October 16, 2017
This malicious program has been added to the Dr.Web virus databases under the name Python.BackDoor.33. The Trojan contains a packed utility py2exe, which allows Python scripts to be run on Windows as ordinary executable files. The functions of this malicious program are implemented in file the mscore.pyc.
Python.BackDoor.33 saves its copy in a folder on a drive, modifies the Windows system registry to ensure its launch, and shuts down the script. Thus, the backdoor’s main malicious functions are executed after system restart.
After the computer is rebooted, the Trojan tries to infect all device’s drives with names from C to Z. For this purpose, it creates a hidden folder, saves there a copy of its executable file (also with the “hidden” attribute), after that it creates a link in the root disc directory in the form of <volume name>.lnk, which refers to the malicious executable file. All files different from .lnk, VolumeInformation.exe and .vbs are moved to the hidden folder created earlier.
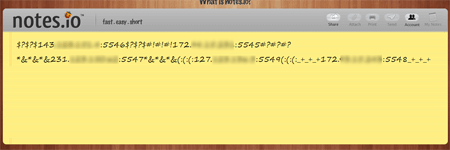
Then the Trojan attempts to define an IP address and an available port of the command and control server by sending a request to several Internet servers, including pastebin.com, docs.google.com and notes.io. The received value looks as follows:
If the backdoor was successful in obtaining the IP address and port, it sends a special request to the C&C server. If the Trojan receives a response , it will download the Python scripts added to the Dr.Web virus databases as Python.BackDoor.35 from the C&C server and run them on the infected device. This script implements functions for stealing passwords (stealer), intercepting pressed keys (keylogger), and executing remote commands (backdoor). This Trojan can also scan whatever storage media is connected to an infected device and infect them in a similar way. In particular, Python.BackDoor.35 allows cybercriminals to:
- Steal information from such browsers as Chrome, Opera, Yandex, Amigo, Torch, and Spark;
- Perform the keylogger functions and make screenshots;
- Download additional modules written in Python and execute them;
- Download files and save then on a media of the infected device;
- Obtain contents of the specified folder;
- “Travel” across folders;
- Request system information.
Among other matters, structure of Python.BackDoor.35 has a self-update function. However, it is not utilized at the moment. All the aforementioned programs have been added to the Dr.Web virus databases, and, therefore, they pose no threat to our users.
#backdoor #malicious_software #Trojan
![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments