Cybercriminal earned millions targeting popular Steam gaming platform
Real-time threat news | Hot news | All the news | Virus alerts
May 30, 2018
“Faker” uses several methods to acquire his illegal income. The main scheme he developed is called MaaS (Malware As a Service). It implements a system for leasing out malicious programs on a subscription basis. Clients of “Faker” who want to profit from spreading Trojans are not required to provide anything except money and, in some cases, a domain: the virus writer provides them with the Trojan, access to the administrative panel, and technical support. Doctor Web’s analysts estimate that this turn-key solution has brought millions to its developer, and how much the clients have earned using this scheme is anybody’s guess considering that the money spent on a month’s subscription could be recouped in a day. All the malicious programs created by “Faker” pose a threat to users of the popular Steam gaming service.
Steam, a platform developed by Valve Corporation, is designed to digitally distribute computer games and programs. A registered Steam user gains access to a dashboard with information on all the games and applications they’ve purchased. In addition, they can make purchases in the Steam shop, buying various digital content and also selling and exchanging collectibles. These collectibles have a key value in various multiplayer games. Weapons, ammunition, and different items allow the gamer’s visual appearance and the visual representation of his belongings in a game to be changed. Collectibles can be exchanged on special websites and also bought and sold for real money. This was the base on that “Faker” built his criminal business.
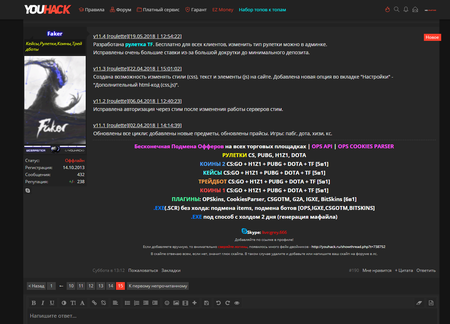
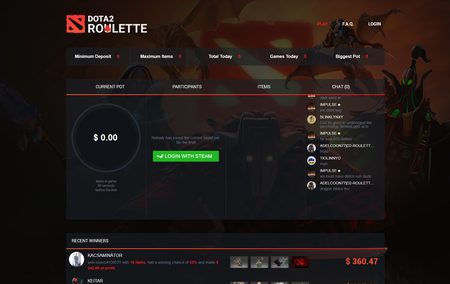
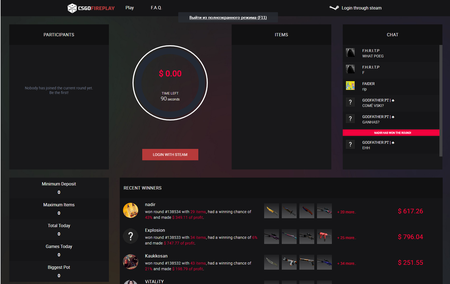
One of his methods for making money involved so-called “roulettes”. That’s what network players call the peculiar auctions in which several participants simultaneously list various collectibles. The possibility of winning depends on the amount bid by the participant, and the winner gets all the listed items. What’s fraudulent is that the real player is opposed by special bots that are guaranteed to win the bid. Sometimes a potential victim is offered the opportunity to administer one of these games and is even allowed to win several times before listing some expensive collectible that is sure to be lost to cybercriminals.
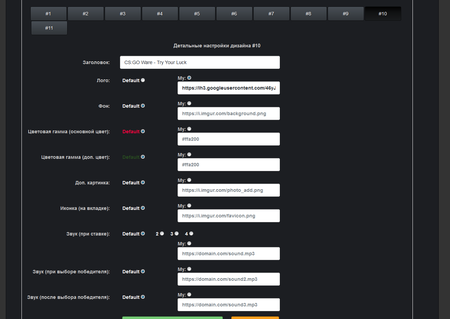
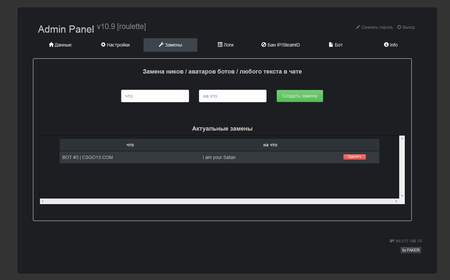
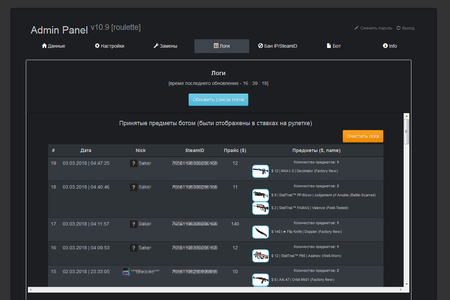
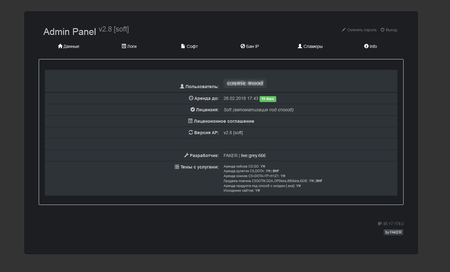
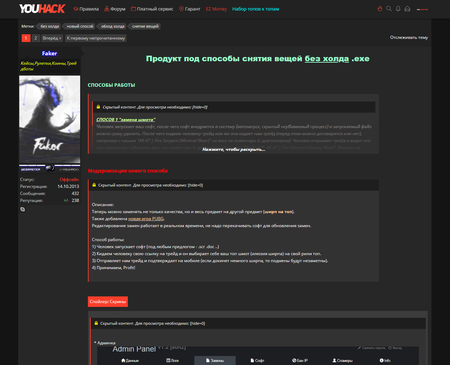
The “roulettes” administrative panel allows for the flexible configuration of the auction website’s visual appearance and its displayed contents; it permits names and text in the chat located on the website to be changed, bids to be controlled, and the list of collectibles received from other players to be viewed. It can also be used to fully control the “roulette”.
In addition, “Faker” lends his malicious programs to other cybercriminals. One of them was dubbed Trojan.PWS.Steam.13604; it was designed to steal Steam user account data. Under the terms of a monthly subscription, the creator of the Trojan provides cybercriminals with a malicious file assembled specially for them; he also gives them dashboard access.
The Trojan is spread using several methods. One of them uses social engineering techniques: a Steam user receives a message that several community members need a new player for a team. After one collective match, for the purpose of making further collaborations convenient, the potential victim is prompted to download and install a client for voice calls. Cybercriminals send the victim a link to a fake website for this application. When the victim clicks on the link, a Trojan disguised as a program is downloaded.
If a potential victim already uses TeamSpeak, they receive the server address used by a team of players for communication. After connecting to this server, the victim sees a window suggesting that they update one of TeamSpeak’s components and an audio subsystem driver. Disguised as this update, the malicious program is downloaded to the computer.
When launched, the Trojan unloads the Steam process (if this process is not its own) and then determines the path to the Steam directory, the application language, and the user name. If one of the Steam system files is available, Trojan.PWS.Steam.13604 extracts from it pairs consisting of steamid64 identifiers and account names. Then the Trojan sends the information collected on the infected computer to the command and control server. This includes the operation system version, the user name and the machine name, the OS language, the path to Steam, the language version of this application, etc.
When the indicated actions are performed, the malicious program removes the original Steam file and copies itself to its location. To prevent the user from updating Steam and getting technical support, the Trojan changes the contents of the hosts file by blocking access to the websites steampowered.com, support.steampowered.com, store.steampowered.com, help.steampowered.com, forums.steampowered.com, virustotal.com, etc. Then Trojan.PWS.Steam.13604 displays a fake Steam authorization window. If the victim enters their login credentials, the Trojan tries to use them to authorize on Steam. If this attempt is successful and Steam Guard—a two-factor authentication system for protecting user accounts—is enabled on the computer, the Trojan displays a fake window for inputting the authorization code. All this information is sent to the cybercriminals’ server.
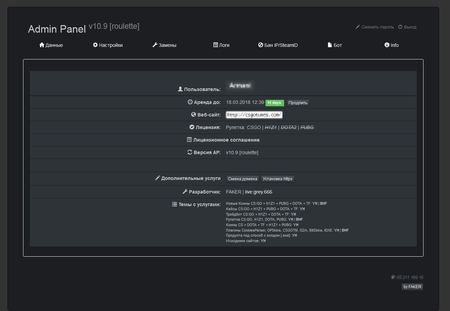
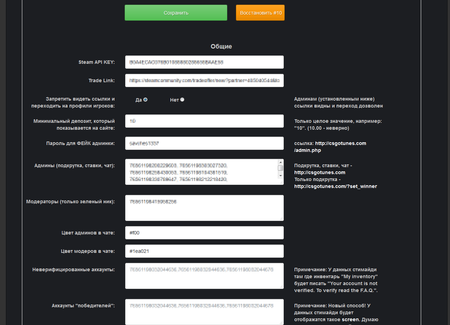
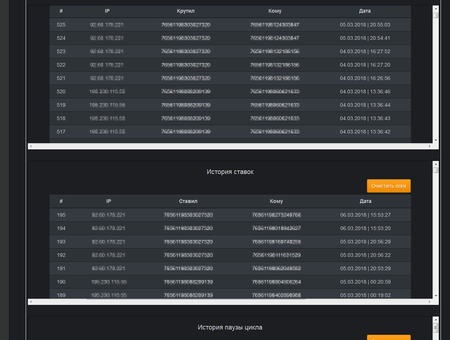
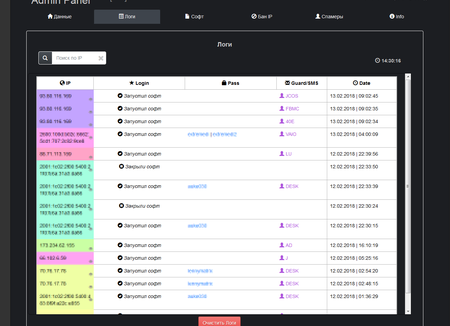
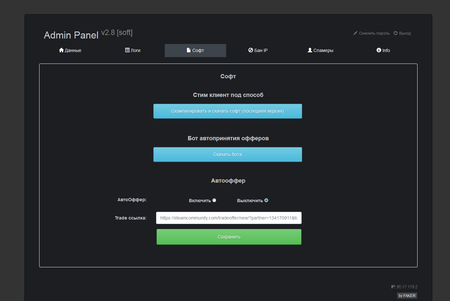
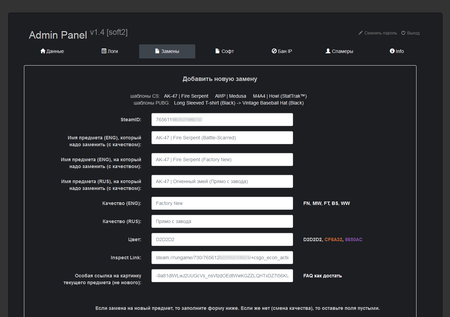
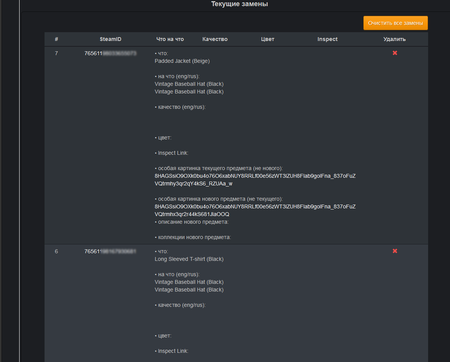
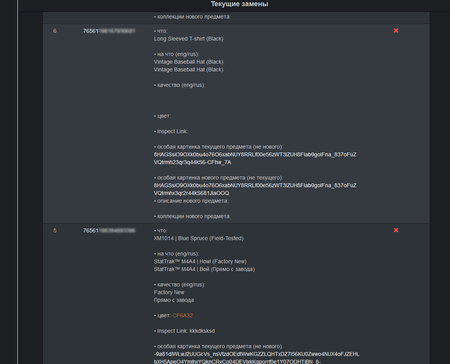
For all of his clients, the virus writer uses the same command and control server. The obtained data forms a file that cybercriminals use to access the victim’s Steam account. The administrative panel interface of Trojan.PWS.Steam.13604 is shown on the following images:
In addition to Trojan.PWS.Steam.13604, “Faker” leases out one more Trojan he has created. It was dubbed Trojan.PWS.Steam.15278. This malicious program is distributed in a similar way and is designed to steal gaming inventory from Steam users. Cybercriminals can sell the virtual items they’ve stolen to other gamers. The virus writer also advertises the leasing service for this malicious program on special forums.
To operate, Trojan.PWS.Steam.15278 uses Fiddler, a free tool for analysing traffic when it’s transferred via the HTTP protocol. it operates on the principle of a proxy server. Fiddler installs a root certificate in the system, which allows Trojan.PWS.Steam.15278 to intercept encrypted HTTPS traffic. The Trojan intercepts server responses and changes their data.
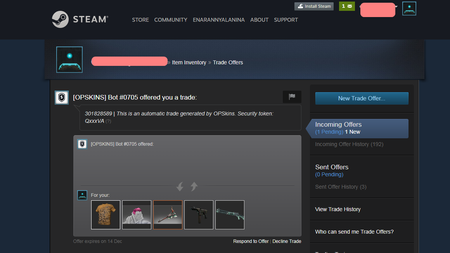
If someone who is using the infected machine exchanges items with other gamers on specially designed markets, such as opskins.com, igxe.cn, bitskins.com, g2a.com, csgo.tm, market.csgo.com, market.dota2.net and tf2.tm, the Trojan changes the recipient of the collectible the moment the exchange deal is made. This happens in the following way. When the Trojan’s victim lists gaming items for sale or exchange, the malicious program connects to their account and at regular time intervals checks the incoming offers. If the user of the infected computer who listed any item for exchange receives a request for a deal, the Trojan cancels this offer, determines the user name, their user icon and the text message from the original request, and sends the victim absolutely the same request but on behalf of the cybercriminals’ account. Physically, this swap is implemented using web injections: Trojan.PWS.Steam.15278 injects the malicious code it receives from the command and control server into webpages. It is notable that “Faker” is the author of other Trojans that operate in a similar fashion and are implemented as an extension for Google Chrome.
When exchanging items via the official website steamcommunity.com, Trojan.PWS.Steam.15278 allows cybercriminals to replace the display of the user’s collectibles. The Trojan modifies the contents of the steamcommunity.com service’s webpages in such way that a potential victim sees an offer for a very expensive and rare collectible. If the user approves the deal, they will get some trivial and cheap inventory item instead of the item they expect. It is almost impossible to dispute the unfair exchange afterwards because from the server’s point of view, the user made this exchange willingly and of their own accord. For example, on the steamcommunity.com service’s page, the user of the infected computer will see that another user is supposedly offering to exchange a collectible called “PLAYERUNKNOWN's Bandana” which is worth $265.31. In reality, after the deal is sealed, the user will get “Combat Pants (White)”, and the price of this item will be just $0.03.
In general, the dashboard of Trojan.PWS.Steam.15278 is similar to the administrative panel of Trojan.PWS.Steam.13604; however, the updated version has an additional section that allows cybercriminals to control the substitution of collectibles when exchange deals are made. They can configure images and descriptions of collectibles that are to be substituted for real ones and displayed to the victim. Afterwards, the cybercriminals can sell the illegally obtained collectibles for real money on network trading platforms.
Dr.Web Anti-virus successfully detects and removes all known modifications of Trojan.PWS.Steam.13604 and Trojan.PWS.Steam.15278; therefore, these malicious programs pose no threat to our users. Doctor Web specialists notified Valve Corporation about the compromised user accounts and also about the accounts used for the fraudulent scheme described above.
More about Trojan.PWS.Steam.13604
More about Trojan.PWS.Steam.15278
#malicious_software #gamer #games #Trojan