August 2, 2018
The malicious software and utilities designed to mine cryptocurrency that we will focus on in this article were downloaded on one of our “honeypots” (special servers that are used by Doctor Web specialists as decoys for cybercriminals). First such attacks on Linux servers were detected by security researcher at the beginning of May 2018. Cybercriminals connected to the server via the SSH protocol, picked out the login and password by searching for them in a dictionary (bruteforce). After successful authorization on the server, cybercriminals disabled the iptables utility that manages firewall operation. Then, cybercriminals downloaded a mining utility and its configuration file to the attacked server. To launch the utility, they edited the /etc/rc.local file contents. After that, they terminated the connection.
In June, cybercriminals changed this scheme and started using malicious software that has been added to the Dr.Web virus databases under the name Linux.BtcMine.82. This Trojan is written in Go. It is a dropper that contains a packed miner in its body. The dropper saves the miner to the disk and launches it. Such scheme considerably simplifies the attack scheme. The e-wallet number for transferring mined cryptocurrency is hardcoded in the malware’s body.
Security researchers examined the cybercriminals’ server from which this Trojan was downloaded and detected several Windows miners there.
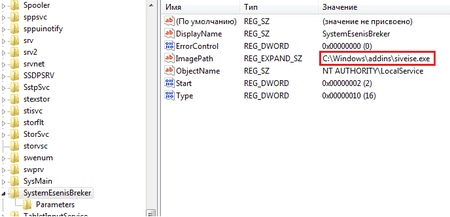
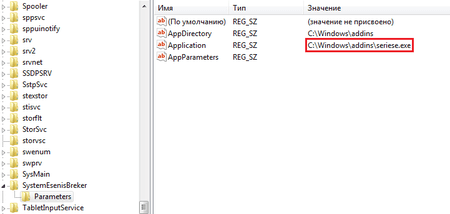
The Windows miner version is a self-unpacking RAR archive that contains a configuration file, several VBS scripts to launch the miner, and a utility to mine cryptocurrency. Once the archive is launched, the utility is unpacked to the %SYSTEMROOT%\addins folder and registers as the SystemEsinesBreker service.
32-bit and 64-bit miner versions for Windows are detected by Dr.Web Anti-virus as Tool.BtcMine. Our users are under reliable protection from malicious activities of these programs.
#Honeypot #Linux #cryptocurrency #mining #Trojan
![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments