August 31, 2017
In early August, Doctor Web detected mass mailings targeting administrators of web resources. In particular, scammers were sending letters, allegedly on behalf of the Regional Network Information Center (RU-CENTER), and, apparently, they were doing so using a database of domain administrator contact information. In these emails, the recipient was asked to place a special PHP file on the server, an action that could compromise the Internet resource. Also in August, a Trojan miner was found. Its loader code mentioned the website owned by well-known cybersecurity expert Bryan Krebs. Moreover, Linux.Hajime Trojan loader versions for devices possessing the MIPS and MIPSEL architecture were added to the Dr.Web virus database.
Principal trends in August
- Growth in the number of fraudulent mailings
- The appearance of a new Trojan miner
- The discovery of Linux.Hajime loaders for MIPS and MIPSEL
Threat of the month
Network worms of the Linux.Hajime family have been around since 2016. To distribute these worms, cybercriminals use the Telnet protocol. After selecting the login and password of an attacked device and logging on to it, the infector plugin saves the loader, which is included in the plugin and written in Assembler. Then, the loader downloads the Trojan’s main module from the attacking computer, and this module connects the infected device to the decentralized P2P botnet. Until recently, anti-viruses detected the Linux.Hajime loader only for equipment possessing the ARM architecture, but Doctor Web virus analysts have added to its virus database similarly functioning malicious applications for MIPS and MIPSEL devices.
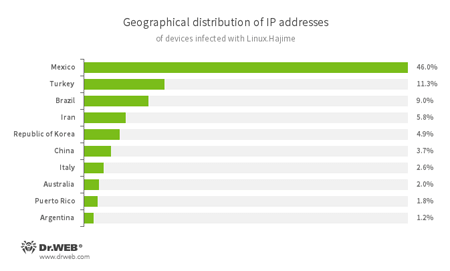
Statistics collected by Doctor Web specialists show that the majority of Linux.Hajime infection cases are registered in Mexico; Turkey ranks second, and Brazil rounds out the top three. For more details on Linux.DownLoader.506 and Linux.DownLoader.356, please refer to the article published on our website.
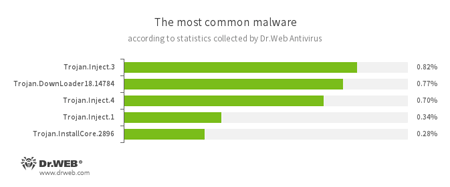
According to Dr.Web Anti-virus statistics
- Trojan.Inject
- A family of malicious programs that inject malicious code into the processes of other programs.
- Trojan.DownLoader
- A family of malicious programs designed to download other malware to the compromised computer.
- Trojan.InstallCore
- A family of installers of unwanted and malicious applications.
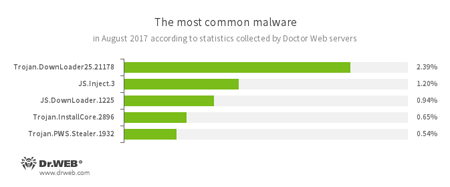
According to Doctor Web’s statistics servers
- Trojan.DownLoader
- A family of malicious programs designed to download other malware to a compromised computer.
- JS.Inject.3
- A family of malicious JavaScripts. They inject a malicious script into the HTML code of web pages.
- JS.DownLoader
- A family of malicious JavaScripts. They download and install malicious software on a computer.
- Trojan.InstallCore
- A family of installers of unwanted and malicious applications.
- Trojan.PWS.Stealer
- A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
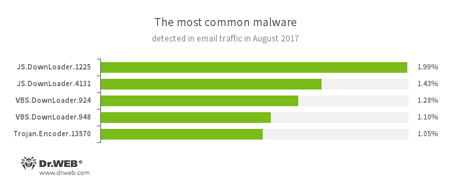
Statistics concerning malicious programs discovered in email traffic
- JS.DownLoader
- A family of malicious JavaScripts. They download and install malicious software on a computer.
- VBS.DownLoader
- A family of malicious JavaScripts. They download and install malicious software on a computer.
- Trojan.Encoder.13570
- A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom to decrypt compromised data.
Encryption ransomware
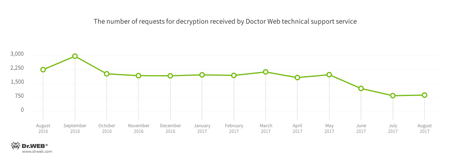
In August, cases involving the following ransomware modifications were most often registered by Doctor Web’s technical support service:
- Trojan.Encoder.858 — 29.21% of requests;
- Trojan.Encoder.567 — 4.02% of requests;
- Trojan.Encoder.761 — 1.85% of requests;
- Trojan.Encoder.11464 — 1.85% of requests;
- Trojan.Encoder.741 — 1.55% of requests
- Trojan.Encoder.3976 — 1.08% of requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During August 2017, 275,399 URLs of non-recommended websites were added to the Dr.Web database.
| July 2017 | August 2017 | Dynamics |
|---|---|---|
| + 327,295 | + 275,399 | -15.8% |
Often the list of non-recommended web resources contains websites that have been attacked by cybercriminals. These crooks publish traffic-generating scripts on compromised Internet resources and scripts that redirect users to third-party websites, and sometimes distribute malicious software in the process. When attacking websites for the purpose of compromising them, cybercriminals first collect information about the web resources they are targeting. In particular, they attempt to determine the type and version of the web server maintaining a website. They also try to identify the content management system version, the engine programming language and other technical information, including the list of subdomains of the attacked website’s main domain. If the DNS servers maintaining a website are configured correctly, cybercriminals will not be able to obtain the domain zone information they request. However, if the DNS server settings are incorrect, a special AXFR request allows cybercriminals to obtain full data on the subdomains registered in the domain zone. Having incorrect DNS server settings is not in itself a vulnerability, however, this can be an indirect cause for a web resource to become compromised. For more details, please refer to our article.
Other events in information security
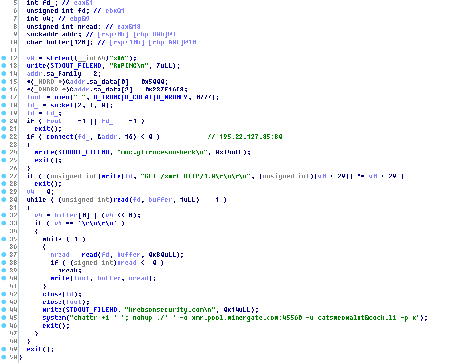
In August, Doctor Web virus analysts added to its virus database a new Trojan miner for the Linux OS, Linux.BtcMine.26. This malicious program is intended to be used to mine the Monero (XMR) cryptocurrency and is distributed similarly to Linux.Mirai. Cybercriminals connect to an attacked device using the Telnet protocol, and after selecting the login and password, they save the loader on the device. Then, using a console command, cybercriminals start the program from the terminal, and the Trojan is downloaded to the device.
The loader of the Linux.BtcMine.26 miner is distinguished by one architectural feature—in its code, the website krebsonsecurity.com is mentioned several times. This website is owned by well-known cybersecurity expert Bryan Krebs. For more details on this malicious program, please refer to our news article.
Malicious and unwanted programs for mobile devices
In the last summer month of this year, several malicious Android applications were detected on Google Play. The Android.Click.268 and Android.Click.274 Trojans, which were added to the Dr.Web virus database, performed DDoS attacks on network resources. Another Trojan, Android.Click.269, secretly loaded websites specified by attackers and clicked on banners located on those websites, generating revenue for cybercriminals. One more malicious Android program, distributed on Google Play in August, was added to the virus database as Android.BankBot.225.origin. It displayed fake input forms over banking and other launched software and stole all entered information. Also in August, the Android.MulDrop.1067 dropper, which is designed to install other Trojans, was found on Google Play.
The following events are among the most notable with regards to mobile security in August:
- The detection of Android Trojans carrying out DDoS attacks;
- The discovery of a banking Trojan on Google Play;
- The discovery on Google Play of a malicious program designed to install other Trojans.
Learn more about malicious and unwanted programs for mobile devices in our August overview.