Dr.Web: Trojan preinstalled on Android devices infects applications’ processes and downloads malicious modules
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
July 27, 2017
Trojans of Android.Triada family embed in the system process of the Zygote component, which is used to launch programs on mobile devices. By infecting Zygote, Trojans embed into processes of all running applications get their privileges and function as part of applications. Then, they secretly download and launch malicious modules.
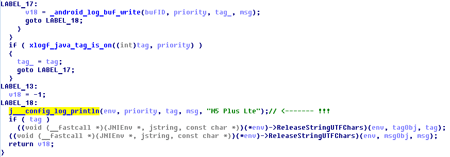
Unlike other Trojans of this family that try to get root privileges to perform malicious actions, Android.Triada.231 detected by the Dr.Web Virus Analytics is embedded into libandroid_runtime.so system library. Its modified version was found on several mobile devices, including Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20. Libandroid_runtime.so is used by all Android applications, thus the malicious code in the infected system is found in the memory of all running applications.
Android.Triada.231 is embedded into the source code of the library. It can be assumed that insiders or unscrupulous partners, who participated in creating firmware for infected mobile devices, are to be blamed for the dissemination of the Trojan.
Android.Triada.231 is embedded into libandroid_runtime.so in a way that it gets control each time when an application on the device makes a record to the system log. As Zygote is launched before other applications, the initial launch of the Trojan is performed by Zygote.
After the initialization, the malicious program sets up some parameters, creates a working directory, and checks in what environment it is running. If the Trojan is in the Dalvik environment, it intercepts one of the system methods, which allows it to track the start of all applications and perform malicious activity immediately after they start.
The main function of Android.Triada.231 is to secretly run additional malicious modules that can download other Trojan components. To run additional modules, Android.Triada.231 checks if there is a special subdirectory in the working directory previously created by the Trojan. The subdirectory name should include the MD5 value of the software package name of the application, into the process of which the Trojan is infiltrated. If Android.Triada.231 finds this directory, it seeks files 32.mmd or 64.mmd (for 32-bit and 64-bit operating systems respectively) in it. It if finds the file, the Trojan decrypts it, saves it as libcnfgp.so, then loads it into RAM using one of the system methods and deletes the decrypted file from the device. If the malicious program does not find the required object, it seeks the file 36.jmd. Android.Triada.231 decrypts the file, saves it as mms-core.jar, runs it using the class DexClassLoader and then deletes the created copy.
As a result, Android.Triada.231 can infiltrate various Trojan modules in processes of any application and affect its operation. For example, virus writers can make Trojan to download and run malicious plugins for stealing confidential information from bank applications, cyberespionage modules and for intercepting of correspondence from social media clients and messengers, etc.
Moreover, Android.Triada.231 can extract the module Android.Triada.194.origin from libandroid_runtime.so, which is stored in the library in the encrypted form. Its main function is downloading additional malicious components from the Internet, as well as ensuring their interaction with each other.
Since Android.Triada.231 is embedded into one of the libraries of the operating system and located in the system section, it cannot be deleted using standard methods. The only safe and secure method to get rid of this Trojan is to install clean Android firmware. Dr.Web specialist notified manufacturers of compromised smartphones of an existing problem, so users are advised to install all possible updates that will be released for such devices.