the Trojan performed several undesirable functions. For example, the Trojan displayed annoying advertisements and opened webpages to paid mobile services. Android.Click.265.origin also automatically clicked the subscription confirmation button. Following that, a victim’s mobile number was charged every day.
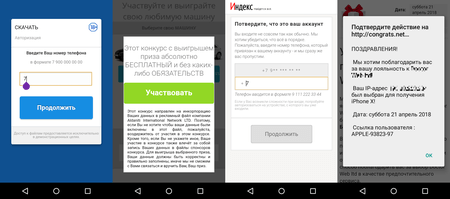
Android.Click.248.origin is another Trojan that is used in fraudulent schemes subscribing Android device owners to premium services. This malicious program, which had been detected by Doctor Web security researchers in April, was distributed via Google Play in August. As before, cybercriminals distribute Android.Click.248.origin as well-known software, for example, the client application of the “Youla” Internet notice board, the AliExpress online store, and the virtual voice assistant by Yandex—“Alisa”.
This Trojan opens one of the phishing websites where a user is invited to download a well-known program or to receive a reward. A potential victim is asked to provide their mobile number, which is supposedly required to receive a confirmation code. In reality, however, this code is required to confirm a subscription to a paid service. If an infected device uses a mobile network to connect to the Internet, an Android device owner is subscribed to a premium service automatically after the phone number has been entered on the fraudulent website. Below you can see examples of the fraudulent webpages downloaded by Android.Click.248.origin:
Additionally, among the malicious applications detected in August and distributed via Google Play, we should mention many other modifications of the Android.Click Trojan family. Representatives of this family examined by our security specialists were distributed under the guise of the official programs of bookmaker companies, including “Olymp”, “Mostbet”, “Fonbet”, “Liga stavok”, “1xBet, “Winline”, and others. In total, Doctor Web security researchers have detected 127 malicious programs distributed by 44 developers. These applications are being promptly deleted from Google Play; though, cybercriminals continue adding them to Google Play almost every day.
Once launched, these Trojans connect to the command and control (C&C) server and receive a command to download a website displayed to a user. Currently these specified malicious programs open official webpages of bookmakers, but the name of the Trojan application does not affect the downloaded website. In addition, at any moment, the C&C server can send a command to Trojans to download an arbitrary web resource, including fraudulent or malicious online portals from which other malicious programs can be downloaded to an Android device. This is why these Trojans pose a serious threat.
Another scammer Trojan detected in August was hidden in the “Opros” (meaning “survey”) application. It was added to the virus database as Android.FakeApp.110. Its authors promised a payment for participating in common surveys that did not last more than several minutes.
Once launched, Android.FakeApp.110 downloaded cybercriminals’ fraudulent website where a potential victim was prompted to answer simple questions supposedly from sponsors that were eager to pay a lot for participating in marketing research. For example, a user could be asked which perfume they preferred or the brand of their car.
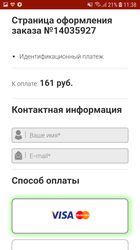
After answering some of these questions, the user was promised to receive a reward of dozens or even hundreds of thousands of rubles. At that, the user was warned that the money would be transferred partially within a certain period of time due to a payment system limit. However, there was a “possibility” to get the full amount of money. For that, the victim needed to make an identification payment of 100–200 rubles that supposedly confirmed the winner’s identity. This is the fraudulent scheme: victims willingly give their money to cybercriminals to receive the reward, but ultimately they do not get anything. Doctor Web security analysts have notified Google about this malicious application, and now it cannot be downloaded.
To take money from mobile device owners or to get other advantages, cybercriminals use various tricks and invent new scam schemes. Doctor Web reminds users to be careful when installing applications even from Google Play. It is necessary to pay attention on the developer’s name, publication date, and reviews from other users. These simple measures can decrease the risk that the mobile device will become infected. In addition, to protect Android devices, users are also recommended to install Dr.Web anti-virus products for Android which successfully detect and remove all known and undesirable applications.
Подробнее об Android.Click.265.origin
Подробнее об Android.Click.248.origin
Подробнее об Android.FakeApp.110
#Android, #мошенничество, #Google_Play, #троянец