April 28, 2018
In April 2018, Doctor Web detected the spreading of a dangerous banking Trojan Android.BankBot.358.origin, which infected over 60,000 mobile devices of Russian users. Over the course of the month, virus analysts also detected numerous Android.Click Trojans distributed via Google Play. Android.RemoteCode.152.origin was also detected on Google Play. It downloaded other malicious modules and used them to create advertising banners, then it tapped on them, generating profit for cybercriminals. Riskware Program.PWS.2 was found on Google Play. It provided access to Telegram, which had been blocked in Russia. However, this riskware did not provide the required confidential data protection. Among the malicious Android applications detected in April was also such spyware as Android.Hidden.5078, Android.Spy.443.origin and Android.Spy.444.origin.
PRINCIPAL TRENDS IN APRIL
- Mass spreading of a banking Trojan among Russian users of mobile Android devices
- The detection of malicious programs and riskware on Google Play
- The detection of new spyware Trojans for Android
Mobile threat of the month
In the past month, Doctor Web reported the spreading of a banking Trojan Android.BankBot.358.origin that infected over 60,000 Android smartphones and tablets. Most of these devices belonged to Russian users. The main target for Android.BankBot.358.origin were clients of a major bank.
The Trojan was spread using various fraudulent SMS messages that suggested users follow a link to read information on advertisements, loans and money transfers. If a potential victim tapped the link, they would be directed to a website that loaded the banker to a mobile device.
To steal money from accounts, the Trojan used SMS commands for managing mobile banking. So even if a victim’s device did not have the official application of a major bank installed, infected devices’ owners could lose their money. The cybercriminals’ attack resulted in threatening over 78,000,000 rubles of the major bank’s clients. More information regarding Android.BankBot.358.origin can be found in our report.
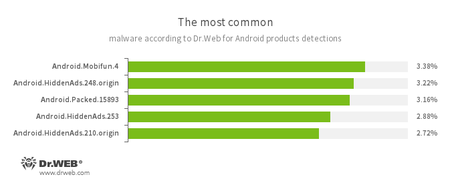
According to statistics collected by Dr.Web for Android
- Android.Mobifun.4
- A Trojan designed to download other Android applications.
- Android.HiddenAds.248.origin
- Android.HiddenAds.253
- Android.HiddenAds.210.origin
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs, which sometimes covertly install them in the system directory.
- Android.Packed.15893
- Detection for Android Trojans protected by a program packer.
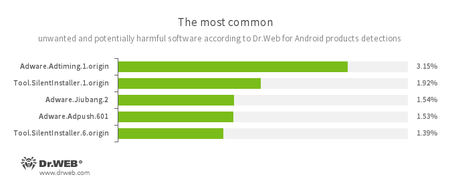
- Adware.Adtiming.1.origin
- Adware.Adpush.601
- Adware.Jiubang.2
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
- Tool.SilentInstaller.1.origin
- Tool.SilentInstaller.6.origin
- Riskware designed to silently launch applications without the user’s action.
Threats on Google Play
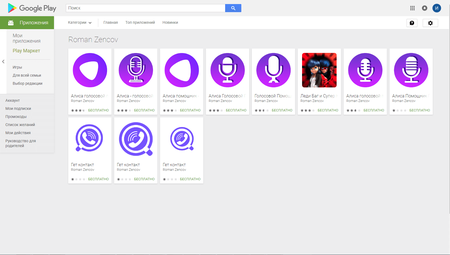
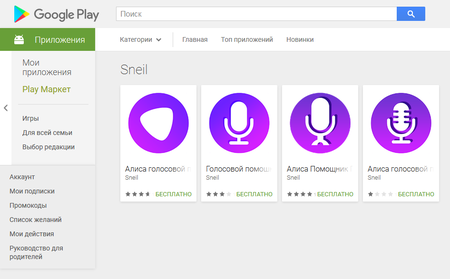
In the past month Doctor Web specialists found many new malicious programs on Google Play. Among them were various Android.Click Trojans. For example, in mid-April signatures of Android.Click.245.origin were added to the Dr.Web virus database. Cybercriminals distributed this Trojan on behalf of developers Roman Zencov and Sneil and disguised it as popular applications.
Once launched, the Trojan downloaded websites specified by cybercriminals. These websites were used to trick users into signing up for expensive content services. If potential victims’ devices connected to the Internet via a mobile network, the subscription was performed automatically upon tapping on several buttons on these websites. More information regarding one of such cases can be found in the Doctor Web’s article.
Later in April virus analysts found similar malicious programs on Google Play. They were added to the Dr.Web virus database as Android.Click.246.origin and Android.Click.458. Similar with Android.Click.245.origin, cybercriminals also distributed these Trojans as benign programs. For example, cybercriminals disguised as mendozapps added around 40 such malicious applications on Google Play.
Developers Trinh Repasi and Vashashlaba disguised a similar Trojan Android.Click.248.origin as Viber and Avito applications. This malicious program is written in Kotlin. It checks infected devices’ IP address and, depending on a user’s location, receives an assignment to load specific websites. Cybercriminals control Android.Click.248.origin via the Firebase cloud service.
In late April Doctor Web virus analysts detected Android.RemoteCode.152.origin on Google Play. It was hidden in benign programs. This malicious program covertly downloaded and launched additional modules used to create invisible advertising banners. The Trojan independently tapped on these banners, bringing profits to the virus writers who created them. More detailed information about Android.RemoteCode.152.origin can be found in the corresponding article on our website.
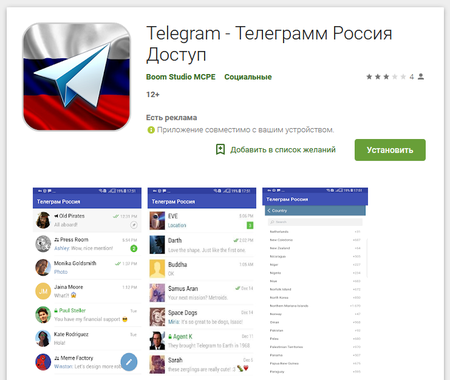
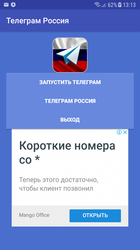
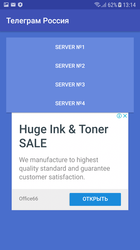
In April Doctor Web specialists also detected the riskware Program.PWS.2 on Google Play. It allowed working with Telegram, which had been blocked in Russia.
This application operates via an anonymizer but does not encrypt transferred login credentials and other confidential information. That said, all personal user information is at risk. Doctor Web reported on a similar dangerous program in June 2017.
Icon of Program.PWS.2 and running application’s interface are presented in the Figures below:
Spyware
In April new spyware was detected. These spying Trojans stole confidential information of Android smartphone and tablet users. One of them was added to the Dr.Web virus database as Android.Hidden.5078. This malicious program stole correspondence from popular messengers such as Viber, Facebook Messenger, WhatsApp, WeChat, Telegram, Skype, Weibo, Twitter, Line and others. When creating the Trojan, cybercriminals used code obfuscation and anti-debugging to avoid detection by anti-viruses and to make Trojan’s analysis difficult.
Other Android spyware detected in the past month were dubbed Android.Spy.443.origin and Android.Spy.444.origin. The Trojan, which is added to the Dr.Web virus database as Android.DownLoader.3557, was disguised as a settings module. It downloaded and installed them on mobile devices. This loader was distributed via Google Play as an online-messenger called Dardesh.
Once launched, Android.DownLoader.3557 suggested a potential victim install a component, which is supposedly required for the program’s operation and in reality was one of the spying Trojans.
Once installed and launched, Android.Spy.443.origin and Android.Spy.444.origin started tracking mobile device user’s actions. They tracked an infected smartphone or tablet’s location, obtained information on all available files, sent cybercriminals the user’s documents, sent and stole SMS messages, recorded the environment using the device’s microphone, recorded video, intercepted phone calls, stole data from the contact list and performed other actions.
Cybercriminals continue to actively distribute Android Trojans using not only fraudulent websites but also Google Play. Doctor Web recommends mobile device owners install Dr.Web for Android to protect their mobile devices from malicious and unwanted applications.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products