Doctor Web: banking Trojan Android.BankBot.149.origin has become a rampant tool of cybercriminals
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
March 20, 2018
At the time it appeared, Android.BankBot.149.origin was a banking Trojan with a typical set of functions. The Trojan showed phishing windows that have been used to steal the usernames and passwords of accounts of online banking systems of various credit organizations, have been stealing information about bank cards, and have also been able to intercept incoming SMS to gain access to one-time passwords for money transfer confirmations. When the source code of this malware became available to everyone, the virus writers began creating a number of similar Trojans on its basis. At the same time, criminals actively distributed them through Google Play. Among these banking Trojans have been Android.BankBot.179.origin, Android.BankBot.160.origin, Android.BankBot.163.origin, Android.BankBot.193.origin and Android.Banker.202.origin, which virus writers disguised as innocuous and useful applications.
Another Trojan, which code has been used by cybercriminals, has been added to the Dr.Web virus database as Android.BankBot.250.origin. Trojan is also known as Anubis. Doctor Web virus analysts have found out the first versions of this malicious program in November 2017. These modifications of the Trojan were copying the capabilities of Android.BankBot.149.origin almost completely.The banking Trojan has been able to perform the following actions:
- sending SMS messages with the given text to the number specified in the command;
- executing USSD requests;
- sending copies of SMS messages stored on the device to the managing server;
- receiving information about applications installed;
- showing dialog boxes with the text specified in the command;
- requesting additional work permits;
- showing push notifications whose contents are specified in the command;
- showing a push-notifications whose contents are set in the Trojan's code;
- blocking the screen of the device window WebView, which showed the content received from the server web page;
- sending all the numbers from the contact list to the server;
- sending SMS messages to all numbers from the contact list;
- accessing information about device and its location;
- requesting access to accessibility features (Accessibility Service);
- learning the IP address of an infected smartphone or tablet;
- cleaning up its configuration file and stopping own work.
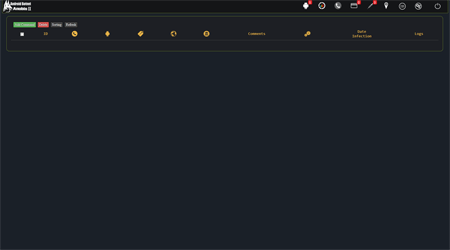
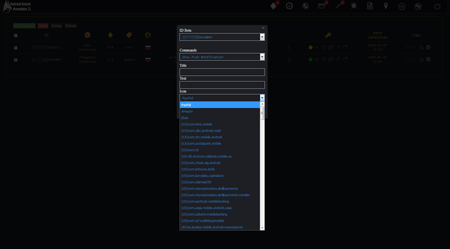
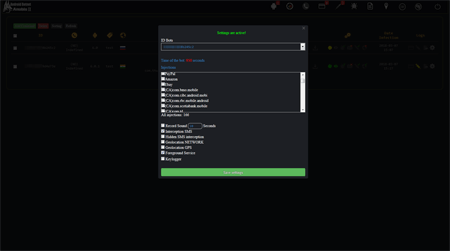
On the pictures below the example of the Android.BankBot.250.origin Trojan’s control panel is displayed:
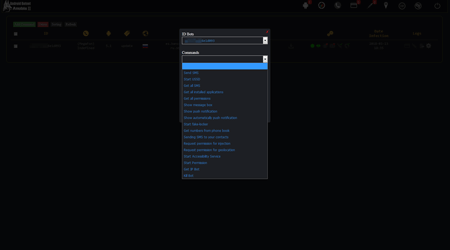
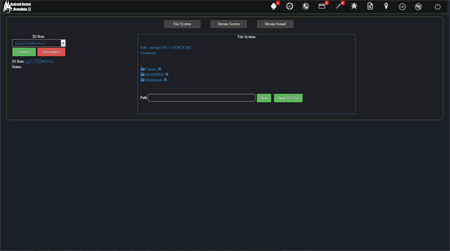
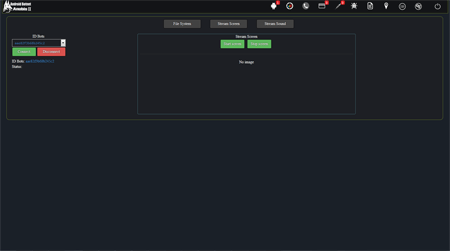
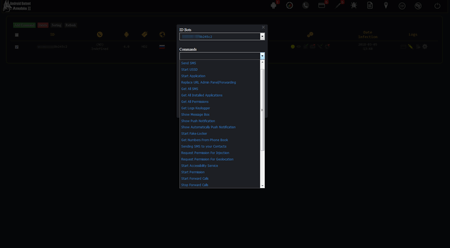
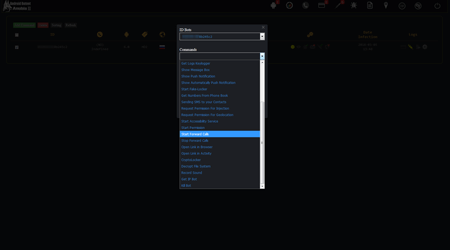
However, with the appearance of Android.BankBot.250.origin updates, its functionality expanded gradually. One of the Trojan’s new versions, named Android.BankBot.325.origin, contains the possibility of remote access to infected devices. As a result, the banking Trojan could work as a remote administration utility or RAT (Remote Administration Tool). One of its new features is the ability to view a list of files that have been stored in the memory of infected smartphones or tablets, downloading any of the files to the management server, as well as deleting them. In addition, the Trojan was able to monitor everything that was happening on the screen, making screenshots and sending them to criminals. By the command of virus writers Android.BankBot.325.origin was also able to listen to its surroundings using the built-in microphone. Therefore, the Trojan could be used for cyber espionage. The following images display the section of the administration panel of the Trojan's management server where the criminals were able to give the Trojan a corresponding command:
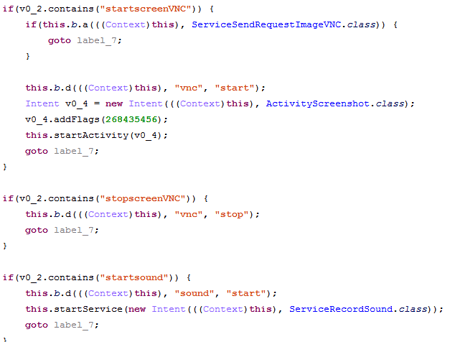
At the same time, the analysis of the banking Trojan has stated that virus writers use the abbreviation "VNC" in the methods’ names, as well as in the control commands, which stands for Virtual Network Computing and refers to the remote access to the desktop system. However, it is not implemented in the Android.BankBot.325.origin Trojan, and the criminals only use its name for their own convenience. Nevertheless, it is possible to conclude that cybercriminals began developing the ability to control the screen of infected devices remotely and to turn a banking Trojan into a more universal malicious application. Below is a fragment of the Android.BankBot.325.origin code displayed where the above-mentioned abbreviation is used:
One of the latest modifications Android.BankBot.325.origin, which has been examined by Doctor Web virus analysts, received more functions. The list of banking Trojan potential now includes:
- sending SMS messages with the given text to the number specified in the command;
- executing USSD requests;
- launching applications;
- changing a managing server’s address;
- sending copies of SMS messages stored on the device to the managing server;
- receiving information about applications installed;
- intercepting the characters entered on the keyboard (keylogger);
- requesting additional work permits;
- showing dialog boxes with the text specified in the command;
- showing push notifications whose contents are specified in the command;
- showing push notifications whose contents are set in the Trojan's code;
- sending all the numbers from the contact list to the server;
- sending SMS messages to all numbers from the contact list;
- blocking the screen the WebView device window, which showed the content received from the server web page;
- requesting access to accessibility features (Accessibility Service);
- redirecting phone calls;
- opening in browser website addresses, specified in the commands;
- opening links to web pages using WebView;
- filing encrypting and ransom requiring;
- decrypting files;
- recording the surroundings using the device's microphone;
- accessing the information about the device and its location;
- obtaining the IP address of the device;
- cleaning the configuration file and stopping the Trojan.
The following figures demonstrate the list of commands that criminals are able send to a banking Trojan through the administration panel:
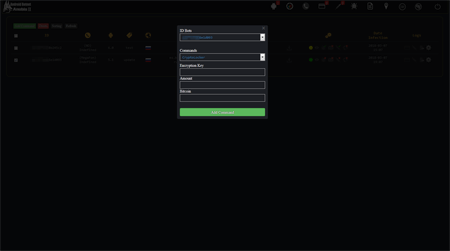
Most of the commands sent to the banking Trojan are configured in the same panel. For example, the figure below demonstrates the configuring of the file encryption settings. Virus writers can set the encryption key, the ransom amount (for example, in bitcoins) that Android.BankBot.325.origin will request from the victim, as well as their e-wallet number for the transfer:
Fake notifications can be set up in the same panel, which should cause the user to run the application necessary to cybercriminals. Immediately after the launch of the target application, the Trojan displays a phishing form, containing login, password and other sensitive information requests over its window and passes it to the virus writers.
Similarly, phishing windows are configured with additional parameters:
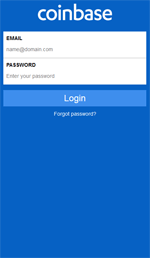
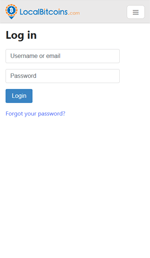
Android.BankBot.325.origin origin displays fake authorization forms when launching over 160 programs, including software for accessing banking services, payment systems and social networks. At the same time, popular applications for working with crypto-currencies have been added. Android.BankBot.325.origin origin is not the first banking Trojan that tries to steal logins and passwords from such programs; but within it, criminals tried to create the appearance of phishing windows resembling the interface of real applications. Examples of such fraudulent authorization forms are displayed in the following figures:
Virus analysts have determined that the Trojan is attacking users from Russia, Ukraine, Turkey, England, Germany, France, the USA, Hong Kong, Hungary, Israel, Japan, New Zealand, Poland, and Romania. However, this list can be updated with other states any time cybercriminals show interest in them.
Doctor Web specialists expect that the authors of Android.BankBot.325.origin will continue to improve the functionality of the Trojan and will be introducing new features for remote management of infected smartphones and tablets. It is possible that additional spy functions will appear in the Trojan. Dr.Web anti-virus products for Android successfully detect all known modifications to this malicious application, so they do not pose any threat to users.
#Android #banking Trojan #bitcoin
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products