Doctor Web warns of website hacking using the “Internet of things”
Real-time threat news | Hot news | All the news | Virus alerts
December 7, 2017
Linux.ProxyM is a malicious program for Linux which launches a SOCKS proxy server on an infected device. Cybercriminals can use it to anonymously perform destructive actions. The known assembly of this Trojan exists for devices possessing the following architectures: x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC. It means Linux.ProxyM can infect almost any Linux device, including routers, set-top boxes, and other similar equipment.
In September, Doctor Web security researchers learned cybercriminals used Linux.ProxyM to send over 400 spam messages per day from each infected device. Emails advertised adult content resources and questionable financial services. Soon cybercriminals began using the “Internet of things” to distribute phishing messages. The emails were supposedly sent on behalf of DocuSign—a service that allows users to download, view, sign and track the status of electronic documents.
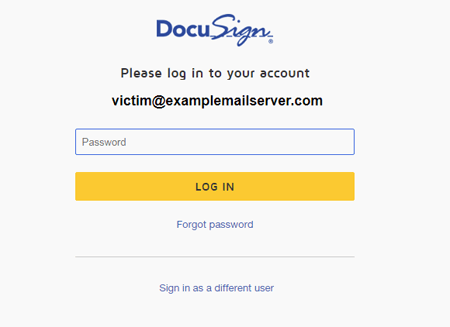
If a user followed a link in an email, they would land on a fake DocuSign website with an authorization form. After entering a password, a victim would be redirected to the real DocuSign authorization page, and the contents of the phishing form were then sent to the cybercriminals.
In December, cybercriminals found another use for devices infected with Linux.ProxyM: they used the Trojan’s proxy server to preserve anonymity and made numerous attempts at hacking websites. Cybercriminals use various hacking methods. They are SQL injections (an injection of a malicious SQL code into a request to a website database), XSS (Cross-Site Scripting)—an attack method that involves adding a malicious script to a webpage, which is then executed on a computer when this page is opened, and Local File Inclusion (LFI). This kind of attack allows attackers to remotely read files on an attacked server using specially crafted commands. Among the attacked websites were game severs, forums and resources on other topics, including Russian websites.
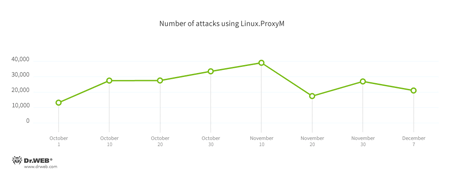
Doctor Web security analysts continue to monitor the Linux.ProxyM botnet activity. The chart with the number of registered Trojan attacks is presented below.
Although Linux.ProxyM has only one function—a proxy server—cybercriminals continue finding new opportunities to use it for illegal actions and showing increasing interest in the “Internet of things”.