Doctor Web: We’ve seen these methods of infection before
Real-time threat news | Hot news | All the news | Virus alerts
June 29, 2017
The security researchers who examined Trojan.Encoder.12544 have reported that the Trojan first began spreading from an update system of the program MEDoc. This program helps Ukrainian users manage their taxes. The security researchers found that a tool named EzVit.exe, which is included in the MEDoc distribution kit and designed to update the main application, executed a CMD command at some point. This command launched the download of a malicious library. The main functionality of Trojan.Encoder.12544 is implemented in this library. Given that this encryption ransomware spreads via a network independently, using a vulnerability in the SMB protocol, and steals Windows user account data, for the infection to spread further just one machine is needed.
Back in 2012, Doctor Web security researchers detected a targeted attack on drugstores and pharmaceutical companies that involved the use of a malicious program called BackDoor.Dande. This spyware Trojan stole medication procurement information from special programs used in the pharmaceutical industry. Once launched, the backdoor checked whether the relevant procurement applications and medication purchase records were present in the system, and, if it did not find them, it would shut down. More than 2,800 drugstores and Russian pharmaceutical companies were affected. Thus, it can be stated with certainty that BackDoor.Dande was used for business espionage.
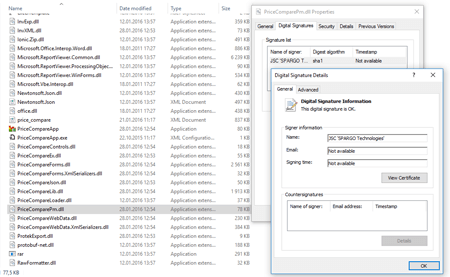
Doctor Web specialists conducted an investigation lasting four years. One of the affected companies provided its hard drives which had been compromised by BackDoor.Dande. Our analytics determined the creation date of the driver that launched all the other backdoor components. This driver was mentioned in the Windows paging file and log of the Avast anti-virus installed on the infected machine. An analysis of these files showed the malicious driver was created right after the launch of an application called ePrica (D:\ePrica\App\PriceCompareLoader.dll). This application, developed by a company called “Spargo Tekhnologii”, allows drugstore executives to analyze medication prices and choose the best supplier. This examination of ePrica allowed Doctor Web’s specialists to determine that the program loads a library into the system, and that library covertly downloads, decrypts, and launches BackDoor.Dande. The Trojan was downloaded from http://ws.eprica.ru. This website belonged to “Spargo Tekhnologii” and was designed to update ePrica. In addition, the module that covertly downloaded the malicious program had the valid digital signature “Spargo”. The Trojan loaded stolen data to servers located outside Russia. In other words, just like Trojan.Encoder.12544, the backdoor was “hidden” in the program’s update module.
The similarity of these two cases shows that the software development infrastructure requires a heightened level of awareness in terms of information security. Above all, the update process for any commercial software should be closely scrutinized by both users and the developers themselves. Some update tools of different programs have the right to install and launch executable files in an operating system. This can be an unexpected source of infection. In the case of MEDoc, the infection was caused by cybercriminals hacking into and compromising an update server. In the case of BackDoor.Dande, specialists believe the deliberate actions of insiders caused the infection to spread. This method could be used by cybercriminals to conduct an effective aimed attack on users of practically any software.