Doctor Web: Android Trojan controlled via Telegram spies on Iranian users
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
June 19, 2017
The Trojan, named Android.Spy.377.origin, is a remote administration tool (RAT) that is distributed under the guise of benign applications. It has been attacking Iranian users. The utility can be installed on smartphones and tablets as a program named “ینستا پلاس” (“Insta Plus”), “پروفایل چکر” (“Profile Checker”), and “Cleaner Pro”.
Once launched, the Trojan offers to check how popular the mobile device owner is among other Telegram users. To do that, it asks the owner for their personal ID. After the victim inputs any information in the corresponding form, Android.Spy.377.origin displays the “number of visitors” to their profile. However, in reality the Trojan doesn’t perform any check. It only generates an arbitrary number, which is presented as a true result. This function serves to clear the malicious program of suspicion and to give the impression that it poses no threat. Sometime after its launch, Android.Spy.377.origin removes its shortcut from the device home screen and shuts its window in an attempt to hide its presence in the system.
Android.Spy.377.origin is a classic spyware program capable of executing cybercriminals’ commands. The main thing that distinguishes this malicious application from other Android Trojans is in the way cybercriminals control it: via the message-exchange protocol of the Telegram online messenger. This is the first Android Trojan Doctor Web security researchers have come across that has this feature.
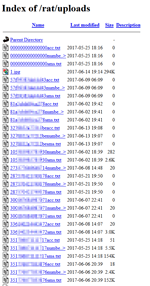
After removing the shortcut, Android.Spy.377.origin copies the contact list, incoming and outgoing SMS messages, and Google account data of the mobile device owner. Then it saves this data to text files in its working directory. In addition, the Trojan takes a photo with the front camera to capture the owner’s face. Then the spyware loads this photo and files with the stolen data to the command and control server and sends a signal to the cybercriminals’ Telegram bot indicating that the device has been infected successfully.
Below are examples of files that have been transmitted by Android.Spy.377.origin to cybercriminals.
Once the confidential information is stolen, Android.Spy.377.origin reconnects to the bot and waits for the bot to send messages containing control commands. The Trojan can receive the following orders:
- call — make a phone call;
- sendmsg — send an SMS;
- getapps — forward information about the installed applications to the server;
- getfiles — forward information about all the available files to the server;
- getloc — forward device location information to the server;
- upload — upload to the server the file that is indicated in a command and stored on the device;
- removeA — delete from the device the file specified in a command;
- removeB — delete a file group;
- lstmsg — forward to the server the file containing information about all the sent and received SMS, including sender and recipient phone numbers, and message contents.
When each command is executed, the malicious program reports this information back to the cybercriminals’ Telegram bot.
Besides collecting confidential data when commanded to do so by cybercriminals, Android.Spy.377.origin independently tracks all incoming and outgoing SMS as well as device coordinates. The Trojan alerts the cybercriminals’ Telegram bot whenever new messages are received or sent or the infected smartphone or tablet’s location changes.
Doctor Web security researchers are warning users that cybercriminals often distribute malicious applications under the guise of benign programs. To protect their devices from Android Trojans, users should install software distributed only by reliable developers and download it from such dependable sources as Google Play. All known versions of Android.Spy.377.origin are successfully detected by Dr.Web for Android anti-virus products; therefore, this spyware does not pose any threat to our users.