Mobile malware review for 2017
December 29, 2017
Information security events of the past year showed that cybercriminals’ interest in mobile devices still persists. The evidence is both an emergence of new malicious Android programs and an extension of their functionality. During the past year, owners of smartphones and tablets were under the threat of Trojans that use the Android Accessibility Service. With the help of the Accessibility Service, they covertly performed malicious actions. For example, they changed system settings and covertly downloaded and installed software.
Banking Trojans were again a serious threat that stole login credentials and other sensitive information and helped cybercriminals steal money from victims’ accounts. In 2016, the source codes of one of the Android bankers were made public. This simplified the process for creating new malicious applications of such type for virus writers.
The problem with Android ransomware still persists. These Trojans block mobile devices and demand a ransom to restore operability. In 2017, among these malicious programs were also coders that encrypted files.
It is also well worth mentioning the emergence of numerous new threats on Google Play. Among them were both Trojan and unwanted programs.
In 2017, one of the most wide-spread malicious applications were ones that opened websites to inflate their popularity, followed links and clicked on advertising banners. New Trojans for mining cryptocurrency were also detected..
Principal trends of the year
- An emergence of Trojans using the Android Accessibility Service
- The detection of a large amount of malicious and unwanted programs on Google Play
- The emergence of new banking Trojans
- The spreading of malicious applications that loaded websites to inflate their popularity, followed links and clicked on advertising banners
- The detection of new Trojans that mined cryptocurrency using computing powers of infected mobile devices
Most remarkable events
In 2017, malicious programs that used Android Accessibility Service became widespread. Functions of this mode simplify the use of smartphones and tablets for people with reduced capabilities. However, when Trojans obtained access to such functions, it would actually fully control an infected device and perform malicious actions without the owner’s intervention. For example, it could simulate tapping in dialogs, open and change various settings, and automatically install other applications.
One of such Trojans was Android.BankBot.211.origin. Once the required privileges were gained, it independently added itself to a list of device administrators, assigned itself an SMS manager by default and could record everything that happened on a device’s screen. Android.BankBot.211.origin displayed fake authorization forms once banking and other programs were launched, made screenshots on every tap on a keyboard, and sent cybercriminals information about all SMS messages and phone calls.
Android.DownLoader.504.origin is one more Trojan that used Android Accessibility Service to automatically execute malicious actions. It covertly downloaded various applications and also other Trojans, then independently installed them.
Additionally, in the past year Android.BankBot.233.origin was detected. It had similar functions. It used its own sources and the Accessibility Service to covertly install a banking Trojan Android.BankBot.234.origin. It tracked the launch of Play Market and displayed a phishing form of a payment service setting on top of it with a request to input bank card information. Android.BankBot.234.origin sent the obtained data to virus writers that could use it to steal money from a victim’s account.
Cybercriminals use most of the malicious and unwanted Android programs to generate income. Along with stealing money using banking Trojans, another popular source of illegal income for cybercriminals is covertly downloading and installing applications on mobile devices. In 2016, Doctor Web specialists noted the emergence and wide distribution of Trojans and unwanted programs created for this purpose. In 2017 this trend persisted. In January, Doctor Web reported on Android.Skyfin.1.origin which injected itself into the Play Market process and downloaded applications from Google Play on its behalf. Android.Skyfin.1.origin did not install the downloaded software but fully simulated its installation by replacing various parameters when sending requests to Google server and tricking it. As a result, the Trojan artificially increased the number of installs and inflated the popularity of programs. It could independently leave fake reviews boosting application ratings and making them more appealing for users.
In May, Android.RemoteCode.28 was detected on Google Play. It also downloaded other programs from the Internet. In July, Doctor Web security researchers detected Android.Triada.231. Cybercriminals injected it into an Android system library and inserted it into the firmware of several mobile device models. Android.Triada.231 injected itself into the processes of all programs and could covertly launch additional malicious modules.
Another wide-spread method of cybercriminals for gaining profit is loading websites for generating traffic, and also clicking on banners and other elements on those websites. One of the malicious programs used by cybercriminals for this purpose in 2017 was Android.RemoteCode.106.origin distributed via Google Play. It downloaded auxiliary modules and used them to open websites. Then it followed links located on these websites and clicked on ads.
A similar functionality had a Trojan family Android.Click detected in 2017. For example, according to a command and control server’s orders, Android.Click.132.origin covertly loaded webpages and automatically clicked on their advertising banners. Android.Click.268, Android.Click.269 and Android.Click.274 also opened webpages and clicked on areas indicated by cybercriminals, which boosted ad click-throughs. They receive website addresses for sending 10 million empty requests from the control center. As a result, users who installed these Trojans unwillingly became participants of DDoS attacks.
The display of aggressive advertising is still a popular source of income for virus writers and unfair software developers. In March 2017, Doctor Web published an article about an unwanted advertising module dubbed Adware.Cootek.1.origin. It was embedded in a benign keyboard application called TouchPal and distributed via Google Play. More than 50 million users installed this program. Adware.Cootek.1.origin displayed obnoxious ads and even embedded banners in a lock screen.
In April, Android.MobiDash.44 was detected on Google Play. It was distributed as a manual to popular games. It displayed advertisements and could also download additional malicious modules.
Cryptocurrency mining with the use of mobile devices cannot be qualified as an effective source of profit. Nevertheless, this method of wealth accumulation still attracts cybercriminals. In November 2017, Android.CoinMine.3 was detected on Google Play. This malicious program covertly downloaded a website with an embedded script that mined the Monero cryptocurrency.
However, criminals use malicious programs not only to generate income. Some Trojans are also used for tracking and cyber espionage. Thus, in April 2017, information about Android.Chrysaor.1.origin and Android.Chrysaor.2.origin was published. These Trojans were involved in targeted attacks. They stole correspondence from numerous messaging programs, such as Skype, Viber, WhatsApp, Twitter, Facebook, mail clients, etc. They also intercepted SMS messages and performed tap-ins via the microphone of an infected smartphone or tablet, and recorded phone calls. These Trojans tracked the location of mobile devices, stole browser history, sent cybercriminals information on contact list and collected confidential data.
In July, one more similar Trojan dubbed Android.Lipizzan.2 was detected. It also stole correspondence from popular messengers and mail clients, intercepted and recorded phone calls, made recordings using a microphone, took screenshots and tracked the location of an infected device.
Additionally, in 2017 Doctor Web detected Android.Spy.377.origin, which spied on Iranian users. Cybercriminals controlled it with commands sent via the message-exchange protocol of the Telegram online messenger. Android.Spy.377.origin sent cybercriminals information about all files available on a device and could upload any of them to the command and control server. Upon the command of cybercriminals, the Trojan sent SMS messages, made phone calls, tracked the coordinates of an infected smartphone or tablet, stole all incoming and outgoing SMS messages, and other confidential information.
Mobile malware landscape
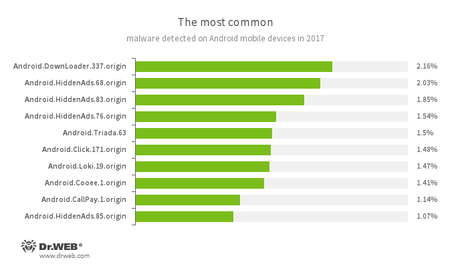
According to Dr. Web’s detection statistics for Android products, Trojans on Android devices that independently downloaded other malicious programs and unwanted software were most often encountered in 2017. In addition, a substantial share of detected threats was adware.
- Android.DownLoader.337.origin
- The Trojan that downloads applications indicated by virus writers.
- Android.HiddenAds
- Representatives of a Trojan family designed to display unwanted ads.
- Android.Triada.63
- A multi-functional Trojan that performs different malicious actions.
- Android.Click.171.origin
- A Trojan designed to inflate traffic numbers on websites specified by cybercriminals.
- Android.Loki.19.origin
- A malicious program designed to download other Trojans.
- Android.Cooee.1.origin
- A Trojan that covertly downloads and installs applications and displays advertisements.
- Android.CallPay.1.origin
- A Trojan that provides access to adult content while covertly making phone calls to premium numbers as payment for this service.
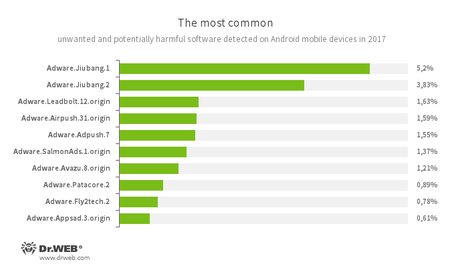
When it comes to unwanted programs and riskware that were detected on smartphones and tablets in 2017, the trend is similar to 2016. In the past 12 months, Android devices were most frequently infected with unwanted program modules that displayed ads.
- Adware.Jiubang.1
- Adware.Jiubang.2
- Adware.Leadbolt.12.origin
- Adware.Airpush.31.origin
- Adware.Adpush.7
- Adware.SalmonAds.1.origin
- Adware.Avazu.8.origin
- Adware.Patacore.2
- Adware.Fly2tech.2
- Adware.Appsad.3.origin
They were unwanted modules that software developers and virus writers had injected into applications to display aggressive advertising.
Banking Trojans
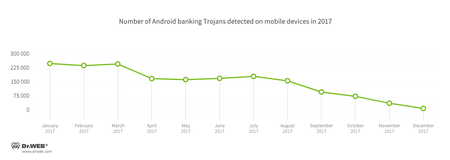
Banking Trojans are among the most dangerous malicious applications because they help cybercriminals steal money. During 2017, Android bankers penetrated mobile devices more than 1,900,000 times. This is 9.5% less than a year before. The detection dynamics of these malicious programs for these past 12 months is shown in the following figure:
A notable event of the past year was the spreading of Android bankers created on the basis of a published source code of Android.BankBot.149.origin. Among them was Android.BankBot.179.origin detected on Google Play in April. This Trojan displayed fake input forms for login credentials upon the launch of more than 200 banking programs. As a result, owners of infected smartphones and tablets did not know they had seen a fake window and input their sensitive information, which was then sent to cybercriminals. Android.BankBot.179.origin intercepted all SMS messages with verification codes from credit organizations and automatically validated the transfer of money to cybercriminals’ accounts.
Other Trojans created on the basis of published source codes were dubbed Android.BankBot.160.origin and Android.BankBot.163.origin. They were embedded into applications for displaying weather forecasts and also distributed via Google Play. These malicious programs tracked the launch of banking applications and displayed fake authorization windows upon their opening.
Among other Android bankers that attacked mobile device users in 2017 was Android.Banker.202.origin. It was hidden in benign programs and distributed via Google Play. Once launched, Android.Banker.202.origin extracted from its file sources and launched Android.Banker.1426. The latter was downloaded from the command and control server on one of the Android bankers from the Android.BankBot family, which stole login credentials and other confidential information.
Ransomware Trojans
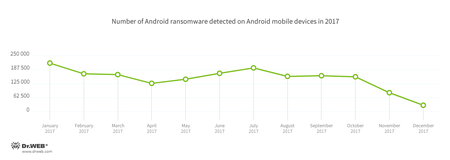
Ransomware poses a serious danger. They block mobile devices and even encrypt their files, and then demand a ransom. In 2017, Android smartphone and tablet owners faced similar lockers again. During the past 12 months, Dr.Web anti-virus products for Android detected these Trojans over 177,000 times. The detection dynamics of Android ransomware is illustrated in the following graph:
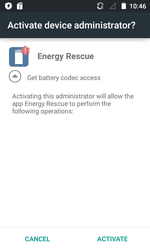
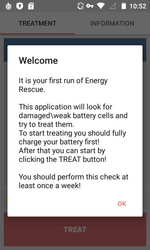
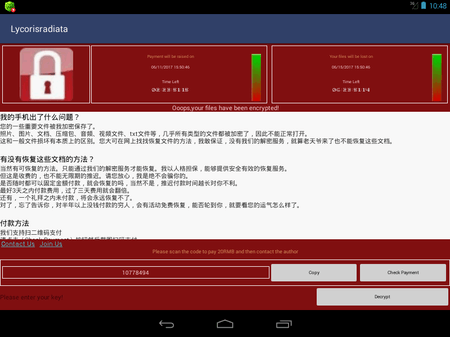
One of these Trojans was detected on Google play and dubbed Android.Locker.387.origin. It was hidden in an application called Energy Rescue, which supposedly restored some damaged and weak accumulator cells. In reality, Android.Locker.387.origin could not perform the promised procedure and just simulated the activity. Instead of battery restoration, it blocked the screen of an infected device. This action required a request for administrator privileges. It then demanded a ransom.
In June, the ransomware Trojan Android.Encoder.3.origin became well-known. It attacked Chinese Android users and encrypted files on SD cards. It is interesting because its window with ransom demands was created in the same sensational style of WannaCry, which infected hundreds of thousands of computers throughout the world in May 2017.
In late summer, a signature of Android.Banker.184.origin was added to the Dr.Web virus database. It requested access to the Accessibility Service, independently added itself to a list of administrators of an infected device, set its own PIN code for unlocking screens, and then encrypted photos, videos, documents, and other files.
Threats on Google Play
Despite Google’s attempts to provide security to the official Android application catalog, malicious and unwanted programs still persist. In 2017, many threats were detected on Google Play. In April, Android.BankBot.180.origin was detected. It was hidden in a flashlight application. It displayed fake input forms for login credentials to access bank accounts and intercepted SMS messages with verification codes.
In June, Android.Dvmap.1.origin was detected on Google Play. It used a set of exploits to gain root access and covertly installed Android.Dvmap.2.origin. This module connected to the command and control server and upon its command could download additional components.
In the same month, riskware Program.PWS.1 was detected on Google Play. It provided access to the “VK” and “Odnoklassniki” websites, which are blocked in Ukraine. This application used an anonymizing server to bypass restrictions. However, it did not encrypt sent login credentials and other information that resulted from work in social networks. It posed a threat to the confidentiality of mobile device owners.
Later, Trojans such as Android.SmsSend.1907.origin and Android.SmsSend.1908.origin were detected on Google Play. They sent SMS to premium numbers and subscribed users to expensive services.
In July, Doctor Web reported on Android.DownLoader.558.origin. It was embedded into a special program platform applied for software development (SDK, Software Development Kit), which was used for optimizing and simplifying application updates. Android.DownLoader.558.origin could covertly download and launch additional modules. In the same month, Android.RemoteCode.85.origin was detected on Google Play. This Trojan downloaded and launched a malicious component that sent cybercriminals users’ SMS messages.
In September, Android.SockBot.5 was detected on Google Play. It used an infected device as a proxy server implemented via the SOCKS protocol. And in November, Android.DownLoader.658.origin was detected in the catalog. It offered different applications for download and installation.
In the course of the year, new modifications of Android.Spy.308.origin were detected on Google Play. Doctor Web reported them in 2016. As before, the malicious program was injected into benign software. The main function of Android.Spy.308.origin is to display annoying ads, and download and launch additional modules.
Prospects and trends
Cybercriminals continually improve mechanisms for spreading malicious programs and their functional possibilities. One of the main threats to Android mobile device users are banking Trojans. In 2016, Doctor Web specialists noted that a growing number of these malicious applications for stealing confidential information track the launch of banking clients and display on top of them phishing forms for inputting personal data. In 2017 this trend persisted. It can be said without doubt that next year cybercriminals will follow the indicated attack vector and create new bankers.
Trojans use the Android Accessibility Service, which significantly extended the functionality of malicious programs and made them more dangerous because these privileges actually grant them full control over infected devices. The threat to owners of smartphones and tablets is so serious that Google decided to significantly limit the use of these functions in programs distributed via Google Play. If applications are not designed to assist people with reduced capabilities, they can be removed from the official catalog. Developers must prove that their software truly needs the indicated functions, and explain to users exactly why these functions are required. Without any doubts, virus writers will find a way to bypass the restrictions and will continue to spread Trojans with this functionality.
Another possible trend in 2018 is the improvement of measures for detecting Trojans with more sophisticated analysis. More often cybercriminals use multi-stage malicious programs when the main functionality is hidden in loadable modules, and auxiliary Trojan applications are located on command and control servers. All kinds of packers became widely spread. Most likely, virus writers will further apply these and other methods for protecting malicious programs.
More cases of infected mobile device firmware are also expected in 2018. More ransomware will emerge, including Trojans that encrypt user files.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products