March 2, 2018
The Trojan, dubbed Android.BankBot.344.origin was hidden in an application called “VSEBANKI – Vse banki v odnom meste” (ALLBANKS – all banks in one place). Cybercriminals uploaded it to Google Play on February 25, and less than 500 mobile users actually downloaded the app. The authors also took the trouble to add fake reviews on behalf of the “lucky” users. Doctor Web specialists informed Google about the Trojan, and it was quickly deleted from Google Play.
The design of the Trojan distributed on Google Play under the guise of a banking application.
Android.BankBot.344.origin is a modification of Android.BankBot.336.origin, a malicious program that was detected on February and was also distributed via Google Play. Unlike the previous version that attacked Ukrainian users, the updated Trojan is designed for Russian banks’ clients. Similar to the previous modification, cybercriminals pass Android.BankBot.344.origin off as the application, which supposedly provides online access to financial services of various credit organizations. In fact, the claimed functionality didn’t exist.
The list of Russian banks which online accounts the user can supposedly access via the application.
The Trojan invited users to sign into an existing mobile banking account using their logins and passwords or to input bank card information. Once victims input confidential data, the program sent it to cybercriminals. As a result, they could steal mobile users’ money. Like the previous Trojan’s version, Android.BankBot.344.origin was able to intercept incoming SMS messages.
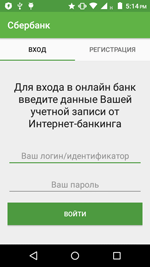
An example of phishing input form. Login credentials are requested to get access to online banking of one of the credit organizations.
An example of phishing input form. A user is invited to sign in and input their bank card information.
Doctor Web highly recommends that users install only the official applications of credit organizations when using online banking systems. Dr.Web for Android successfully detects all known modifications of Android.BankBot.344.origin, so they do not pose any threat to our users.
#Android, #Google_Play, #banking_Trojan
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products





![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments