April 5, 2018
Dr. Web has known of Android.BankBot.358.origin since the end of 2015. Virus analysts have determined that new modifications of Android.BankBot.358.origin are designed to attack Russian Sberbank clients and have already infected more than 60,000 mobile devices. However, virus writers spread numerous different versions of this malicious application, so the number of victims can be significantly higher. In total, cybercriminals could steal more than 78,000,000 rubles from the bank accounts of infected devices. Cybercriminals could also steal over 2,700,000 rubles from mobile phone accounts.
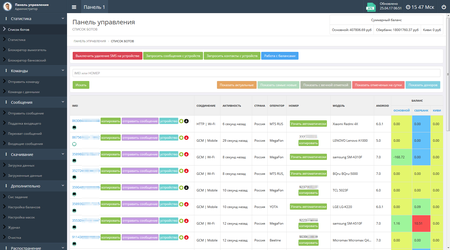
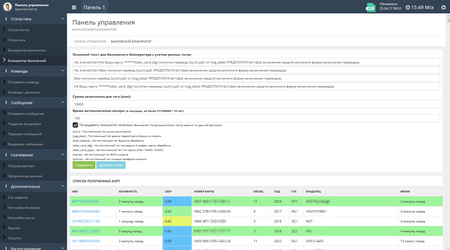
The following figures show the administration panel sections of Android.BankBot.358.origin with information on infected devices and statistics on one of the detected botnets:
This banking Trojan is distributed by fraudulent SMS messages that can be sent by cybercriminals and the malicious program itself. The messages are mostly sent on behalf of Avito.ru users. These SMS messages invite the victim to follow the link and supposedly become familiar with the reply to the posted ad. For example, the following text is popular: “Good day, are you interested in an exchange?”. In addition, sometimes mobile device owners receive fake notifications about loans, mobile transfers and credited funds to a bank account. Below you can see examples of phishing messages that have been sent in the administration panel of the Trojan’s server and sent upon the cybercriminals’ command:
When following the link from such message, the victim sees the cybercriminals’ website, from which a mobile device downloads a malicious APK file. To make it more convincing, cybercriminals use the real Avito label in Android.BankBot.358.origin, increasing the possibility of a successful Trojan installation upon its download. Some of the banker’s modifications can be distributed as other programs - for example, software for operation with the Visa and Western Union payment systems.
Upon the first launch, Android.BankBot.358.origin requests access to the device administrator rights and persists until a user gives up and grants it all the required privileges. After obtaining all the necessary privileges, the Trojan displays a fake message about an installation error and deletes its icon from the list of programs on the home screen. Essentially, Android.BankBot.358.origin tries to hide itself on a smartphone or a tablet. If a user later tries to remove the banker from the list of administrators, Android.BankBot.358.origin activates a self-protection function and shuts down the respective system settings window. In addition, some Trojan versions also install their own lock screen PIN codes.
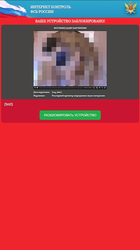
After infecting a device, Android.BankBot.358.origin establishes a connection with the command and control server, informs it of the successful infection and waits for further instructions. The Trojan’s main goal is to steal money from Sberbank’s Russian-speaking clients. The main attack vector is phishing. Cybercriminals send the Trojan a command to block an infected device with a window with a fraudulent message. It imitates the appearance of Sberbank Online, the remote banking and payment system, and is displayed to all users no matter whether they are Sberbank or another financial organization’s clients. This message notifies clients of a received money transfer in the amount of 10,000 rubles. To receive the money, the smartphone or tablet owner is invited to provide full bank card information: its number, holder’s name, expiration date, and the CVV code. Additionally, this malicious window cannot be closed without the input of the all required data, and the device stays blocked. As a result, a user has to confirm “crediting to the bank account”, then the bank card information is sent to cybercriminals, and they can freely steal all the money from the victim’s bank account.
However, at the moment this news article has been posted, the existing modifications of the Trojan have not performed full check of bank card information and have removed the block after an input of any data. As a result, the mobile device owners who have suffered from Android.BankBot.358.origin can get rid of the phishing window and use the anti-virus to remove the malicious program. For this purpose, input an arbitrary card number in the fraudulent form. The card number consists of 16 or 18 numbers. You should also specify a random expiration date from the period between 2017 and 2030. By no means should you input information of the real Sberbank or any other card, because cybercriminals will get a full access to it.
Nevertheless, nothing prevents virus writers from another blocking of a smartphone or a tablet after penetrating the deception. Therefore, when the phishing window is closed, it is necessary to scan the device with the anti-virus as soon as possible and remove the Trojan: https://download.drweb.ru/android/
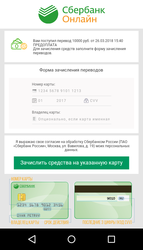
If a user uses the Mobile banking service, Android.BankBot.358.origin tries to use it to steal money from the victim’s account. The malicious program covertly sends SMS messages with commands to perform operations in the online banking system. The Trojan checks the current balance of the user’s card and automatically transfers money to the cybercriminals’ bank account, or to their mobile account. The example of Android.BankBot.358.origin stealing money via the remote banking service is shown in the following figure:
To obtain additional income, some versions of Android.BankBot.358.origin can block an infected device with a ransom message demanding that the victim pay a fine for watching prohibited videos. In order to hide their malicious activity (for example, suspicious SMS messages), various Trojan’s modifications can also block the screen of an infected smartphone or tablet with a notification that some system update was installed.
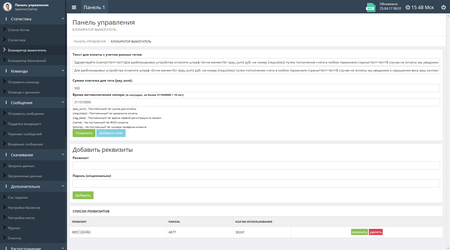
Virus writers can configure the parameters of blocking windows in the administration panel of the command and control server. For example, set texts of displayed messages, their display duration and a required ransom amount. Below are examples of the corresponding sections of the control panel:
Along with stealing money and blocking infected devices, Android.BankBot.358.origin can perform other malicious actions. When the Trojan receives commands from cybercriminals, it can:
- Update itself;
- Send SMS messages to all contact list numbers;
- Send SMS messages to all numbers specified in commands;
- Load websites specified by cybercriminals;
- Send to the server all saved SMS messages from the device;
- Obtain information on contacts from the contact list;
- Create fake incoming SMS messages.
Dr.Web for Android has successfully detected all the known modifications of Android.BankBot.358.origin, so the Trojan does not pose any threat to our users. Doctor Web specialists have sent information about the Trojan to Sberbank and continue to monitor the situation.
#Android #banker #mobile #ransom #banking_Trojan
Your Android needs protection!
Use Dr.Web
- First Russian anti-virus for Android
- Over 135 million downloads—just from Google Play!
- Available free of charge for users who purchase Dr.Web home products




![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments