July 31, 2018
In July 2018, cybercriminals again spread the dangerous Android backdoor named Android.Backdoor.554.origin, which has been known to Doctor Web virus analysts since April 2017. This Trojan spied on users and allowed cybercriminals to remotely control infected smartphones and tablets. Android.Backdoor.554.origin contained the hidden Windows worm, which was copied to a memory card connected to the mobile device for infecting computers running on Windows subsequently. Additionally, in the previous month, cybercriminals continued attacking Android smartphones and tablet owners using Trojans-bankers. One of them, named Android.Banker.2746, was detected in some applications in the Google Play catalogue. A number of other Trojan bankers were loaded malicious software on mobile devices by Android.DownLoader.753.origin, which also was present in the official Android catalogue. Besides, during July, cybercriminals spread other banking Trojans for the Android OS. Among them, Android.BankBot.279.origin has been detected, the Trojan that disguised itself as a useful application. Also in July, the virus analysts of Doctor Web discovered several new commercial spyware programs named Program.Shadspy.1.origin and Program.AppSpy.1.origin.
Principal trends in July
- The distribution of the backdoor which was spying on users and helping to infect computers running on Windows
- The appearance of malware in Google Play catalogue
- The distribution of Trojan bankers
Mobile threat of the month
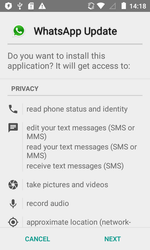
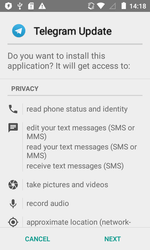
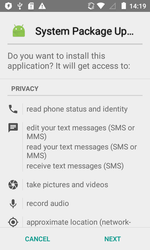
In July, the security specialists discovered another attack of the backdoor Android.Backdoor.554.origin on Android smartphones and tablets users. This Trojan is distributed being disguised as new versions of known software such as WhatsApp and Telegram, on the system or any other important updates.
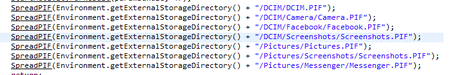
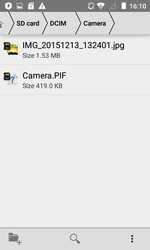
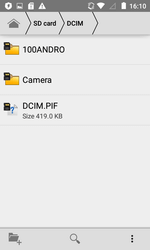
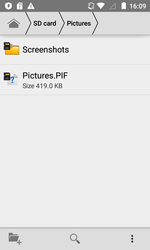
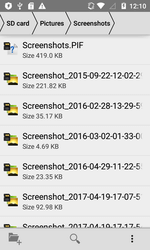
Android.Backdoor.554.origin was executing cybercriminals’ commands and was allowing them to control infected mobile devices and spy on its owner. The Trojan that was tracking the location of the Android-smartphone or tablet, was intercepting correspondence in popular messaging programs, accessed calls and SMS, was stealing contact information from the phone book and was performing other malicious activities. In addition, this backdoor was hiding the Windows worm in its file resources, which was named Win32.HLLW.Siggen.10482. After infecting the mobile device, Android.Backdoor.554.origin was copying the worm to the memory card, placing it in the catalogs with images. In this case, the executable file Win32.HLLW.Siggen.10482 with .pif extension was receiving the name of the directory in which it was located. As a result, when subsequently opening or copying these directories to a computer for viewing images, the user risked running the worm.
The following figure contains a directories list where the Trojan Android.Backdoor.554.origin was putting Win32.HLLW.Siggen.10482 worm:
The examples of successful copying of the executable file of the worm in directories with images on a memory card of the infected Android-device:
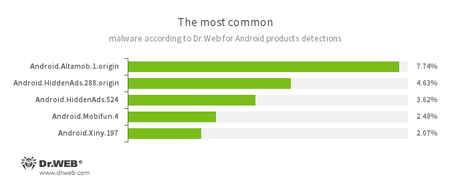
According to statistics collected by Dr.Web for Android
- Android.Altamob.1.origin
- The Trojan advertising platform, which downloads silently and launches malicious modules.
- Android.HiddenAds.288.origin
- Android.HiddenAds.524
- The Trojans, designed to display obtrusive advertising. They are distributed under the guise of popular applications by other malicious programs, which in some cases quietly install them in the system catalog.
- Android.Mobifun.4
- A Trojan that downloads other malware applications.
- Android.Xiny.197
- A Trojan designed for secretively downloading and installing other malicious applications.
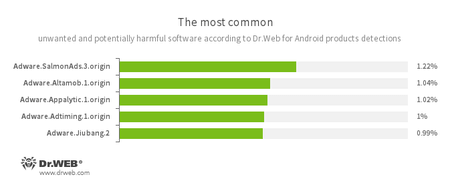
- Adware.SalmonAds.3.origin
- Adware.Altamob.1.origin
- Adware.Appalytic.1.origin
- Adware.Adtiming.1.origin
- Adware.Jiubang.2
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
Banking Trojans
In the previous month, information security specialists detected the Trojan in the Google Play catalogue, named Android.DownLoader.753.origin according to Doctor Web classification. This malicious program was distributed under the guise of financial applications. Some of its modifications did really perform the functions declared, while the rest were useless and were only offering to install the real banking software by downloading its pages in the Play Market.
Android.DownLoader.753.origin was downloading quietly from the remote server one of the banking Trojans of the Android.BankBot family and tried to install it, displaying the standard installation wizard.
In the middle of July, Doctor Web experts analyzed the Android banker, named Android.Banker.2746. Virus writers were distributing this Trojan through the Google Play catalog, disguising the malicious program as the official banking application.
Using it, they tried to access the customer accounts of one of the Turkish credit organizations. Android.Banker.2746 was displaying fake login and password boxes and intercepted SMS with one-time verification codes.
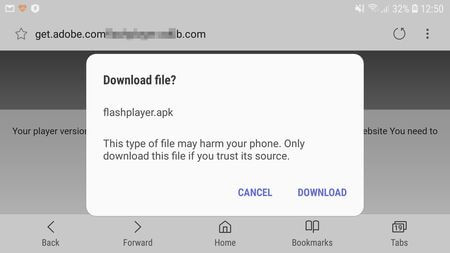
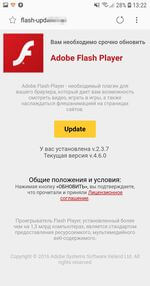
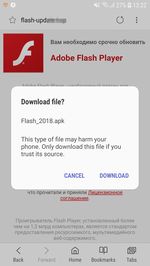
Among the banking Trojans that were attacking users in the parting month, was a malicious program Android.BankBot.279.origin. Cybercriminals were spreading it using fraudulent websites. Once a user visited one of the sites from a mobile device, the Trojan was loaded in the guise of innocuous and useful programs, such as Adobe Flash Player, online communication programs, VPN-clients and other software. Android.BankBot.279.origin was tracking the launch of banking applications installed on the smartphone or tablet and was showing a phishing login authorization form on top of their windows to access the user's account. In addition, the banker could change the pin code of the screen to unlock and block the infected device.
Examples of websites from which Android.BankBot.279.origin was downloaded on mobile devices or tablets:
Spyware
In the parting month, Doctor Web specialists discovered several new commercial spyware. One of them was named Program.AppSpy.1.origin. It tracks the location of the infected device, listens for phone calls and intercepts SMS messages. Another program for cyber espionage was added to the Dr.Web virus database as Program.Shadspy.1.origin. This application has extensive functionality. Program.Shadspy.1.origin monitors SMS correspondence, phone calls, device location, performs a recording of surroundings using the built-in microphone, copies history from the web browser, information about scheduled events from a user's calendar, can take snapshots using a smartphone or tablet camera and perform a number of other actions. In addition, with root privileges, Program.Shadspy.1.origin can intercept correspondence in Facebook and WhatsApp applications.
Banking Trojans pose a serious threat to mobile device owners. Cybercriminals continue to distribute these malicious programs not only through fraudulent sites, but also through the official directory of Google Play. To protect against these and other Android Trojans, users are recommended to use Dr.Web antivirus products for Android.
Your Android needs protection!
Use Dr.Web
- First Russian anti-virus for Android
- Over 135 million downloads—just from Google Play!
- Available free of charge for users who purchase Dr.Web home products