October 27, 2017
In October, yet another Android Trojan embedded into benign applications was detected on Google Play. It allowed cybercriminals to use infected mobile devices as proxy servers. In addition, in the past month a ransomware Trojan became widely known. It encrypted files on Android smartphones and tablets, changed the screen lock password, and demanded ransom.
PRINCIPAL TRENDS IN OCTOBER
- The appearance of information in the mass media about an Android Trojan that changed the PIN code of mobile screen locks and encrypted files.
- The discovery on Google Play of a malicious program that turned Android devices into proxy servers.
Mobile threat of the month
In October, the Trojan Android.SockBot.5 was detected on Google Play. It was added to the Dr.Web virus database back in June 2017. Cybercriminals incorporated it into the following applications:
- PvP skins for Minecraft
- Game Skins for Minecraft
- Military Skins for Minecraft
- Cartoon skins for Minecraft
- Hot Skins for Minecraft PE
- Skins Herobrine for Minecraft
- Skins FNAF for Minecraft
- Assassins skins for Minecraft
These programs allowed users to change the external appearance of characters in the mobile version of the popular game Minecraft.
Once launched, the Trojan covertly connected to a remote command center and then, using the SOCKS protocol, established a connection with a network address. As a result, cybercriminals turned smartphones and tablets into proxy servers and could process traffic through them.
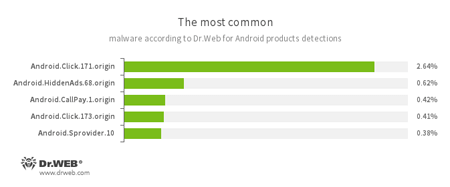
According to statistics collected by Dr.Web for Android
- Android.Click.171.origin
- Android.Click.173.origin
- Trojans that periodically request specific websites can be used to inflate their popularity and follow advertising links.
- Android.HiddenAds.68.origin
- A Trojan designed to display unwanted ads on mobile devices.
- Android.CallPay.1.origin
- A Trojan that provides access to adult content while covertly making phone calls to premium numbers as payment for this service.
- Android.Sprovider.10
- A Trojan that downloads and installs various applications on Android devices. In addition, it can display advertisements.
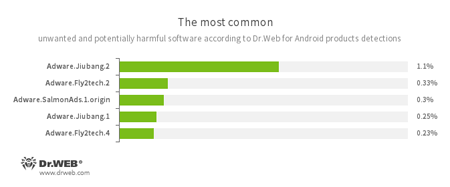
- Adware.Jiubang.2
- Adware.Fly2tech.2
- Adware.SalmonAds.1.origin
- Adware.Jiubang.1
- Adware.Fly2tech.4
- Unwanted program modules incorporated into Android applications and designed to display annoying ads on mobile devices.
A ransomware Trojan
In the past month, the mass media published information on the spread of a dangerous Android ransomware Trojan that changed the lock screen PIN codes of smartphones and tablets, encrypted user files, and demanded a ransom to make devices operational again. This malicious program was added to the Dr.Web database as Android.Banker.184.origin back in August 2017, so it poses no threat to our users.
Once launched, the Trojan attempts to gain access to the Accessibility Service, which it uses to independently add itself to the list of device administrators. Then it changes the PIN code that unlocks the screen, encrypts the user’s files (photos, videos, documents, music, etc.) and displays a message containing a ransom demand. In addition, there are versions of the malicious program that avoid encrypting files larger than 10 MB.
Despite the fact that some publications have described Android.Banker.184.origin’s functionality as being unique, other Trojans have made use of similar capabilities in the past. Back in 2014, Doctor Web detected the Android ransomware Trojan Android.Locker.38.origin, which installed its own code to unlock the device screen. That was the same year the first Android encryption Trojan emerged. It was named Android.Locker.2.origin. Performing malicious actions using the Accessibility Service (such as automatically adding a malicious application to the administrator list) has also previously been used in Android Trojans, for example in Android.BankBot.211.origin.
As before, cybercriminals are trying to spread Trojans via Google Play and continue to refine their malicious programs. Doctor Web recommends that device owners install Dr.Web for Android to protect their mobile devices from possible infection.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 100 million downloads on Google Play alone
- Free for users of Dr.Web home products