Cybercriminals using Internet of things to send spam messages
Real-time threat news | Hot news | All the news | Virus alerts
September 12, 2017
The Trojan at issue is Linux.ProxyM, which was already described by Doctor Web in June. The company wants to remind users that this Trojan runs a SOCKS proxy server on an infected device and is capable of detecting honeypots—special resources created by those researching malicious programs to serve as decoys for cybercriminals. Once the Trojan connects to its command and control (C&C) server and receives confirmation from it, Linux.ProxyM downloads from this server the addresses of two Internet nodes: the first provides a list of logins and passwords, and the second is required for the SOCKS proxy server to operate. Two builds of this Trojan exist for devices possessing the following architectures: x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC. In other words, Linux.ProxyM can operate on almost any Linux device, including routers, set-top boxes, and other equipment.
Doctor Web virus analysts have discovered that cybercriminals are using Linux.ProxyM to send spam. A C&C server sends a command to an infected device. The command contains an SMTP server address, the login and password used to access it, a list of email addresses, and a message template of itself. These emails contain advertising for various adult-content websites. A typical email message sent using devices infected with Linux.ProxyM contains the following:
Subject: Kendra asked if you like hipster girls
A new girl is waiting to meet you.
And she is a hottie!
Go here to see if you want to date this hottie
(Copy and paste the link to your browser)
http://whi*******today.com/
check out sexy dating profiles
There are a LOT of hotties waiting to meet you if we are being honest!
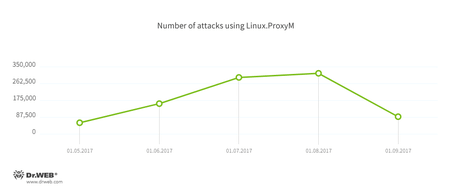
According to Doctor Web’s statistics, a device infected with Linux.ProxyM sends on average about 400 emails per day. The below chart shows how many Linux.ProxyM attacks our specialists have pinpointed.
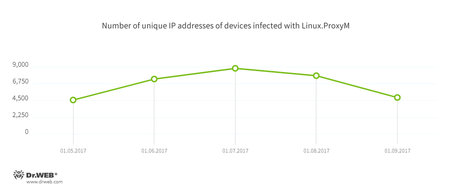
The number of unique IP addresses of infected devices is shown in the following diagram. It is worth mentioning that the figure shows only the number of bots monitored by Doctor Web analysts. The actual number of infected devices may be higher.
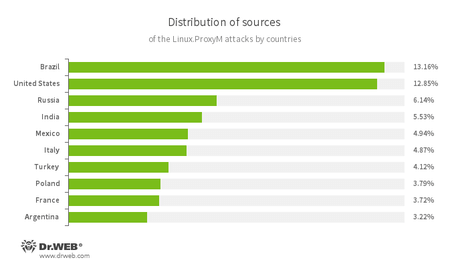
The below illustration shows the geographical locations from which Linux.ProxyM attacks have been launched during the past 30 days:
We can presume that the range of functions implemented by Linux Trojans will be expanded in the future. The Internet of things has long been a focal point for cybercriminals. The wide distribution of malicious Linux programs capable of infecting devices possessing various hardware architectures serves as proof of that.