Doctor Web’s November 2017 virus activity review
November 30, 2017
In November, Doctor Web specialists analyzed a new representative of the Trojan.Gozi banking Trojan family. Unlike its predecessors, the new Trojan completely consists of a set of modules and no longer possesses the mechanism needed to generate control server domain names. Server addresses are now hard-coded into the malware program’s configuration.
Also in November, a new backdoor for Linux and several fraudulent websites were found. Cybercriminals used these websites to fleece money from Internet users on behalf of a nonexistent public fund.
PRINCIPAL TRENDS IN NOVEMBER
- The emergence of a new banking Trojan
- The distribution of a new backdoor for Linux
- The emergence of a new fraudulent Internet scheme
Threat of the month
The Gozi banking Trojan family is well known to security researchers: one of its representatives is famous for using a text file downloaded from a NASA server as a dictionary for generating control server addresses. The new version of the banking Trojan, dubbed Trojan.Gozi.64, can infect computers running 32- and 64-bit versions of Windows 7 and later. The malicious program does not run on earlier Windows versions.
Trojan.Gozi.64’s main purpose is to perform web injections, which means it can inject arbitrary content into webpages users are browsing— for example, fake authorization forms on bank websites and in online banking systems.
In addition, due to the fact that webpage modification is performed directly on an infected computer, the URL of the website involved remains intact in the browser address bar. This may prevent the user from realizing that something is amiss. Any data the user enters into a fake form is sent to cybercriminals, which results in the account of the Trojan’s victim possibly being compromised.
For more information about Trojan.Gozi.64’s functionality and its operating routines, refer to this article on our website.
According to Dr.Web Anti-virus statistics
- Trojan.DownLoader
- A family of malicious programs designed to download other malware to the compromised computer.
- Trojan.Starter.7394
- A Trojan whose main purpose is to launch in an infected system an executable file possessing a specific set of malicious functions.
- Trojan.Encoder.11432
- A multi-component network worm known as WannaCry. It can infect computers running Microsoft Windows without any user involvement. The malware encrypts files on an infected computer and demands a ransom. Test and other files are decrypted with different keys. Therefore, there is no guarantee that the data corrupted by the encoder can be restored successfully, even if a ransom is paid.
- Trojan.Zadved
- This Trojan displays fake search results in a browser window and imitates pop-up messages from social networking sites. In addition, the malware can replace advertisements displayed on different Internet resources.
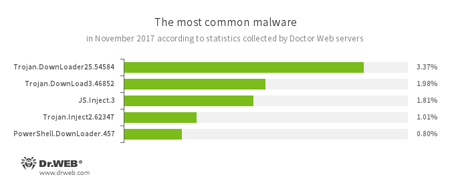
According to Doctor Web’s statistics servers
- Trojan.DownLoader25.54584, Trojan.DownLoad3.46852
- Representatives of Trojan families designed to download other malware to a compromised computer.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- Trojan.Inject
- A family of malicious programs that inject malicious code into the processes of other programs.
- PowerShell.DownLoader
- A family of malicious files written in PowerShell scripts and designed to download and install other malware programs on a computer.
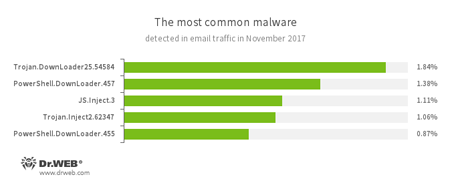
Statistics concerning malicious programs discovered in email traffic
- Trojan.DownLoader
- A family of malicious programs designed to download other malware to the compromised computer.
- PowerShell.DownLoader
- A family of malicious files written in PowerShell scripts and designed to download and install other malware programs on a computer.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- Trojan.Inject
- A family of malicious programs that inject malicious code into the processes of other programs.
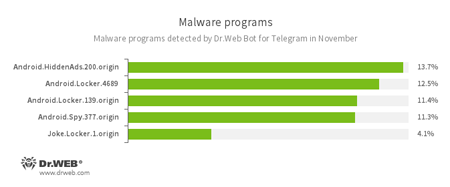
According to Dr.Web Bot for Telegram data
- Android.HiddenAds.200.origin
- A Trojan designed to display advertisements. It is distributed under the guise of popular apps by other malicious programs that in some instances covertly install it in the system directory.
- Android.Locker
- A family of ransomware Trojans for Android. They can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom.
- Android.Spy.337.origin
- A Trojan for Android that steals confidential information, including user passwords.
- Joke.Locker.1.origin
- A joke program for Android that blocks a mobile device’s screen and displays the Windows BSOD (“Blue Screen of Death”).
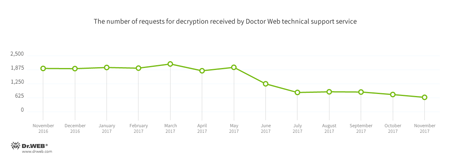
Encryption ransomware
In November, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.3953 — 17.88% of requests;
- Trojan.Encoder.858 — 8.39% of requests;
- Trojan.Encoder.11539 — 6.39% of requests;
- Trojan.Encoder.567 — 5.66% of requests;
- Trojan.Encoder.3976 — 2.37% of requests;
- Trojan.Encoder.761 — 2.37% requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During November 2017, the URLs of 331,895 non-recommended websites were added to the Dr.Web database.
| October 2017 | November 2017 | Dynamics |
|---|---|---|
| +256,429 | +331,895 | +29.4% |
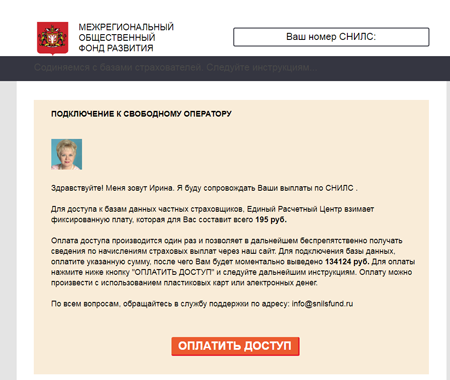
In November, Doctor Web described a new fraudulent scheme that has spread in the Russian segment of the Internet. Cybercriminals have been sending out spam with a link to a website allegedly belonging to a certain “The Interregional Social Fund of Development”. Referring to a nonexistent Decree of the Government of the Russian Federation, the cybercriminals offer to do a check for website visitors to tell them whether they are owed any payouts from various insurance companies. Visitors need to supply their personal insurance policy number (SNILS) or passport number. No matter what kind of data the victim fills in (it can be an arbitrary sequence of numbers), they receive a message telling them that they have been apportioned insurance payments for quite a large sum—several hundred rubles. However, in order to withdraw these savings, the cybercriminals demand a payment.
Virus analysts have detected many other fraudulent projects on the servers containing the webpages of “The Interregional Social Fund of Development”. For more details, please refer to the review on our website.
Linux malware
In late November, Doctor Web security researchers analyzed a new backdoor for Linux named Linux.BackDoor.Hook.1. This Trojan can download files indicated in a command it receives from cybercriminals, launch applications, or connect to a specific remote host. All the features of Linux.BackDoor.Hook.1 are described in our review.
Malicious and unwanted programs for mobile devices
In November, Doctor Web security researchers detected the Trojan Android.RemoteCode.106.origin on Google Play. This Trojan downloads additional malicious modules that load websites and tap on advertisements and links. In addition, malicious programs from the Android.SmsSend family, which send expensive messages, were found in the directory. Also in the past month, the Trojan Android.CoinMine.3 was distributed via Google Play. It used infected mobile devices to mine the Monero cryptocurrency. Furthermore, a large number of banking Trojans from the Android.Banker family were detected on Google Play. These Trojans are designed to steal private user information and money from Android user bank accounts.
The following November events related to mobile malware are the most noteworthy:
- the detection of a large number of Trojans on Google Play.
Find out more about malicious and unwanted programs for mobile devices in our special overview.