Doctor Web: cybercriminals use fake popular Android applications for phishing
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
March 13, 2018
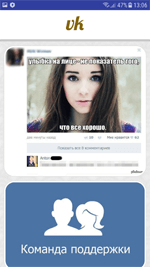
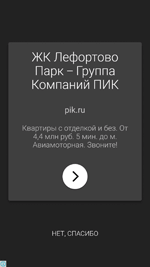
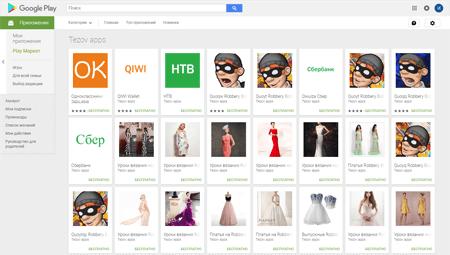
The detected programs have the same names and similar icons as popular applications. Doctor Web security researches have found fake QIWI app software (Russian payment service provider), Sberbank Online, Odnoklassniki and VK (popular social networks), and NTV (Russian television channel). Below, you can see how cybercriminals trick potential victims. In the left illustration you can see the fake application page, which can be easily found on Google Play. In the right illustration, you can see the genuine software page.
Every time the fake applications are launched, they connect with the command and control server. The server responds with the “none” parameter, or sends the web link specified by cybercriminals. When the parameter is received, the malicious programs extract several images from their resources and show them to users. If the malicious programs receive the web link from the C&C server, they load the web page and display it. The page is then opened via WebView directly in the applications. Users do not see the link to the target Internet address. That said, the contents of the demonstrated web pages can vary. For example, smartphone users can see fake login forms of online banking systems or social networks. This puts Android smartphones and tablets owners at risk of phishing attacks. This feature poses a serious threat, so this software has been added to the Dr.Web virus database as Android.Click.415.
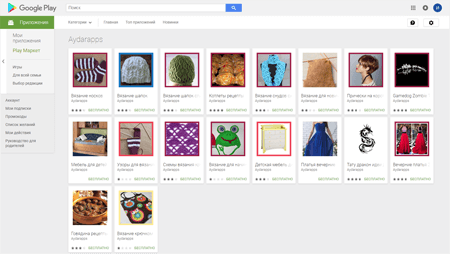
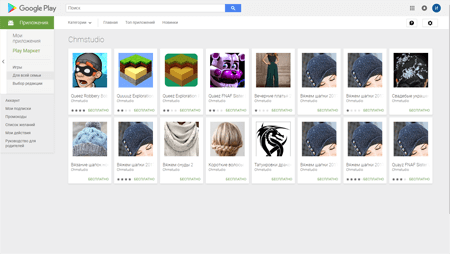
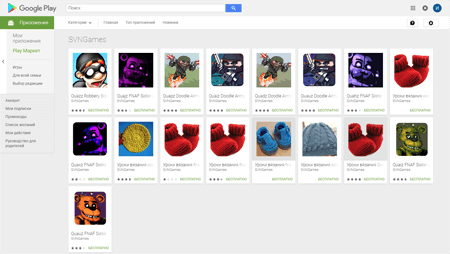
Apart from the mentioned Trojans, Doctor Web security researchers detected more than 70 similar programs. Over 270,000 users have downloaded them. Fake games, recipes collections, and knitting manuals can be found among these applications. Some of them really perform the named functions. However, like the Android.Click.415 Trojan they also can receive links to any web pages from the C&C server. Then, they load and show these web pages to the users. These programs are also added to Dr.Web virus database. They are detected as Android.Click.416 and Android.Click.417. Moreover, while functioning, various modifications of malicious applications constantly show advertisements on the mobile device screen.
At least four software developers distributed the Trojans: Tezov apps, Aydarapps, Chmstudio, and SVNGames. Doctor Web security analysts have notified Google about all detected malicious applications. However, at the moment of the publication of this news, the applications still were available for downloading.
Doctor Web reminds users that it is necessary to pay attention on the software developer name even if you install the application from such dependable sources as Google Play. Cybercriminals can copy the apps’ appearance and use similar names to make users install fake apps that can be found easily in the software distribution services. Dr.Web anti-virus products for Android detect and delete all known modifications of Android.Click.415, Android.Click.416, and Android.Click.417. So, these Trojans do not pose any threat to our users.
- More about the Android.Click.415 Trojan
- More about the Android.Click.416 Trojan
- More about the Android.Click.417 Trojan
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products