About 8% of Android smart TVs and devices are vulnerable to a new miner. Doctor Web describes how you can protect yourself.
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
February 8, 2018
This Android Trojan designed to mine the Monero (XMR) cryptocurrency can infect other devices without any user involvement. The Android.CoinMine.15 malware infects Android devices with an open port 5555, which is used by the interface of the Android Debug Bridge (ADB). Not only smart TVs, but smart phones, tablets, set-top boxes, routers, media players and receivers can be infected, i.e. all devices that use network debugging. The single-board computer Raspberry Pi 3 with Android is another vulnerable device.
The Trojan is distributed in the following way: the droidbot.apk application along with the files nohup, sss and bot.dat are installed on a compromised host using another infected device. The sss file is then run using the nohup utility. During its operation the file acts as a daemon. Following that, it extracts other Trojan components from bot.dat, including a JSON configuration file, miner applications (for 32-bit and 64-bit OS versions) and a copy of the droidbot Trojan program. Once launched, droidbot generates a random IP address and tries to connect to the port 5555 in an infinite loop. If successful, the Trojan attempts to infect the detected device using the ADB debugger’s interface. In a separate thread, Android.CoinMine.15 launches a miner application designed to mine the Monero (XMR) cryptocurrency. Infection by such malicious programs may lead to a significant reduction in the device performance, overheating and rapid battery draining.
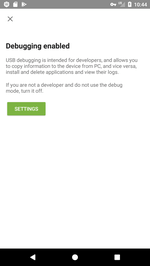
The ADB debugger is disabled by default in Android. However, some vendors enable it anyway. Additionally, ADB can by enabled by a user purposefully. Developers often use the debugging mode. According to statistics collected by Dr.Web for Android, the Android Debug Bridge is enabled on 8% of devices protected by our antivirus. As long as this setting poses a potential threat, Security Auditor, a special Dr.Web component, warns users that the debugger is enabled and offers to disable it.
Dr.Web specialists recommend all users of Android devices scan their operation systems for riskware. To do so, you can purchase Dr.Web Security Space for Android with Security Auditor on our website or on Google Play. If USB debugging is not used on your device, it is better to disable it. Dr.Web for Android products successfully detect and remove Android.CoinMine.15; and, therefore, this malicious program poses no threat to Dr.Web users.
#Android #mining #cryptocurrencies
Your Android needs protection!
Use Dr.Web
- First version of Dr.Web for Android released
- Over 135 million downloads—just from Google Play!
- Available free of charge for users who purchase Dr.Web home products